All across the internet we find guides and tutorials on how to keep your WordPress site secure, and they all approach the concept of user roles, but not many actually approach the capabilities of those roles.
The way the capabilities are handled on WordPress make it quite easy to change what each role is allowed to do.
How WordPress Sets Role Capabilities
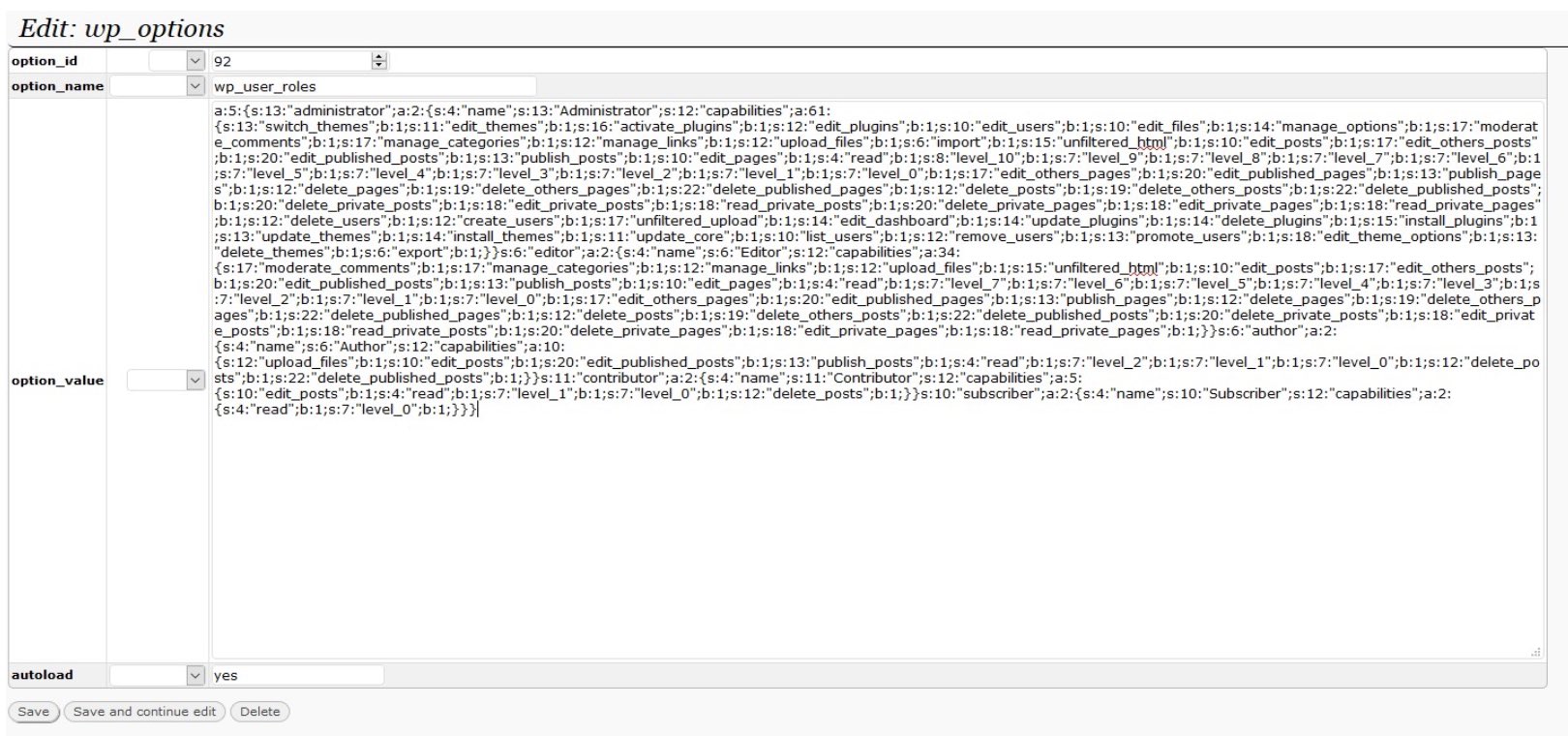
To better understand, we need to first look at how WordPress manages the capabilities of the roles (what it is allowed to do, be it either add/remove users, create/delete posts, etc...). This is defined on the database, in the wp_options table option_name - wp_user_roles
