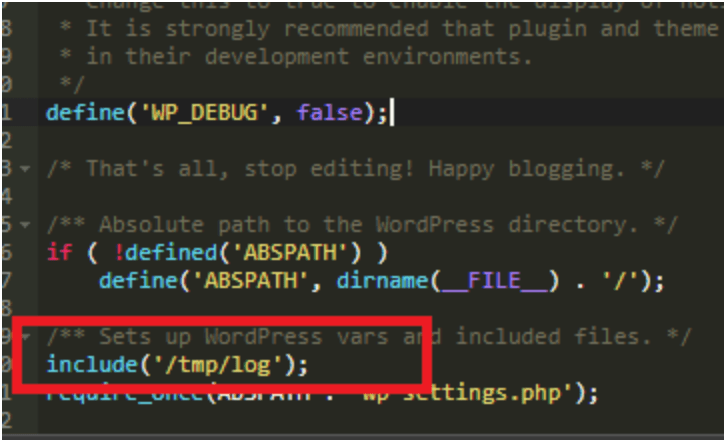
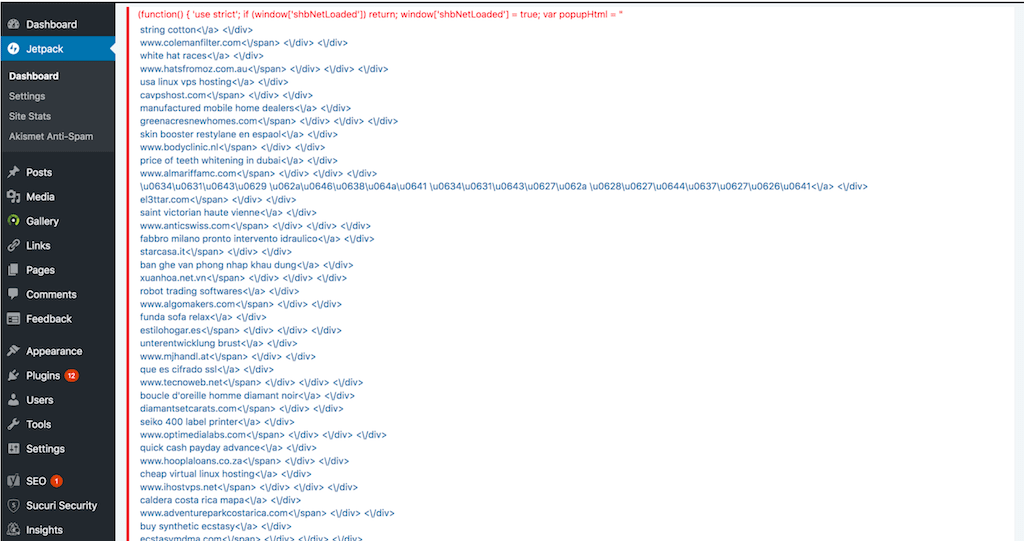
We recently cleaned a site where we found thousands of malicious files with the following content:
<?php
header ( "HTTP/1.1 301 Moved Permanently" ) ;
header ( "Location: hxxp://realprofit[.]su/" ) ;
?>and
<?php
header ( "HTTP/1.1 301 Moved Permanently" ) ;
header ( "Location: hxxp://profitnow[.]su/" ) ;
?>All files were located in the site root directory and had names derived from a person's first names: mccarphy.php, viva.php, lotta.php, sang.php, trine.php, liviu.php, taylar.php, golden.php, staphane, stanislav.php, ismail.php, jerusha.php, menda.php, niel.php, samaira.php, kaa.php, franky.php etc.
Most likely these files are used in an email malware campaign. We found an analysis of one malicious .doc file that made requests to several domains, including realprofit[.]su, and then saved the response as an .exe file and executed it.
This particular wave of the attack is known to infect many sites. Profitnow[.]su was created on November 28, 2018, and according to RiskIQ, 700+ sites redirected there. Realprofit[.]su was created on December 6, 2018, and 500+ sites redirected there.
Some other domains used in this malware campaign:
out36.selfsend.ru
to5.topwenches[.]com
trybestsale[.]su
onlinehotprice[.]su
saleallshop[.]su
bestshopmaster[.]su