There are many different tricks hackers use to make injected spam links invisible to regular visitors.
Below is an example employed by one link spam campaign, which primarily promotes porn, torrents, and pharma.
We’re finding links like these inside various HTML tags with short, random ids:
<span id="4CN8d"><a href="hxxps://youjizz[.]center">teen girls</a> busty ebony chick.</span>
….
<section id="Xwy2w"><a href="hxxps://youjizz[.]center" title="hot teens">hxxps://youjizz[.]center</a><br>
<a href="hxxps://www.thefappeninggirls[.]com">fappening 2020</a> alexa gets her cumshot.<br></section>
….
<span id="hgPdT">
<a href="hxxp://yourbunny[.]mobi/">hxxp://yourbunny[.]mobi/</a> <br/>
<a href="hxxp://lime-torrents[.]org">hxxp://lime-torrents[.]org</a> <br/>
<a href="hxxp://kickasstorrente[.]net" rel="nofollow">kickass</a>
</span>To hide the links, hackers injects scripts with misleading code.
For example, the following snippet tries to set the size of the spam link element to something entirely fictitious: size_for("Opera")
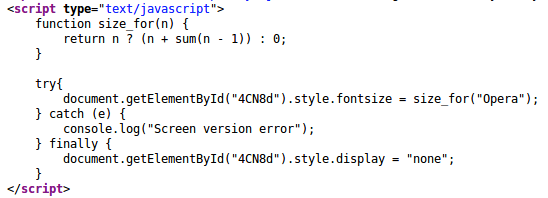
Code that hides the links
It even contains a function that counts the size. However, not only is the code unrelated to the Opera browser, it’s also erroneous because of the use of the undefined “sum” function.
This error is there “by design”. The code that invokes the size_for function is placed in the try...catch...finally block. No matter what happens in these try and catch blocks, it will always fall back to the finally section, which sets the “display” style of the element to “none”.
In another wave of link injections, this same campaign uses a combination of the following two scripts:
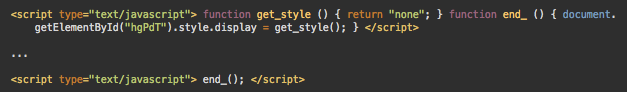
Two-piece spam hiding script
The first script defines the function end_(), which uses a misleadingly named function get_style() to hide the spam element. The second script is injected further in the HTML code to invoke the end_() function and conceal the spam.
At the time of writing, PublicWWW shows over a thousand websites with injected links from this campaign:
- getstyle/end - 1240 sites
- size_for("Opera”) - 469 sites