The Risk
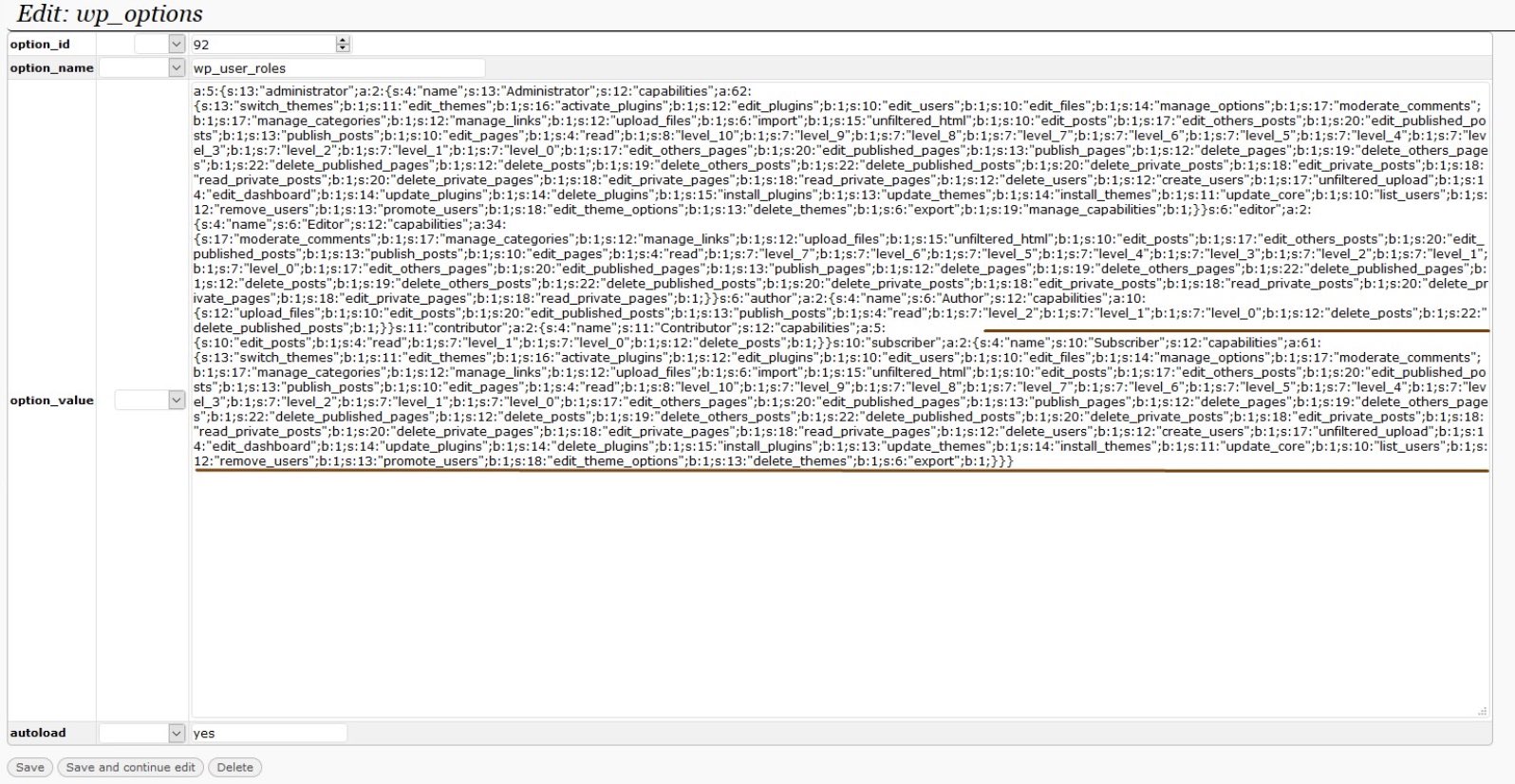
As we previously experienced, attackers are focusing on modifying serialized data within the wp_options table.Due to the feeling that webmasters understand the role “Subscriber” can’t do much about this becomes a serious problem attackers can leverage by simply modifying the wp_user_roles field on the wp_options table (see below):
(Note: The attackers first need to either compromise your website or gain database access in order to accomplish this.)
