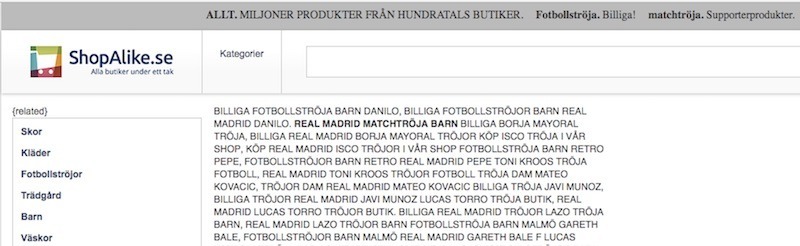
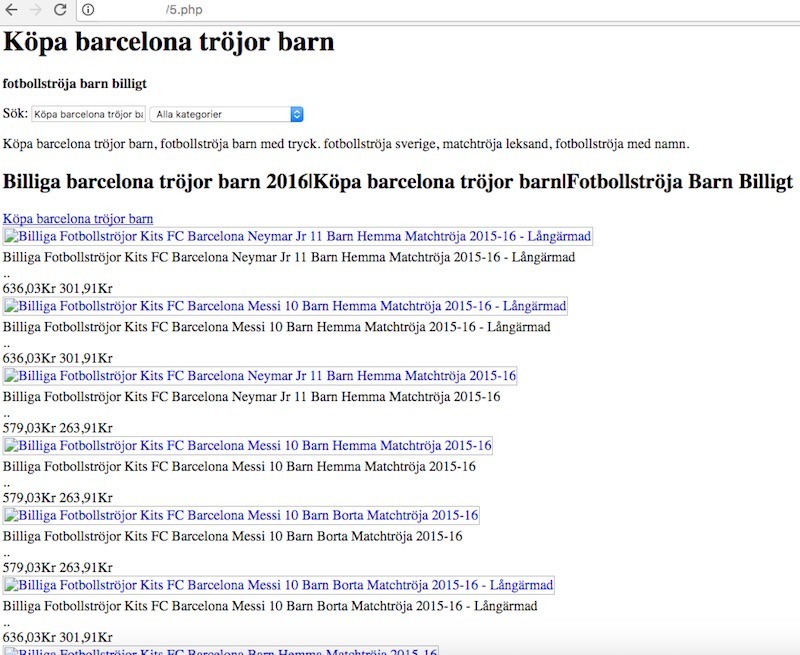
We already discussed in our blog some cases where the attacker uploaded a full ready-to-use website in order to promote their products and services. This is a well-known SEO spam tactic, but this time we're going to cover what we found in a recent incident response process. A full library was injected into the victim's file structure, of course without the consent of the website owner.
First of all, it's worth mentioning that the affected website was running a very old and vulnerable WordPress version, allowing the attacker to easily exploit it and do his dirty work. This is a reminder to always keep your software updated to prevent infections (or reinfections) from happening to your website.
