Exploitation Level: Very Easy / Remote
DREAD Score: 7.4
Vulnerability: Persistent Cross-site Scripting
Patched Version: 3.7.6
During a routine research audit for our Sucuri Firewall, we discovered an Unauthenticated Persistent Cross-Site Scripting (XSS) affecting 40,000+ users of the WP Product Review plugin.
Current State of the Vulnerability
Though this security bug was fixed in the 3.7.6 release, older versions can be exploited by an attacker without any account in the vulnerable site. We are not aware of any exploit attempts currently using this vulnerability.
Disclosure / Response Timeline:
- May 13, 2020: Initial contact.
- May 14, 2020: Patch is live.
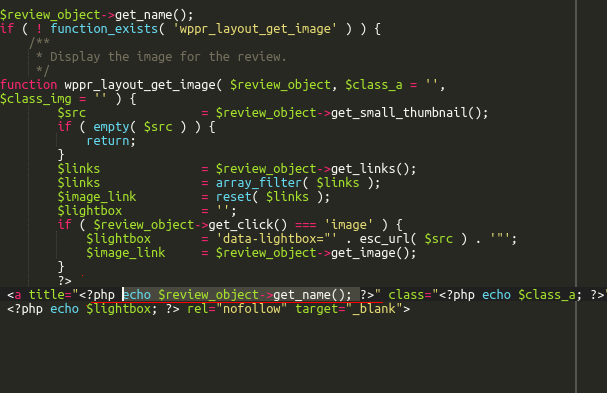
Technical Details
All user input data is sanitized but the WordPress function used can be bypassed when the parameter is set inside an HTML attribute. A successful attack results in malicious scripts being injected in all the site’s products.
Update as Soon as Possible
Unauthenticated attacks are very serious because they can be automated, making it easy for hackers to mount successful, widespread attacks against vulnerable websites. The number of active installs, the ease of exploitation, and the effects of a successful attack are what makes this vulnerability particularly dangerous.
To protect against this vulnerability, we strongly encourage WP Product Review users to update their plugin to version 3.7.6 as soon as possible. Users that are unable to update immediately can leverage the Sucuri Firewall or equivalent technology to virtually patch the vulnerability.