Attackers can quite easily give every subscriber full administration capabilities. Allow me to show you by using the plugin Capability Manager Enhanced
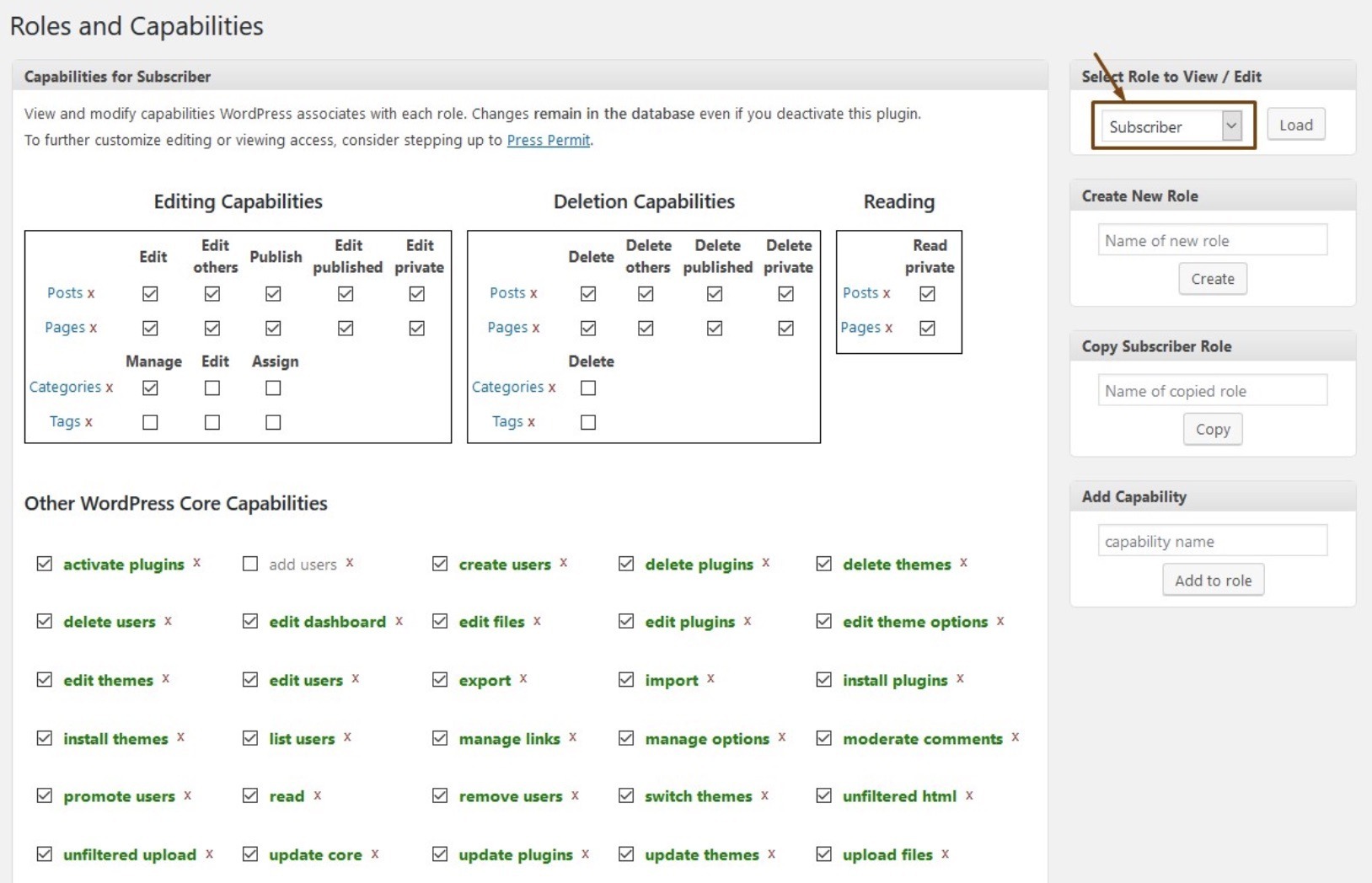
Any subscriber would be able to do pretty much whatever they wanted without you noticing because the list of users would still list the same number of administrators and subscribers.

The only problem with this is that “Subscriber” is a full administrator.