The attacker uploaded a directory, whose name was "libarry" (misspelled), into the website root. That folder contained all the files for the online library, which would look like this:
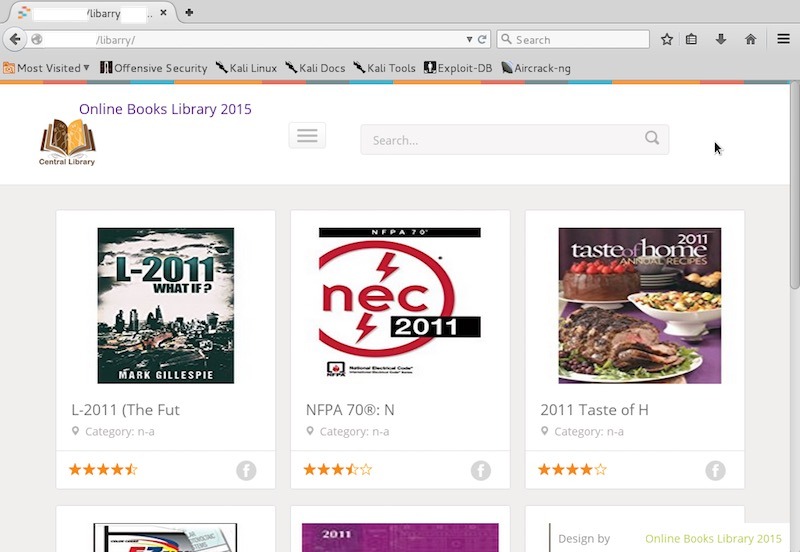
Another interesting thing to note is that they even used the victim's website name as the online library name to make it more legit (the website name was suppressed in the screenshot and in the code block below). This is possible because of the configuration settings located at ./libarry/setting.php:
<?PHP $sub_folder = "libarry"; $site_name = "<Website Original Name> Online Books Library 2015"; $site_title = "<Website Original Name> Read n Download Unlimited Books Online"; $site_desc = "<Website Original Name> Read or Download Unlimited Free Books online on PDF, eBooks or ePub"; $sub_category = "category"; $cat_slug = "hXXp://".$_SERVER["SERVER_NAME"]."/".$sub_folder."/".$sub_category."/";$domain = $_SERVER["SERVER_NAME"]."/".$sub_folder;$site = "hXXp://".$_SERVER["SERVER_NAME"]."/".$sub_folder; $domain1 = str_replace("www.", "", $domain); $domain2 = str_replace("http://", "", $domain1); $domainx = str_replace("https://", "", $domain2); $domain_title = date("m-Y"); $target_dir = "./cache/"; $exten_sitemap = ".tar.gz"; $button_home = 0;$button_dis1 = 0; $button_dis2 = 0; $button_dis3 = 0;$button_dis4 = 0; $button_dis5 = 0;$button_single = 0;$google_master_tools = "<meta name='google-site-verification' content='sRUXfZlQbLp7pHG9TN7IBMlw9NBbfAeLlsmM4sFn5ec' /> "; $counter1 = str_replace(" ","","10660384"); $counter2 = str_replace(" ","","0a38ffb6"); ?>
When clicking on a product, it would direct you from hXXp://site[.]com/libarry to hXXp://site[.]com/asset due to the .htaccess rules in the libarry directory:
Options +FollowSymLinksOptions +Indexes<IfModule mod_rewrite.c> RewriteEngine on RewriteBase /libarry/ RewriteRule ^category/(.)$ hXXp://site[.]com/asset/category/$1 RewriteRule ^(.)/(.)/(.)/(.).jpg$ hXXp://ecx[.]images-amazon[.]com/images/I/$1.jpg RewriteRule ^(.)/(.)/(.).download ./images/button/download.png RewriteRule ^(.)/(.)/(.).more ./images/button/more.png RewriteRule ^download/(.)$ ./button.php?id=#budal#$1 RewriteRule ^read-online/(.)$ ./button.php?id=#budal#$1 RewriteRule ^find/(.)$ ./search.php RewriteRule ^dmca-notice/?$ ./dmca.php?=$1 RewriteRule ^privacy-policy/?$ ./privacy.php?=$1 RewriteRule ^contact-us/?$ ./contact.php?=$1RewriteRule ^faqs/?$ ./faq.php?=$1 RewriteRule ^disclaimers/?$ ./disclaimer.php?=$1 RewriteRule ^(.)/(.)/(.)/(.).html$ hXXp://site[.]com/asset/ RewriteRule ^([^/.]+)/?.xml$ ./sitemaps.php?id=$1 [L] </IfModule> ErrorDocument 404 hXXp://site[.]com/libarry
In hXXp://site[.]com/asset it gets content from http://www.goodreads.com/genres and http://books.4shopings.com, displaying the books and categories from those websites.
This sort of attack can heavily affect your SEO, so make sure that both libarry and asset folders (in this case specifically) have been removed along with any backdoors on the website. If you need some professional assistance to remediate it, let us know.