There is often a misconception regarding the tools that attackers implement in their malicious activity, and that misconception is that they must be using advanced computer programs to target and exploit other computers.
This is not always true, and it is not uncommon to see simplistic tools used, such as the following:
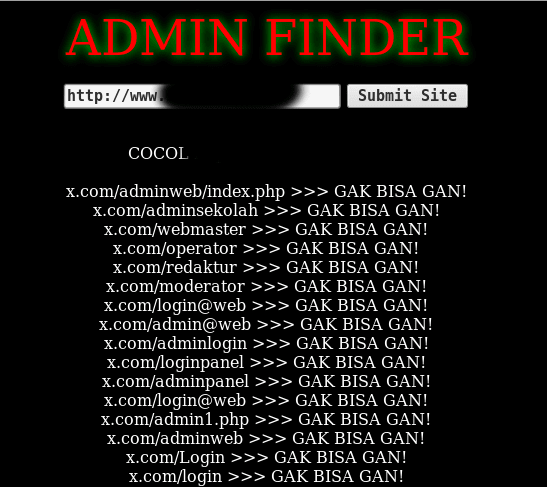
This tool uses simple PHP coding to create an array of segmented URLs that are then appended to the domain name that is provided by the malicious user. It's commonly known as an admin finder as noted by the web page title (hacker group name removed).
if (isset($_POST["submit_lol"])) {
$url = $_POST['hash_lol'];
echo "<br /> COCOL ".$url."<br /><br />";
$adminlocales = array("/adminweb/index.php", "/adminsekolah", "/webmaster", "/operator", "/redaktur", "/moderator", "/login@web", "/admin@web", "/adminlogin", "/loginpanel", "/adminpanel", "/login@web", "/admin1.php", "/adminweb", "/Login", "/login", "/redaktur", "/redakturweb", "/administrator", "/sika", "/develop", "/ketua", "/author", "/user", "/users", "/dinkesadmin", "/retel", "/panel", "/paneladmin", "/panellogin", "/redaksi", "/cp-admin", "/master", "/master/index.php", "/master/login.php", "/operator/index.php", "/sika/index.php", "/develop/index.php", "/ketua/index.php", "/redaktur/index.php", "/admin/index.php", "/administrator/index.php", "/adminweb/index.php", "/user/index.php", "/users/index.php", "/dinkesadmin/index.php", "/retel/index.php", "/author/index.php", "/panel/index.php", "/paneladmin/index.php", "/panellogin/index.php", "/redaksi/index.php", "/cp-admin/index.php", "/operator/login.php", "/sika/login.php", "/develop/login.php", "/ketua/login.php", "/redaktur/login.php", "/admin/login.php", "/administrator/login.php", "/adminweb/login.php");
foreach ($adminlocales as $admin){
$headers = get_headers("$url$admin");
if (eregi('200', $headers[0])) {
echo "<a href='$url$admin'>$url$admin</a> >>> KETEMU GAN!<br />";
}
else {
echo "$url$admin >>> GAK BISA GAN!<br />";
}
}
}
The coding behind the tool itself is almost as simple as the web page it displays. It just captures the domain name through a POST request sent via HTML form, assigns it to the $url variable, then uses a pre-set array of common admin segmented URLs through the $adminlocales variable, and combines the two to complete a full URL. Afterwards, it sends a request and if the request comes back with a valid HTTP "200 OK" code, then it outputs the URL with the Indonesian text "KETEMU GAN!" (I couldn't find an accurate translation, but I assume it's "URL GOOD"). If the web server returns anything other than "200 OK", then it outputs the "GAK BISA GAN!" text.
From there, attackers may use the results of the tool to gain access to administrator interfaces through brute force attempts.
All things considered, it's a very unsophisticated tool and could be much more efficient if run from a terminal with a proxy connection versus a compromised web server.