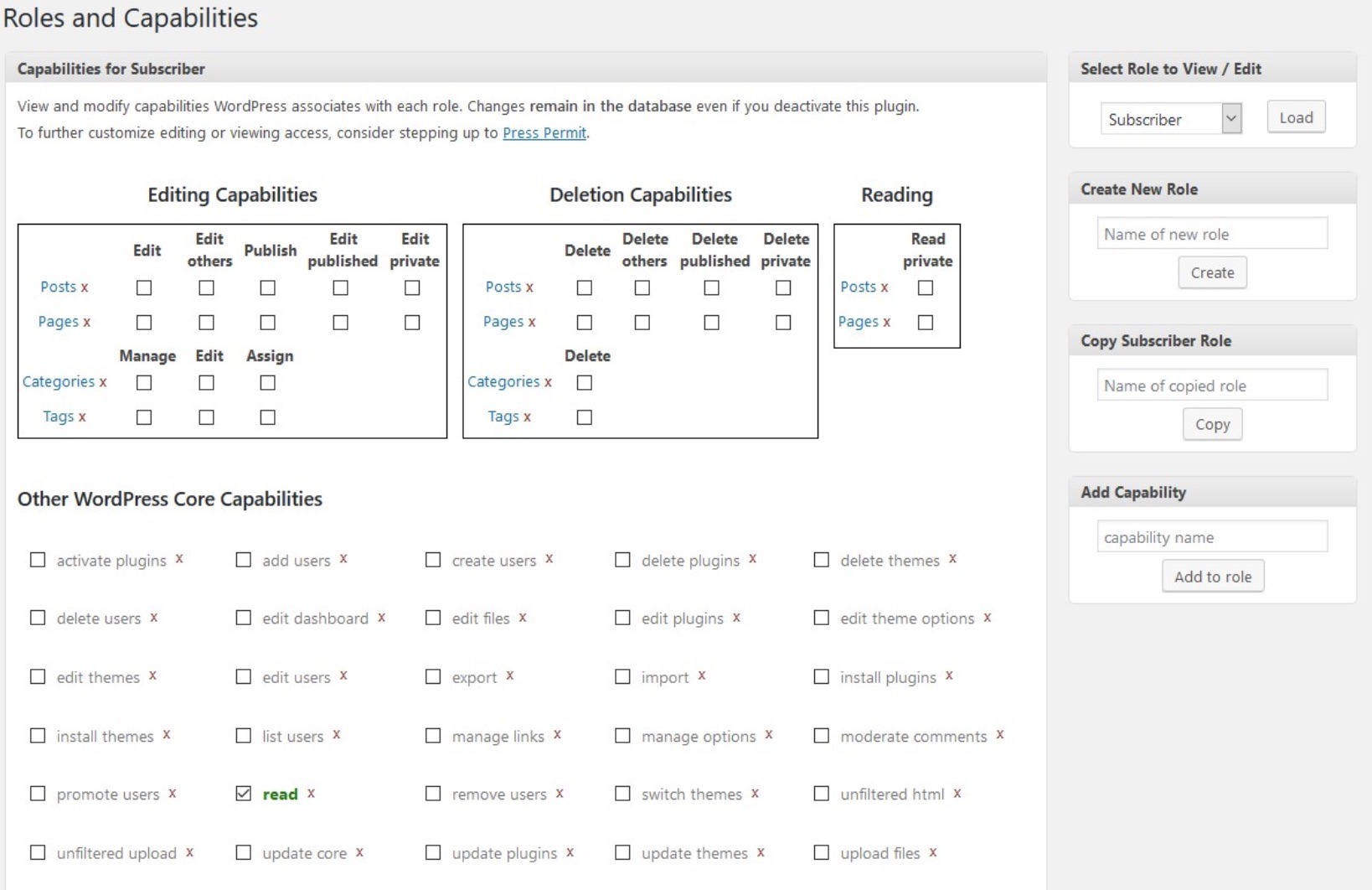
If we compare it with how it is supposed to look under the default role settings, we can see how damaging the small change can be for the website.
Conclusion
What if instead of just one subscriber, there were hundreds, even thousands? What if it was a shop and all your customers were now basically administrators?
WordPress does not have a mechanism to warn a Webmaster if roles other than the “Administrator” has those capabilities.Seeing as this can be set on any role present on your website, it’s very important to keep a sharp eye on the capabilities of each role (especially post-compromise) as it can be easily used as a backdoor to your website. Usage of plugins that manage the capabilities can make this easier for webmasters without technical know-how.